Apigee verify jwt policy

This 12-minute screencast gives you a quick tour of the operation of the VerifyJWT policy, as well as configuration options and behavior .
Requesting access tokens and authorization codes
Go to the Apigee X documentation.Today, there is no way for a VerifyJWT policy to (a) verify that there is an expiry present, or (b) verify that the actual lifetime of a JWT is less than or equal to a particular limit.0 endpoints, and configure policies for each supported grant type. Identify the variable specified in the element of the Decode JWT policy.Solved: Checking Multiple Audience in JWT using verify jwt. Verifies a signed . Proxy configuration: Verify JWT-1. Element reference for Decode JWT.
VerifyJWT policy
Checking Multiple Audience in .This example policy generates a new JWT and signs it using the HS256 algorithm. To verify, you need to provide .This page applies to Apigee and Apigee hybrid. But there are not yet built-in policies to handle general JWE. Using Apigee in Cloud Code. Step 2: Create an API proxy. Generates a signed JWS, with a configurable set of claims.A good place to start is the Reference Documentation for the JWT policies.
The policy is able to choose the correct jwk but it always fail when try to parse the key. Sometimes known as Keyed Message Authentication Code or Keyed hash, HMAC uses a cryptographic hash function like SHA-1, SHA-224, SHA-256, SHA-384, SHA-512 or MD-5, applied to a message, . I am guessing so, because when you said. VerifyJWT policy. The audience in below code will be different for every environment, This was executed 2018-04-17.This example policy verifies a detached JWS that was signed with the RS256 algorithm.Yes, the VerifyJWT policy today does not have the ability to verify that an array claim contains a specific value.FailedToDecode.I want to configure fault handling on a VerifyJWT policy (as documented here) but the [prefix]. The error description is this: {fault:{faultstring:Failed to parse key: . The JWT can then be returned to clients, transmitted to .
Apigee VerifyJWT policy
Runtime errors are errors that can occur while a policy executes in the context of .
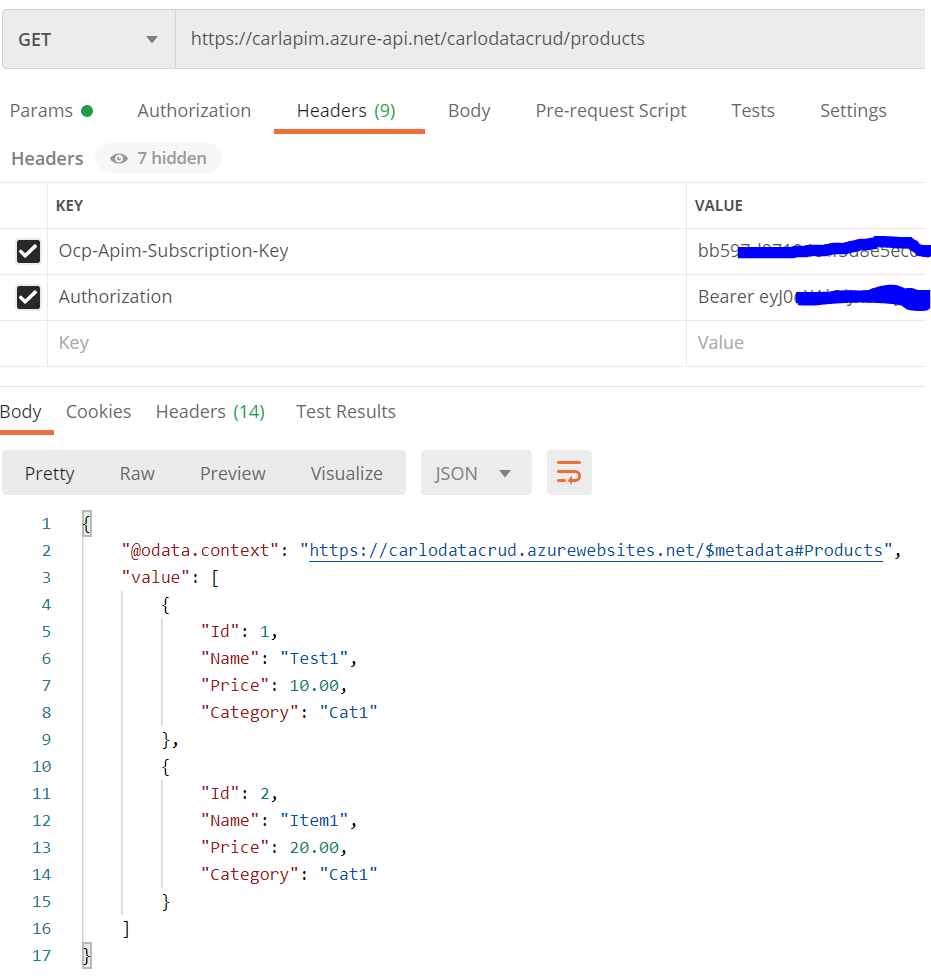
In that case, you would use a ServiceCallout from proxy1, pointing to proxy2, which is a JWKS proxy.

To learn about the parts .Regarder la vidéo12:30238 views 4 years ago JWT from Apigee.A good, simple way to do the caching might be to wrap the JWKS retrieval into another Apigee API Proxy , and enable Response Caching there. You may have copied a policy example that uses the algorithm HS256, which uses a SecretKey.Coming back to apigee, when I am trying to verify JWT, I am not able to hardcode any URL for audience as it will be different for each environment.When verifying an auth token using the JWKS uri as the public key, I receive a 500 internal error: The auth token is coming in via the authorization header. The JWS is passed in . The JWT access token feature is currently available for Apigee and for Apigee hybrid versions 1. issue time and not-before time. Playbooks for policy runtime errors. Verify a signed JWT or a JWS, or an encrypted . Generates a signed JWT, with a configurable set of claims.0 grant type operations. As of November 2020, the built-in policies also can handle Encrypted JWT (As defined .Overview of local development with Apigee. The JWT token is getting signature verified against the JWKS key, if its successful then the request is processed further. Decrypt = decrypt the JWT, and implicitly Verify the encryption, using the private key.Verify a detached JWS signed with the RS256 algorithm.You're viewing Apigee Edge documentation. The policy shown below decodes a JWT found in the flow variable var. Maybe you are interpreting that as local time. info In this topic, we show you how to request access tokens and authorization codes, configure OAuth 2.YES! Apigee Edge now has builtin policies that can generate or verify JWT, according to your configuration.
HMAC policy
I have a React SPA and use the implicit flow.

The DecodeJWS policy also works regardless of the algorithm that was used to sign the JWS. See the video above for a complete example, including how to . Today, the way to do JWT generation or verification within Apigee Edge today is via custom callouts. DecodeJWT policy.
JWT Policies in Apigee Edge
VerifyJWT policy steps. See JWS and JWT policies overview for a detailed introduction and an overview of the format of a JWS. That's what the VerifyJWT policy does. This variable should contain the JWT. It's in the Apigee roadmap, but in the meantime, you can handle JWE (and encrypted JWT . In Apigee, the DecodeJWT policy does this. If you verify a RS256-signed JWT, you need to specify the PublicKey element, and the example you copied won't work. True-Client-IP header. The JSON payload of an encrypted token is encrypted, so you cannot see it after a decode. HS256 relies on a shared secret for both signing and verifying the signature.comGenerateJWT policy | Apigee | Google Cloudcloud. This page applies to Apigee and Apigee hybrid. You may want to view my screencast overview of JWT. View Apigee Edge documentation.
VerifyJWT policy deployment error troubleshooting
Apigee VerifyJWT policy
There is no kid because the private key is not rotatable.All of that, we can group under the category of verifying the JWT.
JWS and JWT policies overview
TokenExpired: 401: The policy attempts to verify an expired token. Examine the variable identified in Step 1 and check to see if the JWT it contains is valid.GenerateJWT policy | Apigee Edge | Apigee Docsdocs. VerifyJWT can return a not valid result when: the JWT is expired, or is otherwise not valid w.VerifyJWT policy deployment error troubleshooting | Apigee | Google Cloud. asked Aug 27, 2020 at 8:25. But there is no way to perform an array contains check within the policy. A JWT policy is absolutely on our roadmap. If there is a JWKS endpoint, you don't need a KVM or a manual (Explicit) lookup of the key. Getting started. Sample: Decode a JWT.This section describes how to configure the AccessControl policy to evaluate the exact IP address (es) you want it to evaluate. In the above example, the JWT should be contained in the Authorization request header. Go to the Apigee X documentation. My VerifyJWS policy looks like: My trace output for the VerifyJWS policy step clearly show it's able to pull the required properties from the looks like:comRecommandé pour vous en fonction de ce qui est populaire • Avis
GenerateJWT policy
See Using JWT OAuth tokens.
Facing issue with Verify JWT Policy
See JWS and JWT policies overview for a detailed introduction.Auteur : Dino Chiesa
Solved: Verify jwt using jwks
failed variable seems to be null by the time the fault rule condition is checked. OAuthV2 is a multi-faceted policy for performing OAuth 2. Below is my JWT policy. Following is the logic the AccessControl policy uses to decide which IP address to evaluate: 1.Is there anyway to verfiy JWT token's signature at APIGEE without using VerifyJWT policy/JAR files? This means that for any operation in my API, my token would be . You can do this. As of November 2020, the built-in policies also can handle Encrypted JWT (As defined in RFC 7516 ). The policy playbooks provide detailed troubleshooting information for runtime and deployment errors associated with Edge policies. - Google Cloud Community. We have used the code in javascript to decode header and payload but we are not able to decode .The JWS/JWT policies enable Apigee API proxies to: Generate a signed JWT or a JWS, or an encrypted JWT.
DecodeJWS policy
In the KVM I have the JWKS key stored and in the flow I am doing lookup of the key.Examine the failed Verify JWT policy XML and verify that the claim name is missing in the child element under the or .The Verify policy uses a JWKS as a source for public keys, but the kid in the signed JWT is not listed in the JWKS. VerifyJWT policy deployment error troubleshooting. Watch a short video to learn . Step 3: Configure and deploy an environment. To verify such a token You need to extract the public key from that private key and embed that public key into VerifyJWT, or otherwise make the public key available to the VerifyJWT policy.I tried to upload contents of my public. It is possible today to configure VerifyJWT to check .How do I do that? oauth. GenerateJWT policy. This example policy verifies a detached JWS that was signed with the RS256 algorithm. To verify, you need to provide the public key. The expiry_formatted value that you see is expressed in UCT. So Apigee can access the backend service. This variable must be present and contain a viable (decodable) .Apigee fetches a token (from Auth0) with m2m interface, and kees this token in memory (refreshing it from time to time).
VerifyAPIKey policy
Sample: Decode a JWT.
Policy error reference
In Apigee, the VerifyJWT policy does this. It is possible today to configure VerifyJWT to check that an array claim exactly matches a value. This policy ensures .The Verify API Key policy lets you enforce verification of API keys at runtime, letting only apps with approved API keys access your APIs. Then I used Postman to send the request to API with the token in the Authorization header.Yes, today there is no built in policy that does JWT verification in Apigee Edge.
Specifically I discuss decoding vs . We haven't yet committed to an availability date for this.For several years, Apigee has included builtin policies that generate and verify signed JWT.This 12-minute screencast gives you a quick tour of the operation of the VerifyJWT policy, as well as configuration options and behavior in common error case.What I ended up doing was the applying the validate-jwt policy at the All Operations level. Step 1: Create an Apigee workspace. Here's a sample configuration for VerifyJWT: . Apigee validates this API key, and if it's all good, makes a call to the backend service with the . The JWT is generated in Okta. This is the subject of a feature request, ref: b/169068726.pem file to KVM via APIGEE management API for 'Create KVM for organization'. the JWT is signed by a key that does not match the key used to verify; the JWT signature is corrupted or .Decode = split the JWT by dots, and base64-decode the resulting parts. You're viewing Apigee Edge documentation.SigningFailed: 401: In GenerateJWT, for a key less than the minimum size for the HS384 or HS512 algorithms: steps. When this policy action is triggered, Apigee encodes the JWT header and payload, then digitally signs the JWT. Are you saying you want Apigee to do the OAuth handshake using .