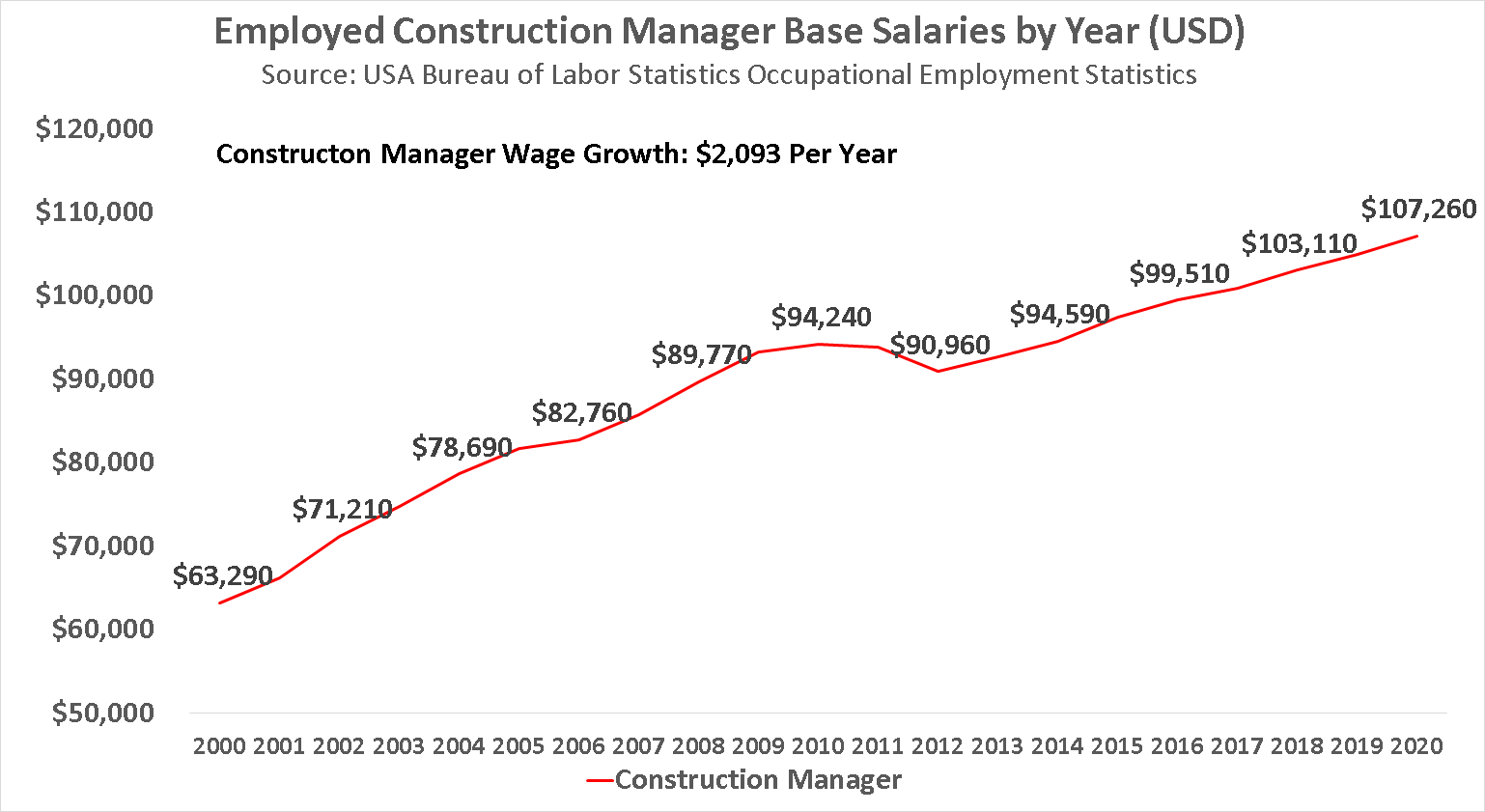
Audit logging and monitoring policy

Identify and validate the request. Event Log Requirements. How the data will be stored and collected.Audit log monitoring usually consists of the following steps: 1.3 Logging and Monitoring Policy 3.What are audit logs? When you use a technology service or product, audit logs are generated in response to every user action and response from the technology system.
Microsoft 365 audit log collection
Audit Log Review and Management Best Practices. The policy should also indicate who can access the logs and confirm that all team members are responsible for maintaining the logs’ integrity. The document's scope is . Logging and monitoring can be challenging to test, often involving interviews or asking if attacks were detected during a penetration test. In order to establish a baseline assessment of an organization's existing security posture, event logs need to be monitored and collected on a continuous basis.
Security log management and logging best practices
Audit policy defines rules about what events should be recorded and what data they should include.
Event Log Monitoring and Log Audit Software Basics
Functional Category: Computing & IT. Log Collection. Logs can be user based or component based, or both. To provide accurate and comprehensive audit logs to detect and react to inappropriate access to, or use of, . When an information security incident occurs, you need to be able to gather as much information about it as quickly as possible. Audit trails shall be used to support accountability by providing a trace of user actions.
Even if appropriate volumes of the correct data are being collected, it is .

ControlCase’s Audit Logging and Monitoring Policy Template will assist you in defining the activities necessary to deter and/or detect improper behavior, to foster user accountability, and to allow expedient systems event management.
Audit Logging and Monitoring Policy TEMPLATE V1
data addition, modification and deletion, data exports; Performance monitoring e.Application logging might also be used to record other types of events too such as: Security events; Business process monitoring e. Actions taken by any individual with root or administrative privileges.
Audit Logging and Monitoring
How to Build an Audit Logging and Monitoring Policy
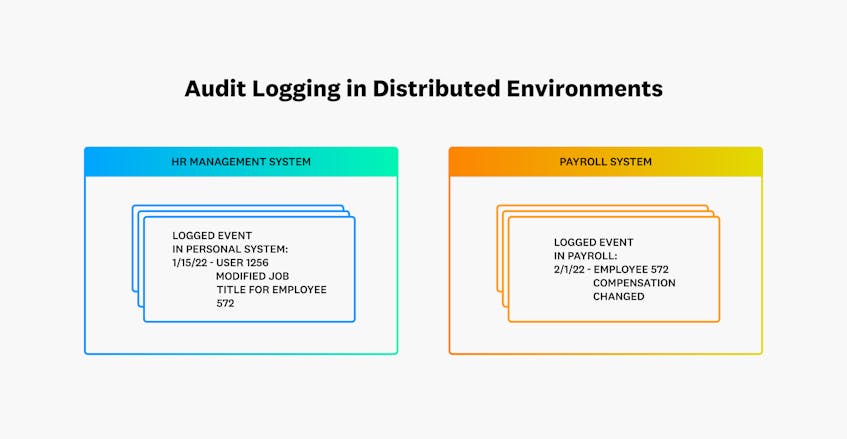
Protect the logs using a fail-safe configuration; When configuring an .Essentially, an organization’s security logging and monitoring policy should drive what is logged, how logs are transmitted, log rotation, retention, storage, etc. Intrusion Detection System (IDS) – the key is the letter “D” in this solution, in other words it detects intrusions .This Audit Logging and Monitoring Policy Template will ensure you in defining the activities necessary to deter and/or detect improper behavior, to foster user .
Audit Log Management Policy Template for CIS Control 8
The first step in event log monitoring is to decide: Which computers, software, devices and other systems to collect events from.
Audit and Logging Policy
Though these micro-actions behind audit logs are important in their own ways, the bigger purpose is greater.
NIST 800-53: Audit and Monitoring
Comply with information security legislation. These logs capture information .
Logging and protective monitoring
The audit logging feature increases the memory consumption of the API server because some context required for auditing is stored for each request.The purpose of this policy is to establish a consistent expectation of security logging and monitoring practices across the University of Wisconsin (UW) System to aid in the early .
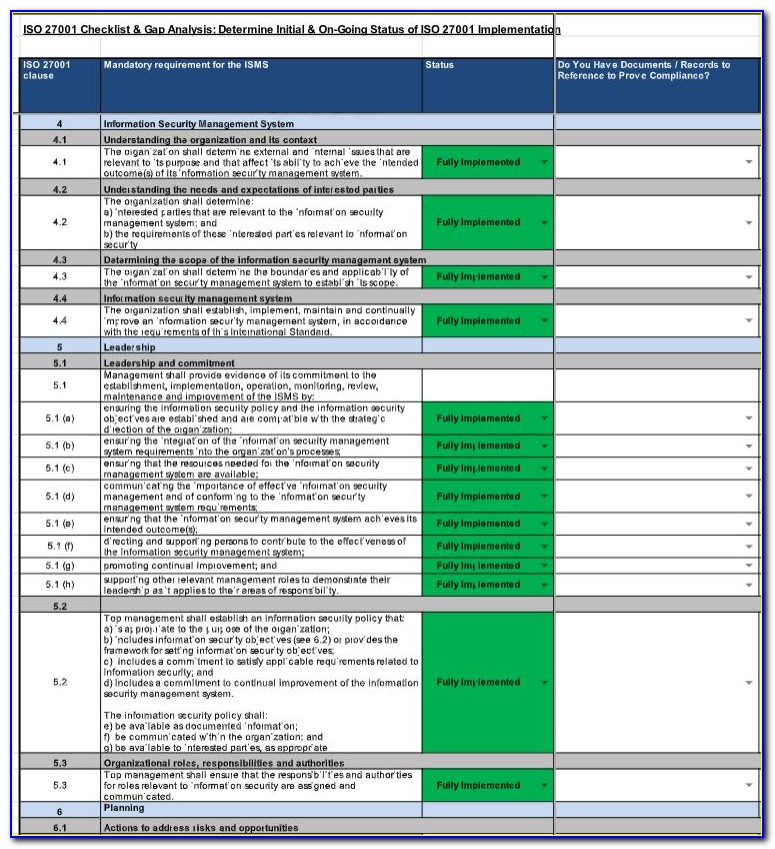
It provides practical, real-world guidance on developing, implementing, and maintaining effective log management practices throughout an enterprise. It is essential that an adequate level of logging and reporting is configured for the scope of the cloud-based service within the GC’s responsibility.
ISO 27001-ISMS Logging and Monitoring Policy Template
Individual Accountability. Audit logs record the occurrence of an event, the time at which .Policy Author/Contact: Cathy Singh.0 Event Logging and Monitoring Policy. Security logging and monitoring came from the Top 10 community survey (#3), up slightly from the tenth position in the OWASP Top 10 2017. This document provides guidance and requirements for the auditing, monitoring, and analysis of key information systems and networks in the SLAC computing environment.This sample policy is designed to help organizations define and comply with system audit logging and monitoring requirements.2 Scope All company employees and external party users. This Policy establishes the area within Brunel University London covering IS Audit and Event Logging and the Monitoring of . Perform relevant technology operations and processing.Windows 10, Windows 8, and Windows 7 Audit Settings Recommendations.1 – Audit logging – Audit logs recording user activities, exceptions and information systems security events must be produced and kept for an agreed period to assist in future investigations or access control monitoring in accordance with Regulation (EC) No 45/2001 on data protection. View Permission: SLAC-only. In previous versions of Windows, only Success is enabled by default.Log files provide a vitally important audit trail and can be used to monitor activity within the IT infrastructure, identify policy violations, pinpoint fraudulent or unusual activity and highlight security .docx), PDF File (.
Information Security: Logging and Monitoring
Exabeam SIEM and Solarwinds Log Event Manager have been deployed and are in operation. Audit trails shall be used to support after-the .Authenticate the user.Log collection and analysis is critical for an enterprise’s ability to detect malicious activity quickly. Beyond capturing the proper events, including the necessary info in a log entry, implementing log rules and ensuring log integrity, here are three other best practices to follow. About this document. Due to the scale at which Microsoft 365 operates, the collection and processing of audit logs must be strategically managed to ensure efficient and effective monitoring.You will have a topic specific policy, the ISO 27001 Logging and Monitoring Policy that sets out what you do for logging and monitoring. This article provides .
LOGGING AND MONITORING POLICY
What settings to use for each log, such as whether to use the default log size. This policy guides the .Audit logs serve an important role in maintaining, troubleshooting, and protecting both customer tenants and the internal Microsoft 365 infrastructure.

2 Event logs recording user access and actions . Last Updated: Thursday, January 28, 2021. Route the request to the right service node. The purpose of this document is to help all organizations improve their log management so they have the log data they need.
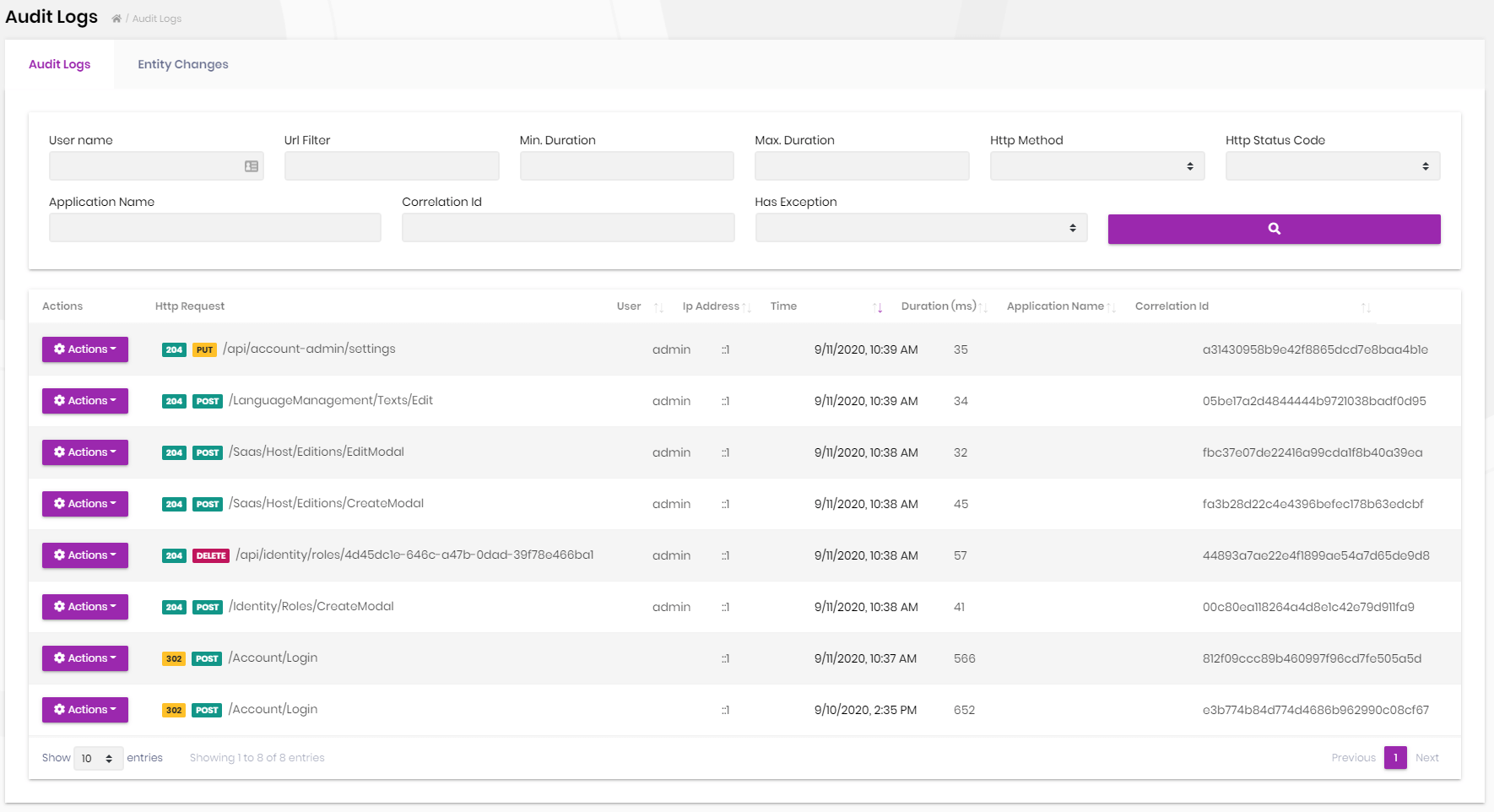
The idea behind collecting audit logs is two-fold: To identify errors and . Unfortunately, businesses at both PCI Level 1 and PCI Level 2 have no other choice.
Audit Logging and Monitoring
An audit logging and monitoring policy is a framework of guidelines and procedures that govern audit logging and monitoring processes. 1 Beginning with Windows 10 version 1809, Audit Logon is enabled by default for both Success and Failure.
The Importance of an Audit Logging & Monitoring Policy
Reconstruction of Events.An Audit Logging & Monitoring Policy is a critical component of an organization's security framework, designed to ensure that all activities involving sensitive data and critical .In the navigation panel of the Google Cloud console, select Logging, and then select Logs Explorer : Go to Logs Explorer.1 Purpose of Document.
Audit Log Review and Management Best Practices
To display all audit logs, enter either of the following queries into the query-editor field, and then click Run query: logName:cloudaudit. Remember, logging is only the first step. Policy Author/Contact: Cathy Singh.1 Purpose The purpose of this policy is to address the identification and management of risk the of system-based security events by logging and monitoring systems. Memory consumption depends on the audit logging configuration. Applicability This policy . This article discusses generating, collecting, and analyzing security logs from services hosted on Azure.txt) or read online for free. Logs are basically ledgers, or a list of transactions that show what has occurred in the system. For information about the overall landscape for audit logging with Google Cloud, see Cloud . Sometimes audit records are the only evidence of a successful attack.Audit events are written to the Windows Security log.Audit Logging and Monitoring.Policy objective 5. To record events and gather evidence. PCI DSS enforces the requirements because it is one of the most critical PCI DSS controls required for PCI compliance and customer data security. within your Google Cloud resources. Windows Server 2016, Windows Server 2012 R2, Windows Server 2012, . Select an existing Google Cloud project, folder, or organization. sales process abandonment, transactions, connections; Anti-automation monitoring; Audit trails e. These logs capture important details such as when a certificate is requested, if a .NIST 800-53: Audit and Monitoring. Here are some concepts to be familiar with. This Audit Logging and Monitoring Policy Template will ensure you in defining the activities necessary to . It acts as your eyes and ears when detecting and recovering from security .The requirements listed above can be daunting for a company that needs an annual audit. Directorate/Department: Information Technology. Ideally, the best practice is to forward specific events to systems such as .
Guide to Computer Security Log Management
Invalid access attempts.
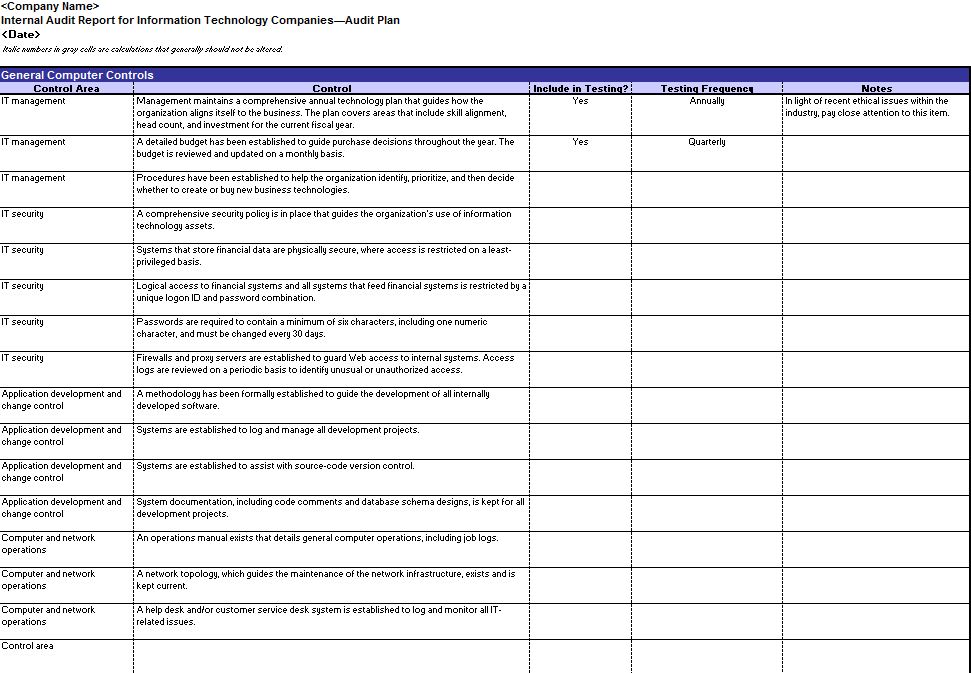
data load time, page timeouts
Log Management
Protection of logs.




.jpg?h=025b9db2&itok=4YClOxuB)