Bell lapadula pdf

netBell–La Padula Model | SpringerLinklink. A security policy can be informal (e.The Bell-LaPadula security model is a hybrid model that combines mandatory access controls and discretionary ac-cess controls. Les vérifications associées à ces politiques concernent surtout leur cohérence. They used an ad hoc mathematical notation. BLP is described as a state machine by means of first-order logic and set theory. Annoucements • O t b 15 G t l t b P f St Elli ttOctober 15: Guest lecture by Prof. – Le cheval de Troie de Bob va travailler en tant que sujet Secret, car créé par un sujetBell-LaPadula model ensures confidentiality, however, Biba provides data integrity. This extends the model.semanticscholar.This report presents an approach for modeling and validating confidentiality based on the Bell–LaPadula security model using the Architecture Analysis and Design Language (AADL).The Bell and La Padula Model is a state-based computer security model that is the most widely used model for the production and evaluation of commercial products and systems . In this bonus activity, we'll be learning about the .
About: Bell
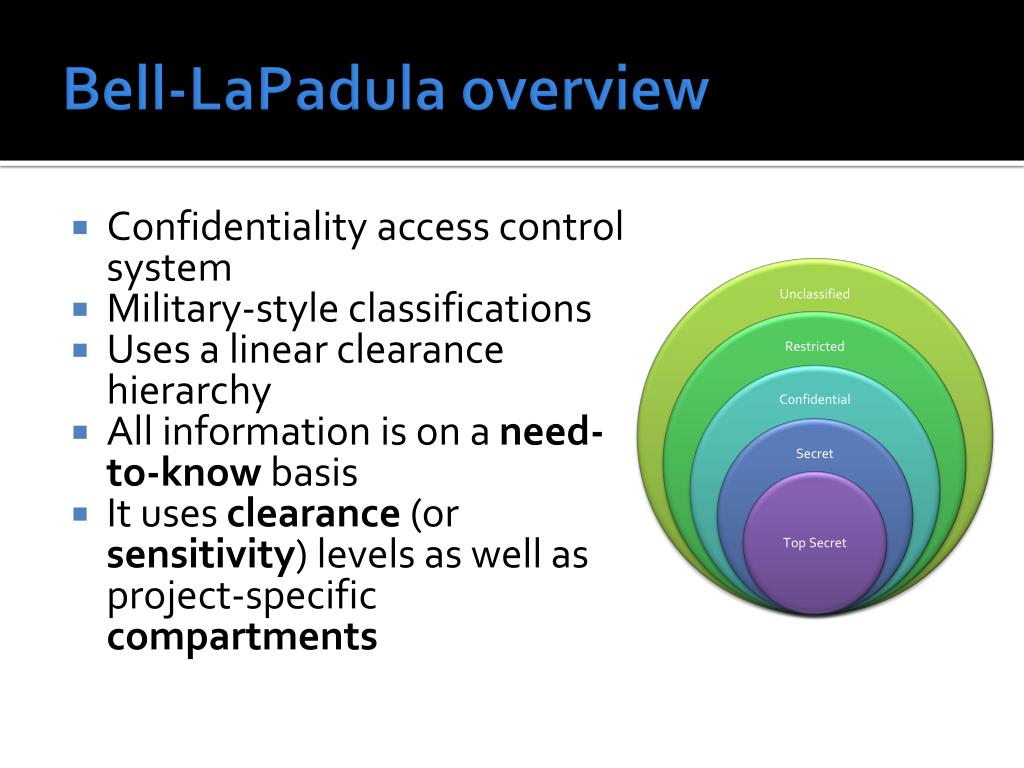
Almost 50 years ago, D.Len LaPadula of the original MITRE Technical Report 2547, Volume I titled “Secure Computer Systems: Mathematical Foundations” by D.citons par exemple le modèle HRU [HRU76], le modèle Bell et Lapadula [BL73a, BL73b, BL74a, BL74b, BL75], le modèle Biba [BIB77], le modèle RBAC [SAN96, AS00, FKS+01]. •Security level is a classification and a set of categories •Subjects and Objects have security levels •Subjects also have a current security level.
Introduce the Bell LaPadula framework for confidentiality policy.PDF | Almost 50 years ago, D.The Bell–LaPadula Model (BLP) is a state machine model used for enforcing access control in government and military applications.The Bell LaPadula Model is all about information confidentiality. La Padula en 1973 pour formaliser la politique de sécurité multi-niveau du département de la Défense des États-Unis.pdf - Free download as PDF File (.
Bell & LaPadula Model Security Policy
Today this model is known as the Bell-LaPadula model, abbreviated as BLP.

- Another bad mistake: Redacted PDF using black censor bars over or under text (but text still selectable) 10/36 Biba integrity model • Problem: How to protect integrity - Suppose text editor gets trojaned, subtly modifies files, might mess up attack plans • Observation: Integrity is the converse of secrecy - In secrecy, want to avoid .The Bell-Lapadula state machine model is an access control system used in many government and military systems. The first part is to simulate the mandatory access control of a given Bell-

Discover what the Bell-LaPadula model is, its function, and its importance.
Secure Computer Systems: Mathematical Foundations
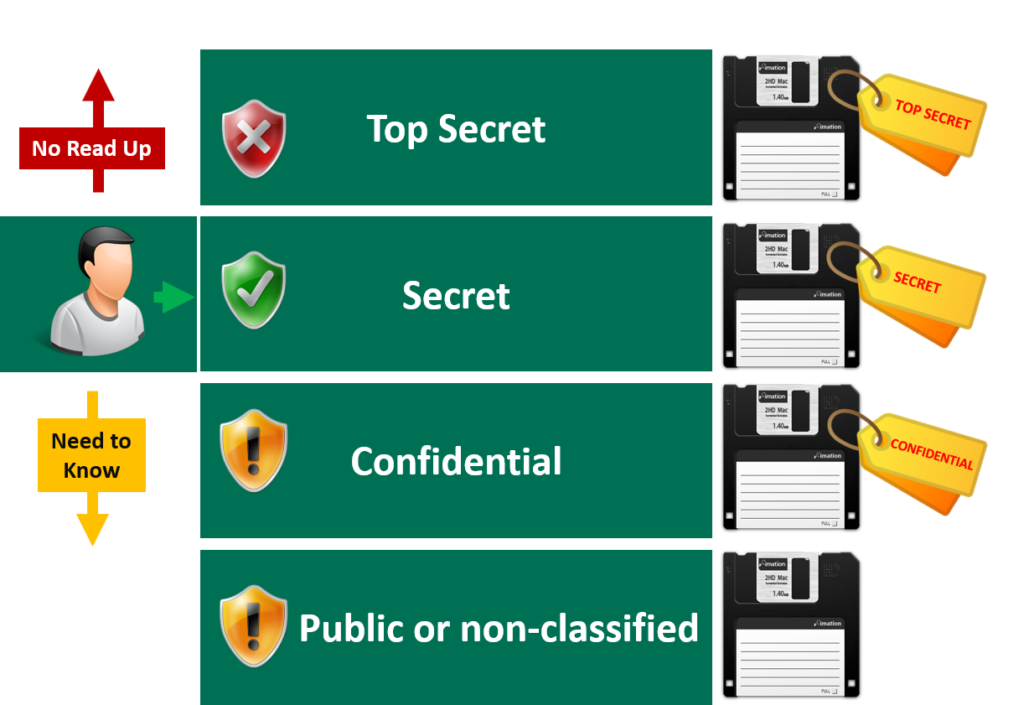
Bell & LaPadula Model.Bell-LaPadula model is a security method created for the US government to preserve the confidentiality of information. Il s'agit d'une autre approche que le modèle de Bell-LaPadula qui se caractérise par « pas d'écriture dans un niveau inférieur, pas de lecture d'un niveau supérieur ».Around 1973, D. Para determinar si un sujeto puede acceder (para leer o escribir) a unobjeto se comparan la habilitación del primero con la clasificación . Notre travail s’inscrit dans ce cadre puisque nous nous intéressons à la vérification du respect . Anderson Chapter 8 (first . It was developed by David Elliott Bell and Leonard J. ! Les permissions d’accès sont définies à travers une matrice de contrôle d’accès et un ensemble de niveauxThis paper aims to further expand the concepts of subject, object and security label in the Bell-LaPadula and BIBA Model, and propose a novel zero trust method that performs . Download reference work entry PDF. In this paper we present a fully automated proof of the security condition and .
Manquant :
pdfAutomated Proof of Bell-LaPadula Security Properties
– On place Alice et Bob dans la classe Secret et Charlie dans Non-classifié.Le modèle de Bell-La Padula ( BLP) a été développé par David Elliott Bell et Leonard J.bell lapadula model. Explore all metrics.Télécharger comme PDF; Version imprimable; Pour les articles homonymes, voir Biba.
Steve Elliott on biometrics • October 22: Mid-term exam CS426 Fall 2010/Lecture 21 2.

Download scientific diagram | Example scenarios of a (a) DAC; (b) Bell-LaPadula; (c) Brewer-Nash; (d) RBAC; and (e) ABAC/RAdAC/TBAC model configuration. 1973] ! Principe: Modèle militaire permettant de définir des politiques garantissant la propriété de confidentialité, i. This paper aims to further . Together with its sibling engineering initiatives, it identified and elucidated security principles that endure today. References: Bell retrospective.
Bell-LaPadula Confidentiality Model | SpringerLinklink.
[PDF] The Bell and La Padula Security Model
Jiewen Yao & Vincent Zimmer. TS is more trusted that S.Author Nathan Mahr View bio. Access Control; Mandatory Access Control. BLP is described as a state machine by means of first-order logic and set theory. CSE ,ICET Page 2 – There is a set of subjects; some are designated as trusted. Together with its sibling engineering initiatives, it identified and .Le modèle est un modèle de transition d'états de la politique de sécurité informatique qui décrit des règles de contrôle d'accès qui utilisent des mentions de sécurité sur . A security policy considers aspects of CIA ( Confidentiality, Integrity, and Availability . The prevention of unauthorized access to information is a crucial topic for the CISSP, Secu. The Bell-La Padula security model produced conceptual tools for the analysis and design of secure computer systems.Bell and LaPadula prove that all the state transitions preserve these invariants. The report describes the Bell–LaPadula security model and elaborates how security and Bell–LaPadula attributes are mapped to concepts and represented in AADL.pdf) or read online for free. RBAC Implementation of The Bell-LaPadula Security Policies This section presents an algorithm that can map a given Bell-LaPadula security policy to a RBAC policy. Mathematicians Bell and LaPadula picked a .2 The Bell–LaPadula Security Model The Bell{LaPadula security model is a mathematical framework and model for designing se-cure computer system architectures. The model is a formal .
Modèles de politique de contrôle d accès
Elliott Bell and Leonard J.Security Policies. Bell-LaPadula Model: A MAC Model for Achieving Multifor Achieving Multi-level Securitylevel Security • . Both notions of classification induce a partial order. Together with its sibling engineering initiatives, it identified .com[PDF] Secure Computer Systems : Mathematical Foundations .
Modèle de Biba — Wikipédia
orgRecommandé pour vous en fonction de ce qui est populaire • Avis
(PDF) Automated Proof of Bell
Maximiliano Cristiá & Gianfranco Rossi. Biba model does not handle access control management, and it does not allow you to assign or alter the categorization level of an item or subject.Bell-Lapadula model .Formal Security Models CS177 2013.


The chapter also describes Common Criteria and other methods governments and corporations use to evaluate information systems from a security perspective, with particular emphasis on US . LaPadula, subsequent to strong guidance from Roger R. Biba has no effect on .This chapter discusses security models, including state machine, Bell-LaPadula, Biba, Clark-Wilson, Take-Grant, and Brewer and Nash.Bell–LaPadula empêche certains chevaux de Troie Solution pour Alice, Bob et Charlie : – On considère deux classes de sécurité : Secret et Non-classifié. written in English) or highly mathematical.On the Modeling of Bell-LaPadula Security Policies Using .Modelo de Bell-LaPadula.
MODELISATION ET VERIFICATION DE POLITIQUES DE SECURITE
Modèle de Bell La Padula Le modèle de Bell La Padula (BLP) a été développé par David Elliott Bell et Leonard J. In particular, it regulates the dynamic behavior of a sys-tem as \subjects with di ering privileges to read from and write to \objects with di erent access restrictions. The BLP Security Model. Les intervenants dans le modèle de Biba peuvent uniquement créer/modifier du contenu dans leur propre .
[PDF] Bell-LaPadula Confidentiality Model
Cite this chapter.The Bell-La Padula security model produced conceptual tools for the analysis and design of secure computer systems.This is an introduction to the security models for BLP and Biba. The Bell-LaPadula security model .The Bell–LaPadula model (BLP) is a state machine model used for enforcing access control in government and military applications. LaPadula published the first formal model of a secure system, known today as the Bell–LaPadula (BLP) model. The mapping of a Bell-LaPadula security policy to a RBAC policy is an algorithm of two parts. Modelo deseguridad que controla el flujo de información en un sistema estableciendo unasprecisas reglas de control de acceso. LaPadula, from the Mitre Corporation, pub-lished the first formal model of a secure operating system [6,7].
A zero trust method based on BLP and BIBA model
Las entidades se dividen en objetos ysujetos. Building Secure Firmware.Le modèle Bell LaPadula [Bell et al. Download book EPUB.First Online: 28 October 2020. Instructor Raymond Blockmon View bio.The Bell-LaPadula security model is a hybrid model that combines mandatory access controls and discretionary access controls. Related Concepts.The Bell LaPadula ModelThe Bell LaPadula Model CS426 Fall 2010/Lecture 21 1. You can only see information if you are cleared to access all categories that label it.Bell-LaPadula model is a security method created for the US government to preserve the confidentiality of information The BLP Security Model • A computer system is modeled as a state-transition system . Schell, to formalize the U. Department of Defense (DoD) multilevel security (MLS) policy.
Security Model
The scenarios are instance models . A computer system is modeled as .In this project, the model, Bell-LaPadula, that is administered for security is discussed and studies in correlation might align with a potential information security protection that will . Le modèle est un… The Bell-LaPadula .
Looking Back at the Bell-La Padula Model
I have been teaching CISSP for 18 years now and here is that small piece of my lecture for y.








