Access control vs authentication
Shows you how authentication . Access Control Policy. Types of Security Access Controls.
What is access control?
access control - Access control is a security technique that regulates who or what can view or use resources in a computing environment.
Authentication strength
1X standard and is widely used to ensure that only authorized devices and users can connect to a network. If you have requirements such as You would like apply separate policies for users and third party Loading. With these two forms of authentication, Azure RBAC, Azure ABAC, and ACLs have no effect.Authorization is the third step of access control.Access control is managed through several components: 1. Authors: Sirapat Boonkrong.
What Is Identity Management and Access Control?
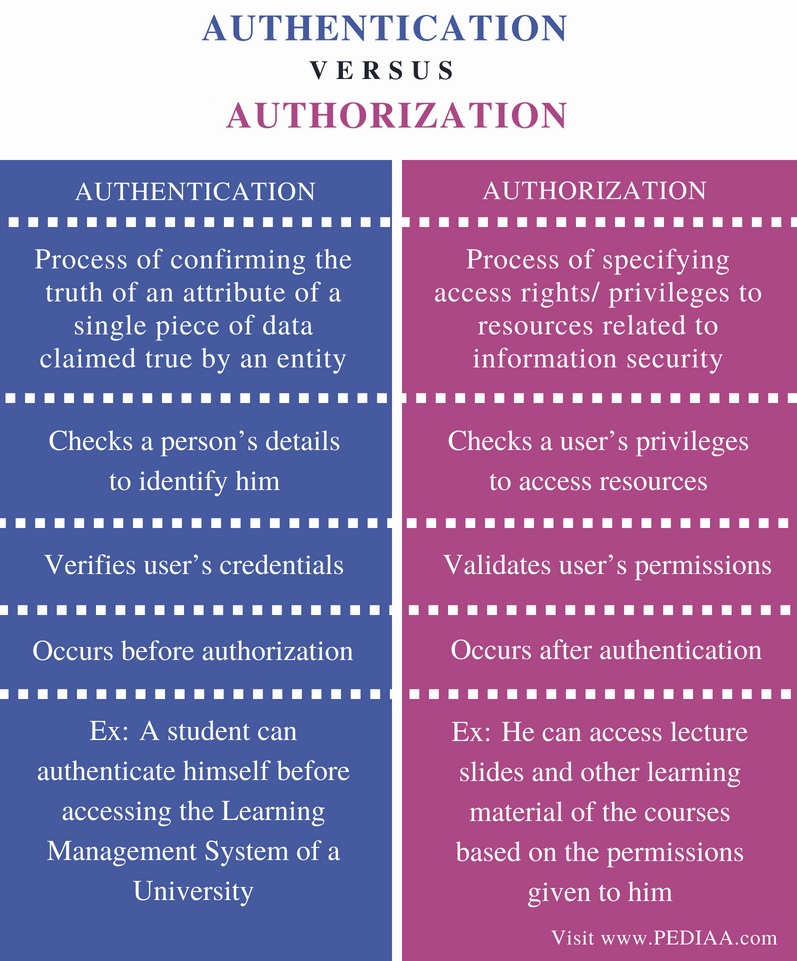
This can involve various .When you enter a username and password, use a PIN, scan your fingerprint, or tap your bank card, your identity is being verified for authentication purposes. In other words, it involves making sure who they really are.Authentication: The primary function of access control is authentication, which verifies the identity of users or entities attempting to gain access. Access Control Authentication Data and Information Security.Authentication vs Authorization Authentication is the process of verifying the identity of a user or client.Authentication is verifying the true identity of a user or entity, while authorization determines what a user can access and ensures that a user or entity receives the right access or permissions in a system. Authentication and authorization are two critical concepts in access control, used in . They are essential components of any system or web application, which determine the security of a system.Authentication and authorization are crucial to access control in security. Authentication is the initial process of establishing the identity of a user.Access Controls. I believe that the TCG authentication system can be considered either role-based or identity-based. CA has been used for years for pay-TV services.
Broken Access Control Vulnerability: A Guide to Prevent Attacks
Access control.
Authentication forms the foundation of access control mechanisms. We run into it daily both in .
Access control vulnerabilities and privilege escalation
Data Lake Storage Gen2 supports the following authorization mechanisms: Shared Key and SAS authorization grants access to a user (or application) without requiring them to have an identity in Microsoft Entra ID.58: (Operator authentication — Levels 3 and 4) A cryptographic module shall employ identity-based authentication mechanisms to control access to the module. They play separate but equally essential roles in securing .Temps de Lecture Estimé: 4 minAccess control systems apply cybersecurity principles like authentication and authorization to ensure users are who they say they are and that they have the right to .
Security
Authentication and Access Control
Together, they form the foundation of access control and data security in the digital world.
Access control model in Azure Data Lake Storage Gen2
In other words, it involves ensuring that they are who they claim to be.Authentication is the crucial first step in the access control process, playing a vital role in verifying the identity of a user or entity seeking access to a system, application, or resource. This process significantly reduces the risk of data theft, sabotage, or other malicious activities.At a high level, access control is a selective restriction of access to data. Whereas authorization policies define what an individual identity or group may access, access controls – also called permissions or privileges . It is defined in the IEEE 802. In the context of web applications, access control is dependent on authentication and session management: Authentication confirms that the user is who they say they are. Although often used interchangeably, authentication and authorization are fundamentally different functions. Authorizationauth0.1X authentication is a network access control standard that provides a framework for securing and controlling access to a local area network (LAN) or a wireless LAN (WLAN). Because access control is typically based on .comRecommandé pour vous en fonction de ce qui est populaire • Avis What is access control? Access control is technology to secure your confidential data. A state of access control is said to be safe if no permission can be leaked to an unauthorized, or uninvited principal. Properly implemented authentication protocols prevent unauthorized individuals from entering secure systems, networks, or data repositories.
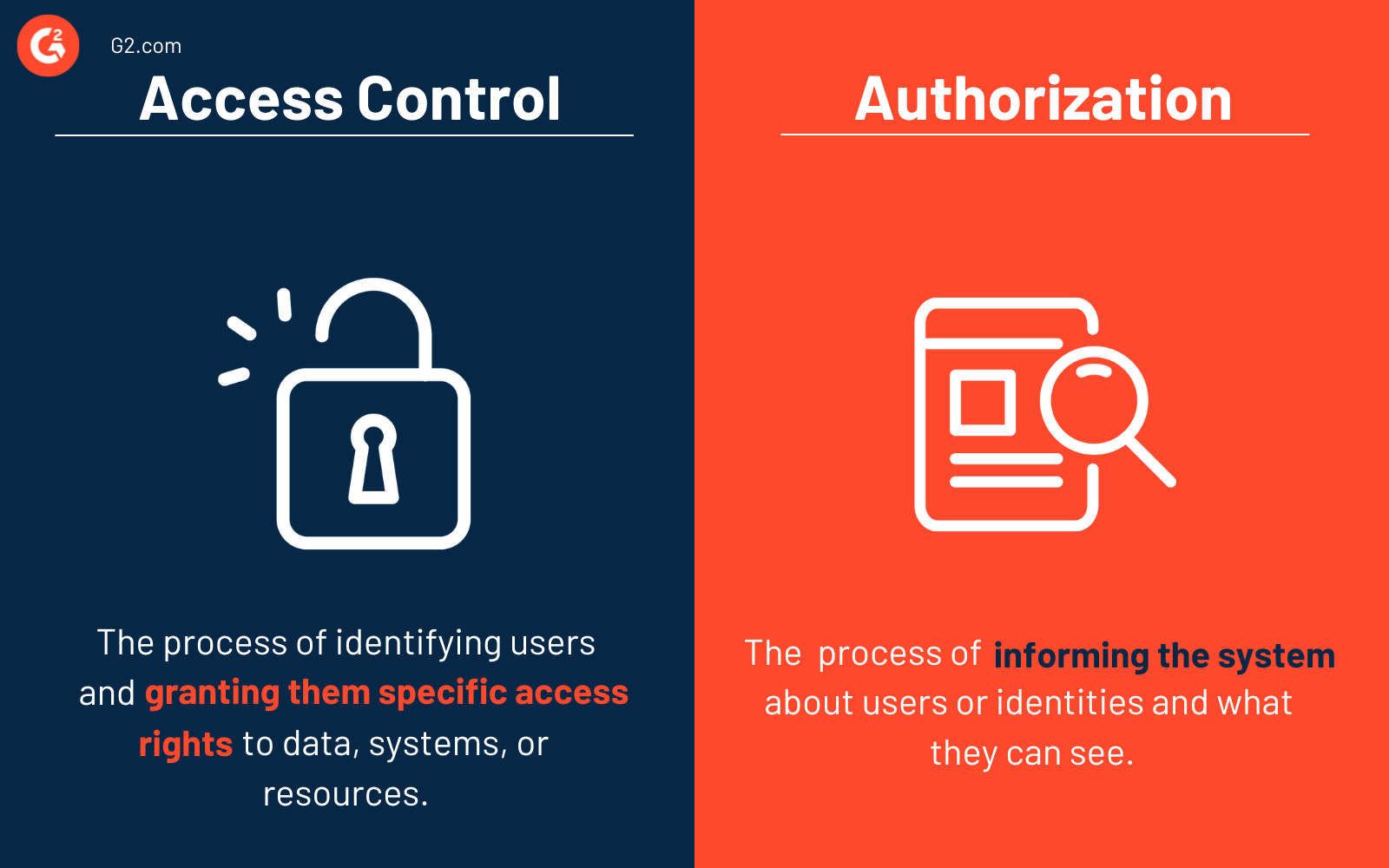
Enabling an authenticated user to sign in to the network with the correct credentials. Practical Cryptography Methods and Tools.Authentication and authorization work together to control access to protected resources.Access Control typically involves technologies like firewalls, authentication methods (e.In other words, access control consists of: Assigning users the appropriate permissions to access files and resources. Technology systems typically use some form of authentication to . Authentication establishes who you are, while authorization dictates what you are allowed to do once your identity is confirmed. Authentication is the process of verifying a user’s .
Similarly, confidentiality is really a manifestation of access control, specifically the ability to read data. There are numerous ATSC and DVB -compliant CA systems available for a broadcaster to choose from.January 19, 2022.

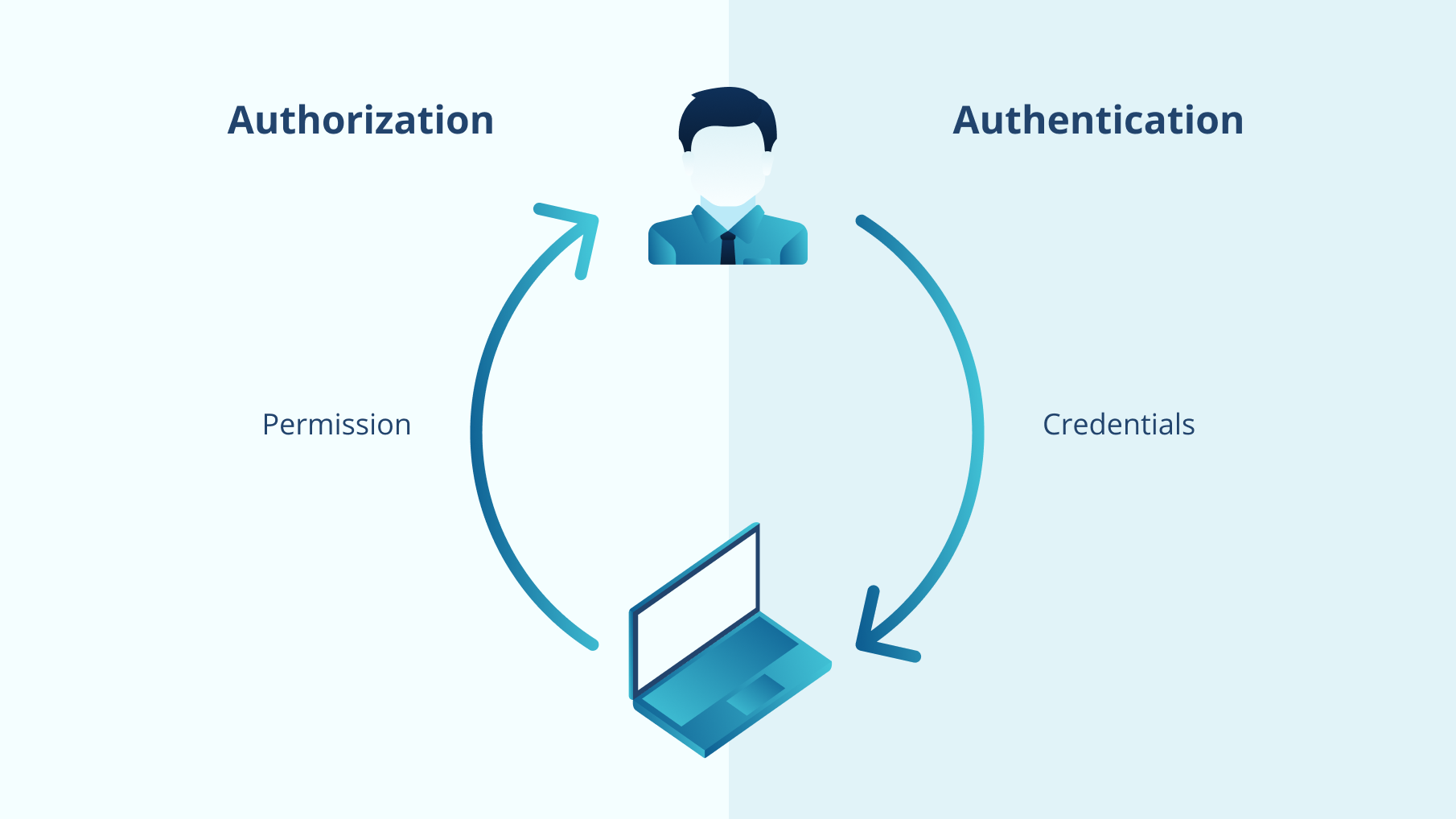
You cannot have a secure . To assure the safety of an access control system, it is essential to . Since, in computer security, confidentiality is often synonymous with encryption, it . Broken authentication refers to the failure of authentication systems to verify the identity of a user correctly. Authentication is any process by which a system verifies the identity of a user who wishes to access the system. Broken Access Control. The difference between authentication and access control lies in their respective roles in security management: Authentication is the process of verifying a user’s identity, typically through credentials like passwords, biometric scans, or security tokens, to ensure they are who they claim to be. The CA system provider provides .For example, access control decisions are generally enforced on the basis of a user-specific policy, and authentication is the way to establish the user in question. Authentication is a prerequisite to authorization. Its primary objective is to validate that the user is, in fact, the person they claim to be. Access control systems grants access to resources only to users whose identity has been proved and having the required permissions. When designing and developing software solutions, it is . For example, when a user .acceptable use policy (AUP) - An acceptable use policy (AUP) is a document stipulating constraints and practices that a user must agree to for access to a corporate network, the internet or other resources.Authentication (AuthN) is a process that verifies that someone or something is who they say they are.So, to sum it all up, authentication and authorization are distinct but complementary processes in digital security.Authentication.

Authentication and authorization are two critical concepts in access control, used in identity and access management (IAM).Authentication and Access Control.Authentication is the process of confirming the identity of a user, system, or entity attempting to access a resource.The paper: “ An Access Control Scheme for Big Data Processing ” provides a general purpose access control scheme for distributed BD processing clusters.We’re thrilled to announce a uthentication strength, a Conditional Access control that allows administrators to specify which authentication methods can be used to access a resource. So, if you are attempting Level 2 certification, call it role-based and then . Authorization is the process of verifying the user’s identity to provide an extra layer of security that the user is who they claim to be. Access control governs decisions and processes of determining, documenting and managing the subjects .
Broken Authentication vs. Session management identifies which subsequent HTTP .Authentication is the process of verifying the identity of a given user or client. Its aim is simple — to make sure the identity is who they say they are. Organizations can manage authentication in a variety of ways.
Authentication and access control news, help and research
(PDF) Authentication and Access Control - ResearchGateresearchgate.
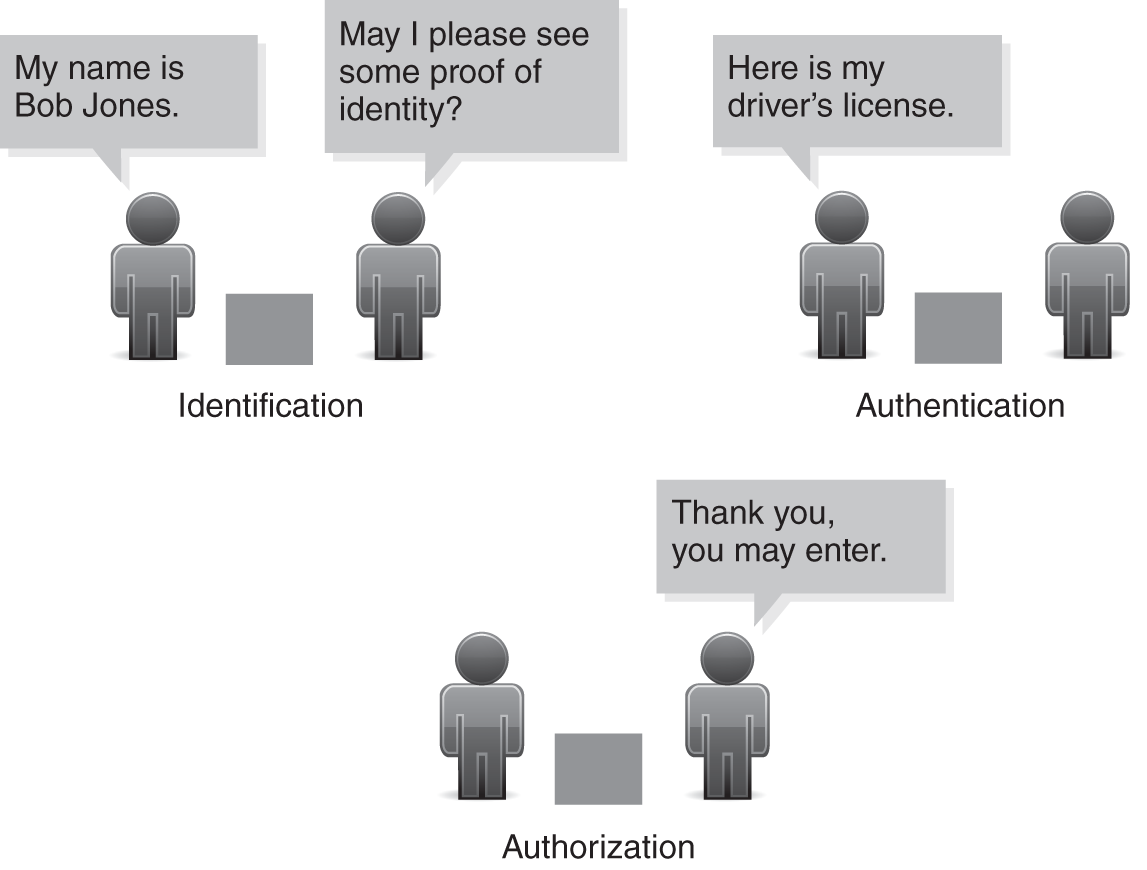
Identification, Authentication, Authorization
Conditional access (CA) is a technology used to control access to digital television ( DTV ) services to authorized users by encrypting the transmitted programming.
IP Address Access Control & Adaptive Authentication
At first glance, authentication and identity management sound as if they describe the same . They can require a name/password combination to . Authentication. In order to secure API authentication, workspace admins can control which users, service principals, and groups can create and use Azure Databricks . Authorization: Differences, Methods, and Techniques.Access control ensures that only identified, authenticated, and authorized users are able to access resources. Security requirements should be described clearly so that architects, designers, developers, and support teams can understand, and they can design and implement .orgAuthentication vs. ⚠️ Traditional PAM deployments have gaps. Broken authentication and broken access control are two distinct vulnerabilities that can occur in web applications.
Access Control Policy and Implementation Guides
Access control and Authorization mean the same thing. Skip to page content Skip to chat. Importance of . It consists of two main components: authentication and authorization, says Daniel Crowley, head of research for IBM . Role-Based Access Control (RBAC) Attribute-Based Access .netAccess Control: Identification, Authentication, and . On the other hand, authorization (or access control) is the process of verifying an entity’s identity.














