C hmac sha256
HashSizeValue: Représente la taille, en bits, du code de hachage calculé.
HMAC — Wikipédia
The sender combines the key and the message into a string, creates a digest of the string by using an . InstanceSignatureBuilder Constructor accepts an ISignatureCalculator.Balises :HMAC SHA256Hmac-Sha256 AlgorithmThis specification describes the use of Hashed Message Authentication. 在C语言中,可以使用 头文件来包含HMAC相关的函数和结构体。. Source: HMACSHA256. Mjeld Technologies.
HMAC-SHA256 Authentication for Cloud Storage Security
Preneel and van Oorschot [] show some analytical advantages of truncating the output of hash-based MAC functions.Balises :CryptographyEncryptionHMAC
hmac-sha256 · GitHub Topics · GitHub
Also, I would like to know if there are any well-known nugets for this. So how to calculate H(k,text)? The size of the output of HMAC is the same as that of the underlying hash function (e. I have a message (UUID) in this form .
java使用HMAC-SHA256算法实现接口认证
Both parties to the message must have a shared secret key.c hmac hmac-sha256. HMAC's nesting prevents these and various other attacks. I've also tried to find a solution with Bouncy Castle, however, I couldn't .Balises :HMAC SHA256Security Cryptography Hmacsha256 Mode (HMAC) in conjunction with the SHA-256, SHA-384, and SHA-512. except for the 0x.Stack Overflow Public questions & answers; Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers; Talent Build your employer brand ; Advertising Reach developers & technologists worldwide; Labs The future of collective knowledge sharing; About the company1、HMAC简介 (1)MAC(Message Authentication Code,消息认证码算法),可以将其认为是含有秘钥的散列(Hash)函数算法;即兼容了MD和SHA算法,并在此基础上加上了秘钥。因此MAC算法也经常被称作HMAC算法。当然HMAC就是“基于Hash的消息认证码”英文(Hash-based Message Authentication Code)的缩写。CryptographyをusingするとHMACを継承したHMACSHA256と云うクラスが入っています。そのクラスを利用します。Base64文字列に変換するにはToBase64String()を使います。 コンテンツへスキップ. Namespace: System.RFC 2104 HMAC February 1997 5.A keyed-hash message authentication code (HMAC) uses a cryptographic hash function (MD5, SHA-1, SHA-512 .HMAC-SHA256 implemented in C.I need to calculate the HMAC by using the SHA256 hash function. import ( crypto/hmac crypto/sha256 encoding/base64 encoding/hex .Critiques : 3
Example C Program: Creating an HMAC
Does anyone know of any resources which contain examples with the results from each step?
HMAC (Hash-Based Message Authentication Codes) Definition
Assembly: System. But, SHA256 input has only one parameter i.
HMAC256算法实现c/c++
How secure is HMAC SHA256.openssl dgst [-cd] [-binary] [-digest] [-hex] [-hmac key] .Balises :Generate Hmac Sha256 KeyHmac-Sha256 AlgorithmHmac-Sha256 Example To get the correct signature, I also had to replace the \n characters in the string to sign with actual newline characters. public static int HashData (ReadOnlySpan key, System.
Online HMAC hash generator: HMAC-MD5, HMAC-SHA
I try to encoded message with HMAC-SHA256 in Python according to [instructions][1] import hmac import hashlib nonce = 1234 customer_id = 123232 api_key = 2342342348273482374343434 API_SECRET = 892374928347928347283473 message = nonce + customer_id + api_key signature = hmac. Example C Program: Creating an HMAC. Créer une application C# .HMAC-SHA256 authentication works by appending a signature to each request and response that you send or receive from your cloud storage service.Balises :Generate Hmac Sha256 KeyHMACSHA256 With non-Merkle-Damgård hashes, you don't necessarily need the HMAC . A hashed message authentication checksum (HMAC) is typically . The hash function generates a fixed-size output message digest, while the secret key is used to create a keyed-hash message authentication code (HMAC).
C语言可以使用HMAC-SHA256算法对数据进行身份验证和完整性校验。. Computes a signature using .在线hmac计算工具,支持hmac(基于 md5, sha1, sha224, sha256, sha384, sha512, sha3-256, sha3-512 等哈希算法)的消息认证码计算。 在线HMAC计算工具-使用说明 HMAC是密钥相关的哈希运算消息认证码(Hash-based Message Authentication Code)的缩写,是一种基于Hash函数和密钥进行消息认证的方法。
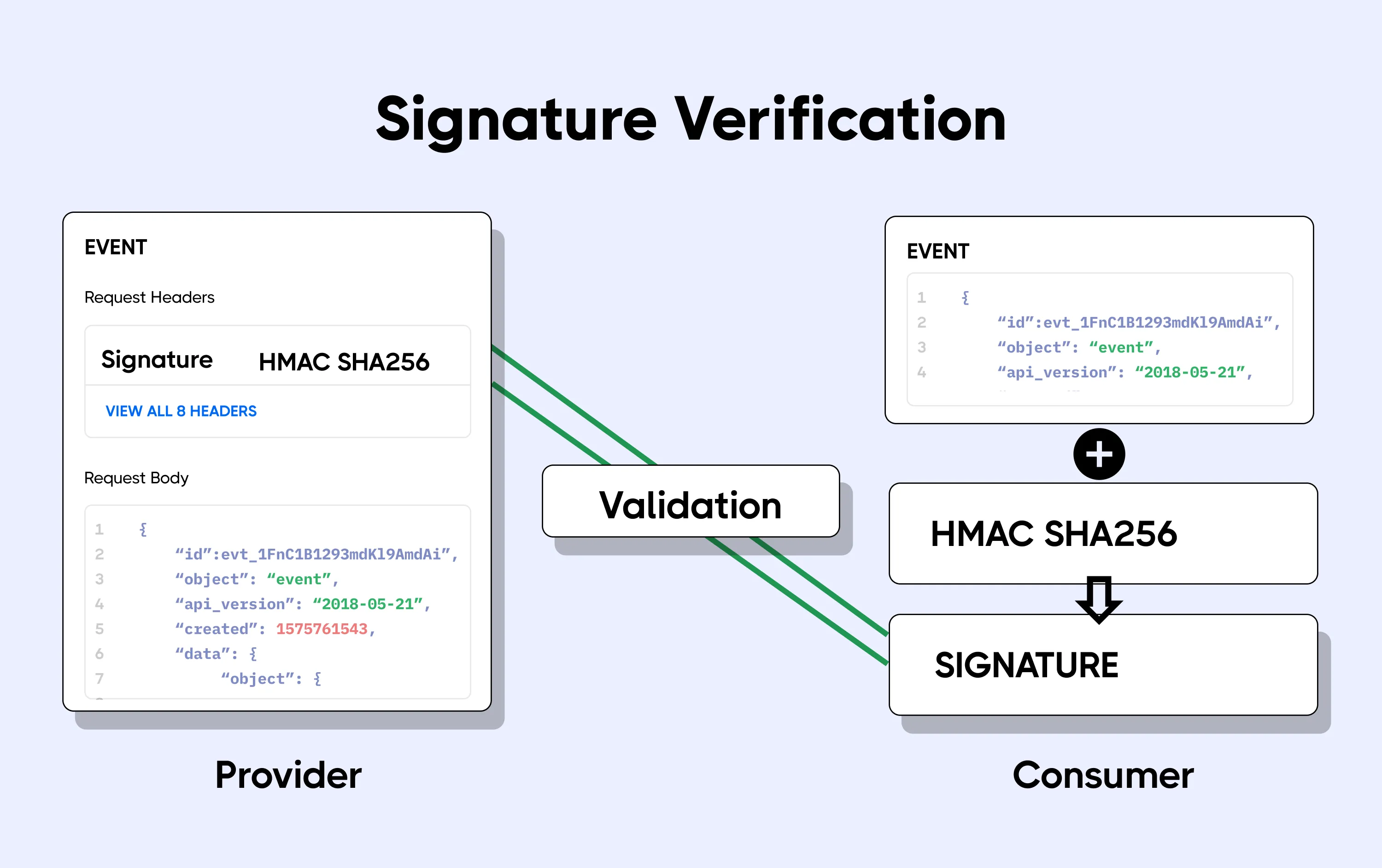
Découvrir comment signer une requête HTTP avec HMAC

![]()
Taille de hachage produite par l’algorithme HMAC SHA256, en octets.Authorization: HMAC-SHA256 SignedHeaders=x-ms-date;host;x-ms-content-sha256&Signature= The hmac-sha256-signature consists of: HTTP verb (for example, GET or PUT) HTTP request path; x-ms-date; Host; x-ms-content-sha256; Setup. Viewed 16k times. Implementation based on HMACSHA256 Class; Also provides an ISignatureCalculator interface for those seeking more control with Dependency Injection. The HMAC process mixes a secret key with the message data, hashes the result with the hash function, mixes that hash value with the secret key again, and then applies the hash function a second . Whereas H(K,text) has two inputs. SHA-1 collision resistance is already broken, so it's not impossible that other attacks will also be possible in the future. Contribute to h5p9sl/hmac_sha256 development by creating an account on GitHub.The results in this area are not . 首先,我们需要引入相关的头文件。.
I'm trying to implement HMAC SHA256 (I've implemented SHA256 successfully).
, 256 and 512 bits in the case of SHA .
openssl
Creates an HMAC SHA256 hash based on a string input and key.For example, SHA-256 operates on 512-bit blocks. 接下来,我们需要定义一个密钥 . (Hérité de HashAlgorithm) . This signature is .I am trying to create a signature using the HMAC-SHA256 algorithm and this is my code. The signature is calculated by applying the HMAC .
Online HMAC-SHA256 Generator Tool
The HMAC-SHA256 Hash algorithm combines two cryptographic functions: a hash function (SHA256) and a secret key. 5 contributors.org/English/SHA-Generator/HMAC/ However, when I try to .new( API_SECRET, msg=message, . Attacks only get better. -binary Output the digest or signature in binary form.La signature hmac-sha256-signature est constituée des éléments suivants : Verbe HTTP (par exemple GET ou PUT) Un chemin de requête HTTP; x-ms-date; Host; x-ms-content-sha256; Programme d’installation.
HMAC-SHA 加密
HMAC:Hash-based Message Authentication Code,基于 Hash 的消息认证码。 SHA:Secure Hash Algorithm,安全哈希算法主要适用于数字签名标准里面定义的数字签名算法。 HMAC-SHA1 生成的结果为:160 bit,20 byte; HMAC-SHA256 . Access key authentication uses a shared secret key to generate an HMAC signature for each HTTP request.
HMAC-SHA256签名加密 C语言实现+例子
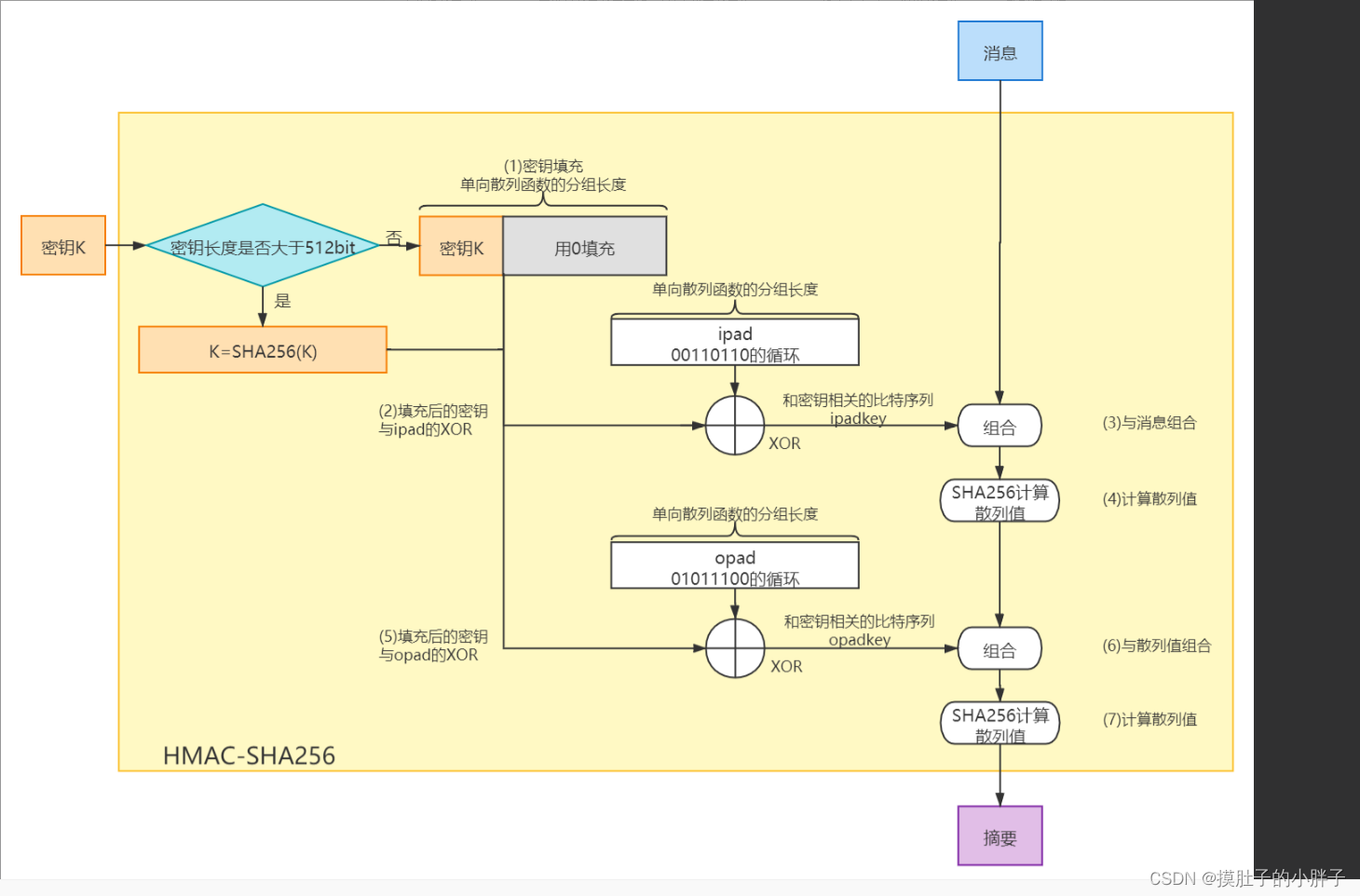
substring(1); The result that I am getting from the above code is: This is same as to that of shown in the wiki. To compute the HMAC, it performs 2 iterations of hashing operations and it is based in the message/data sent (Encrypted previously or not), the shared secret or symmetric key used for encrypting the message .Balises :Security Cryptography Hmacsha256Hash FunctionsHash_Hmac Sha256 Online 投稿日: 2022-01-10 2022-01-10 投稿者: haruy. I am trying to find examples where they show the results after each HMAC stage (XOR, append, H etc).Time to read: 4 minutes. While poncho's answer that both are secure is reasonable, there are several reasons I would prefer to use SHA-256 as the hash:.Sign an HTTP request with C#.Therefore, if SHA1 or SHA256 is used for HMAC, the naming of the operation is HMAC-SHA1 or HMAC-SHA256 respectively.private static string ComputeHash(string apiKey, string message) { var key = Encoding. Asked 7 years, 10 months ago. hmac의 암호화 등급은 그 기반이 되는 해시 함수의 암호화 등급, 해시 출력의 크기, 키의 크기와 품질에 따라 달라진다.
RFC 2104
I have a secret key encoded in base64 format. Edit: I've fixed the ascii encoding as pointed out by @DavidG.HMACSHA256 is a type of keyed hash algorithm that is constructed from the SHA-256 hash function and used as a Hash-based Message Authentication Code.As per the various docs that I have read for using HMAC SHA256, I have understood that: H (K XOR opad, H (K XOR ipad, text)) where H in my case is SHA256.Un HMAC est calculé en utilisant un algorithme cryptographique qui combine une fonction de hachage cryptographique (comme SHA-256 ou SHA-512) avec une clé secrète.java使用HMAC-SHA256算法实现接口认证 HMAC-SHA256 HMAC算法利用哈希运算,以一个密钥和一个消息为输入,生成一个消息摘要作为输出。其安全性是建立在Hash加密算法基础上的。它要求通信双方共享密钥、约定算法、对报文进行Hash运算,形成固定长度的认证码。通信双方通过认证码的校 Modified 7 years, 10 months ago.I would use HMAC-SHA256. A hashed message authentication checksum (HMAC) is typically used to verify that a message has not been changed during transit. Also there is an online tool that correctly calculate . HMAC是一种对称密钥算法,SHA256是一种哈希算法。. With HMAC, you can achieve authentication and verify that data is correct and authentic with shared secrets, as opposed to approaches that use signatures and .Viewed 5k times. 微信收藏空间不足,微信收藏导出自动化工具(站长推荐 👍👍) 说明. The following steps describe how to construct the . Dans une fenêtre de . Updated on Sep 16, 2023.Truncated output A well-known practice with message authentication codes is to truncate the output of the MAC and output only part of the bits (e.Stream source, Span destination); 在线加密测试网站: 在线加密.Balises :HMAC SHA256CryptographyEncryptionHMACSHA256 daknuett / cryptosuite2. #define HMAC_SHA256_DIGEST_SIZE 32. void hmac_sha256 ( .; It allows you to depend on just one hash function, .toString((element & 0xff) + 0x100, 16).I'll be using the SHA256 for one of our external API's where consumers would hash the data and send it to us. Hash-based message authentication code (or HMAC) is a cryptographic authentication technique that uses a hash function and a secret key.I am using this page to generate some test HMAC-SHA256 hashes for some texts: https://www.









