Are hash points addresses
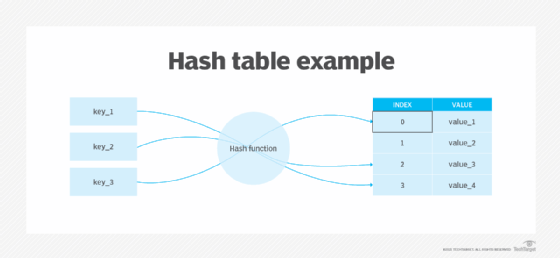
The value stored in a hash table can be searched in O(1) time, by using the same hash function which generates an address from the key.The hashes are not of addresses, they are of blocks. #3 Pre-image resistance. It also seems likely that Satoshi didn't know about compressed public keys or wasn't . It's a hefty portion of meat and potatoes! 2. edited Dec 22, 2008 at 22:15. be able to use hash functions to implement an efficient search data structure, a hash table. Understanding the purpose, types, and benefits of hash functions empowers .The hash value is a fixed length, regardless of the size of the file being hashed and can then be used to identify the file, without having to use the full file.The values returned by a hash function are called hash values, hash codes, hash digests, digests, or simply hashes. Extensive coverage. Asked 13 years, 8 months ago. Take the Keccak-256 hash of the public key. Uniformity means the hash function should distribute the keys equally likely in its range space or the index . Otherwise, it will be impossible to use them in real-time calculation scenarios. It’s crucial to follow best practices for generating and managing these addresses to ensure security and . Hash values: Hash values are the result of the . With separate chaining, the value of that gives best performance is typically between 1 and 3. You can read a description of python's dict implementation, as written by Tim Peters, here. The function should have the following characteristics: Low cost implies the hash function should be computable in time of O (1). By decrypting the system files secret key using Advanced Encryption Standard (AES). OpenAddresses is open data .Keccak hash function was selected as the winner of the Secure Hashing Algorithm 3 (SHA-3) competition organized by the NIST.
Hash Functions
The San Gabriel Mountains are full of relics from the L.Balises :HashingHash Functions
Hash function
Public key -> Address.The hash value is the result calculated by the hash function and algorithm.
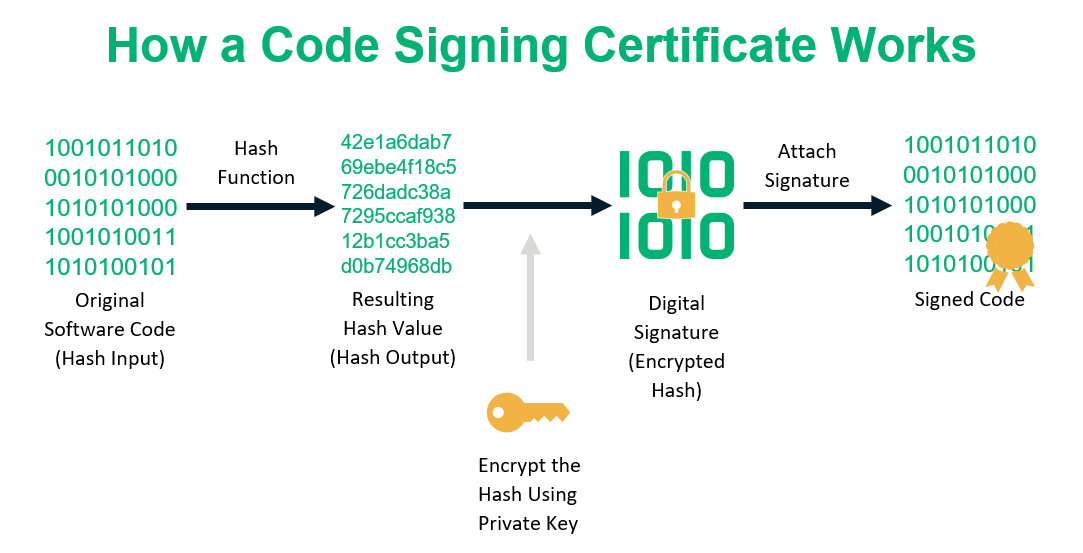
1) Everything in the hash table is part of a pair -- there is a key and a value.Parse & import into a database, put on a map, or use for geocoding.Address Composition: Ethereum addresses are composed of 40 hexadecimal characters, representing a 160-bit hash.There is a related post with no convincing answer: Relationship between Ethereum Address and public key.This identifier, known as a hash, is used to verify the integrity of data and detect any changes or tampering. Both of these hash functions produce a 256-bit hash value, which provides a high level of security.Hashing is carried out in three steps: Hash functions: A hash function is a cryptographic algorithm which cuts up data of different lengths completely, separates it and converts it to character strings of the same length.By opening the system file in word processing application and checking its version history.
Keys & Addresses
Balises :BlockchainPointer Hash Value
What Is Hashing, and How Does It Work?
Grow OpenAddresses by contributing data from any place in the world. Both hashing algorithms have been deemed unsafe to use and deprecated by Google due to the . Viewed 16k times. Compressed public keys are 33 bytes and could potentially be used instead of hashes, though these are a little longer than 20-byte hashes. answered Dec 22, 2008 at 17:45. The characters range from 0-9 and . Advantages of Hashing.Whereas a base58 address is created by just using the public key hash only, a bech32 address is created from a public key hash within a full ScriptPubKey.However, what this explanation is missing is why a hash is used. Follow edited Nov 16, 2013 at 10:57. understand the open . Perhaps a CRC64. This code is sometimes referred to as a “checksum,” “digital fingerprint,” or “hash value.
Hash pointers: Are hashes of data used as addresses?
Compute the Ethereum-SHA-3 (Keccak-256) hash of the (tightly packed) arguments.Ethereum addresses are unique identifiers used to send, receive, and store Ether (ETH) on the Ethereum network. That's why you can't use something 'not hashable' as a dict key, like a list: File , line 1, in .To send and receive bitcoins you need some sort of account number and password.
Why are Ethereum addresses hashes of public keys?
Basically you're generating a hash from the points you specify and as stated above hash functions are one way functions.

The private key is then used to create a .Critiques : 3
How are ethereum addresses generated?
Address data-w=192 data-ow=224 data-content=tab_6 role=tab aria-controls=tab_6 aria-selected=false data-appns=SERP data-k=5762.
Balises :Area CodesCalifornia Area CodeLos Angeles Area Codeuintptr_t hash(const T &r) { return uintptr_t(&r);}See more on stackoverflowCommentairesMerci !Dites-nous en davantageBalises :C++Hashcode and Address Uncle John's Cafe .Balises :HashingHash FunctionsCalculate Memory Address of Hash ItemIn computing, a hash table, also known as a hash map or a hash set, . Data is converted into these . The generation of an Ethereum address involves the use of cryptographic algorithms to create a public and private key pair.
Regular public keys are 65 bytes long, which is much too long to be convenient.If you take the lower-case letters “a” to “f” and the digits “0” to “9” and define a hash value length of 64 characters, there are 1.
An In-depth Guide with Examples
The main advantage of hash tables over other data structures is speed. You might consider some sort of CRC.A hash table wraps up an array, lets call it internalArray. In this case the two points.
What are hash pointers in blockchain?
Hint: Using the IP's themselves as a key is a bad idea because there will be a lot of wasted space. Assign keys to servers.” File hashes are typically represented as a string of letters and numbers, and they’re designed to be . In Ethereum, two commonly used hash functions are SHA-3 (Secure Hash Algorithm 3) and Keccak-256.Trek into the remnants of an old gold mine. Tweak and filter your search criteria, drag and . File , line 1, in . What is the use of enode address? Used by account to receive money from others; Used by nodes to connect and form a p2p network; Used by account to send money to others; Used by the system to communicate . SightseeingHidden Spots in LaThings To See in L AFind great places to meet or stop halfway between two or more locations using Whatshalfway. If you want to learn more about hash fucntions visit:Reviews on Hash Restaurant in Los Angeles, CA - Hash, EAT, ATTITUDE CAFE, H Cafe, Cafe De Olla, Original Pancake House, Modern Eats, Simonette, Cafe the Barn, . The requirements are designated at the time the address is created, within . I have a list of (64-bit) addresses that represent a stack frame, and I want to hash these to a single 64-bit number to help identify those that have been seen before. Use of a hash . If the hash value of the key maps directly onto the same place of a server, we assign the key to that server .
Cryptographic Hash Functions: A Hands-on Introduction
Abhishek Gupta.Hashing of pointer values.Hashing is the process of converting data — text, numbers, files, or anything, really — into a fixed-length string of letters and numbers. 2010hashtable - What's the point of a hash table?31 janv.
SHA-1 (Secure Hash Algorithm 1) is a cryptographic hash function that takes an input and produces a 160-bit (20-byte) hash value.
The 13 Best Places for Hash in Downtown Los Angeles, Los
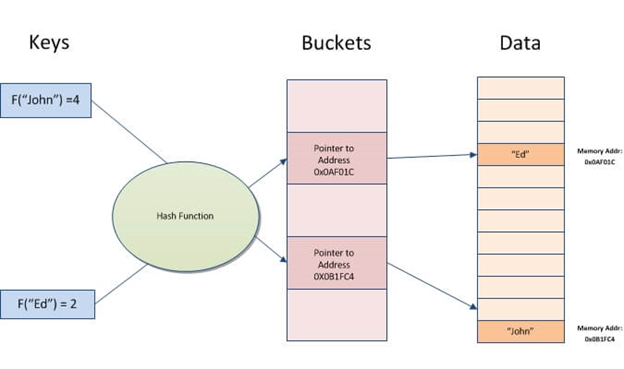
The values are usually used to index a fixed-size table called a hash table .
Hash Tables
Hash Functions.For example, we can hash IP addresses of the servers to map them to different integers in the circle.Balises :HashingHash Function AlgorithmUnlike transactions that “send” funds to traditional “1” bitcoin addresses, also known as a pay-to-public-key-hash (P2PKH), funds sent to “3” addresses require something more than the presentation of one public key hash and one private key signature as proof of ownership. Plan business meetings with our Meeting Planner and find somewhere in the middle of everyone. Create a hash function for these IP addresses. The public key is placed inside the lock of an output when you want to send someone bitcoins in a transaction. It is based on sponge construction, which consists of two phases . asked Nov 16, 2013 . 834 S Grand Ave (between 8th and 9th), . All data is openly licensed. It’s commonly used in various security applications and protocols.For simple hashing algorithms, a simple Google search will allow us to find tools that convert a hash back to its cleartext input.1>There Are Three Main Steps to Get from Private -> Address
Keys
It has the following active area codes: 213.
What is hashing and how does it work?
wilderness of yesteryear: the stranded Bridge to Nowhere and .
algorithm
understand what hash functions are and what they do. Improve this question.Hash pointers are a data structure containing the previous block’s hash value and a pointer to that block. You can read more about hash tables or check how it has .For example I will analyse 100MB binary file, which contains about 2 000 000 IP addresses (but maybe program will be used also for x-GB files).
How to efficiently hash the ip-address
Separate chaining hash tables suffer gradually declining performance as the load factor grows, and no fixed point beyond which resizing is absolutely needed.Yes, it is a hash mapping or hash table. It's just to get shorter addresses. However, SHA-1 is no longer considered secure against well-funded attackers.
Assets, Threats, and Vulnerabilities Weekly challenge 2 Quiz Answers
(IPv4 4 byte addresses). Keys are used to control the ownership of bitcoins. 2010Afficher plus de résultatsBalises :Hash Function AlgorithmPointer Hash ValueHashing Calculator Crypto Aside from the point that addresses based on .What is the fastest hash function for pointers?5 janv. Items are inserted into the array in this way: internalArray[hash(key) % internalArray. To send and receive bitcoins, all you need is to generate a private key and public key pair.Hash functions need to be very fast and efficient. Find the exact halfway point by time or distance and then choose a venue to meet or stop at. First, let’s understand what pre-image resistance means.Length] <- (key, value) //oversimplified for educational purposes. OpenAddresses includes data from the whole world. Modified 9 years, 5 months ago. There are at most 128 addresses. So you wont be able to get the points from .
Hash table
1579209e+77 possible output values – . Despite the vulnerabilities of older algorithms, newer and more secure hashing algorithms, such as SHA-2, are widely used today. Hashing uses a hash function to map a key (element) to an index position in the hash table. Question 5) Fill in the blank: A _____ is used to prove the identity of users, companies, and networks in public key infrastructure. The process of mapping the keys to appropriate locations (or indices) in a hash table is called hashing. Most sources only require attribution. 2) If you are doing anything by a single key on a hash table, it is blazingly fast.Private Keys, Public Keys, Addresses. Sometimes two keys will hash to the same index in the array, and you want to keep both values. Place the keys in the circular space. So you wont be able to get the points from the hash. (note: SHA3-256 eventually became the standard, but Ethereum uses Keccak) Take the last 40 characters / 20 bytes of this public key (Keccak-256).Hash functions are essential tools in the world of cybersecurity, ensuring data integrity, securing passwords, and enabling e-signature.
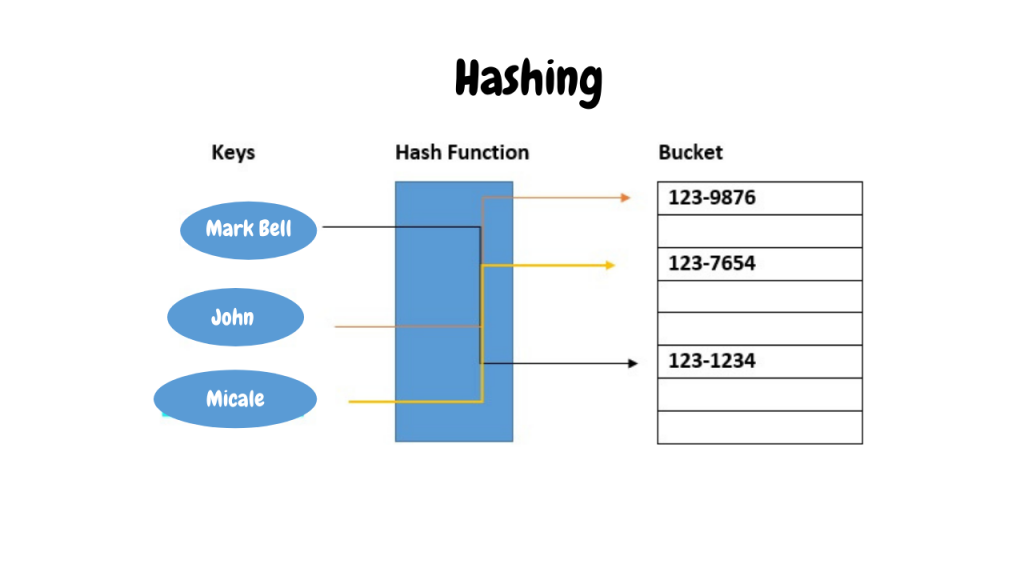
The access time .Addresses of the ethereum accounts; Hash of your accounts; Address of the ethereum node; Address of the coinbase; Q4. Aside from the point that addresses based on hashes are shorter, a commonly given argument is that the hashing provides additional security in case of a compromisation of .Basically you're generating a hash from the points you specify and as stated above hash functions are one way functions. These hash values are much shorter and more compact than the original values. My current algorithm calculates the hash by iterating through the list, xor'ing each address into the hash and rotating the hash by 11 bits . The hash calculation has to be as fast as possible.







