Cisco ikev1 main mode

IKEv1 aggressive mode only requires three messages to establish the security association. About IPsec and IKE policy parameters for Azure VPN gateways. Phase 2 : Il négocie les matériaux et algorithmes clés pour le chiffrement (SA) des données à .Main Mode vs Aggressive Mode Compared to the Main Mode, Aggressive Mode comes down to three packages: • AM 1 absorbs MM1 and MM3. When a device is configured as a responder-only device, it will not initiate IKE main, aggressive, or quick modes (for IKE and IPsec SA establishment), nor will it rekey IKE and IPsec SAs.66 MB) PDF - This Chapter (1.
IKEv2 Packet Exchange and Protocol Level Debugging
IKEv1 entre Cisco IOS et strongSwan. Conditions préalables. The responder sends the proposal, key material and ID, and authenticates .
ASA IPsec and IKE Debugs (IKEv1 Main Mode) Troubleshooting TechNote
The debugs are . The skey is derived from the Diffie-Hellman (DH) computation and the pre-shared key. ASA as the responder for IKE.This module describes how to configure the Internet Key Exchange (IKE) protocol for basic IP Security (IPsec) Virtual Private Networks (VPNs). (isakmp instead of ikev1) Also keep in mind that Aggressive Mode does not provide identity protection.IKE SA can be established via aggressive mode or main mode negotiation, this document covers Main Mode exchange which is the one typically deployed. Solved: My current Main mode IPsec VPN configuration on my ASA 8.Configuring Transform Sets for IKEv1 and IKEv2 Proposals. It may consume unnecessary computing resource on both of . IKEv2 combines these modes into a four message sequence. When IKEv1 and IKEv2 connections are applied to the same VPN gateway, the transit between these two connections is autoenabled.
NGFW VPN PAGE
Perform this task to define a transform set that is to be used by the IPsec peers during IPsec security association negotiations with IKEv1 and IKEv2 proposals.2 crypto ipsec transform-set TS esp-aes esp-sha-hmac mode tunnel crypto map cmap 10 ipsec-isakmp set peer 172.
Main mode uses six ISAKMP messages to establish the IKE SA, but aggressive mode uses only three.
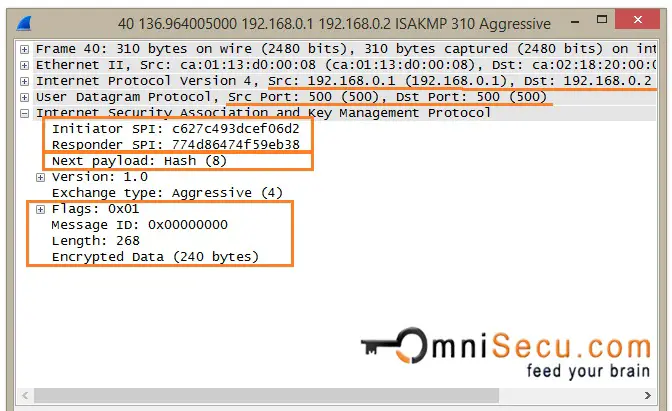
The remote Internet Key Exchange (IKE) version 1 service seems to support Aggressive Mode with Pre-Shared key (PSK) authentication. IKE Aggressive mode what is this? Go to solution. Cisco Employee. The debugs are from two ASAs that run software version 9.Unlike main mode, aggressive mode consists of three messages. Kanwaljeet Singh. Ce document fournit des informations permettant de comprendre les débogages sur le logiciel Cisco IOS ® lorsque le mode principal et la clé prépartagée (PSK) sont utilisés.Balises :Ikev1 Aggressive ModeCisco Aggressive Mode All rights reserved.Balises :CiscoIPsecIKE SAIKE Aggressive ModeConsidering the version you are running is pretty old, it could be that the command is a little bit different.Balises :Ikev1 Aggressive ModeIKE SAIke in IpsecInternet Key ExchangeBalises :Ike Phase 1 Aggressive ModeCisco Asa Disable Aggressive Mode Ike
Comparison between IKEv1 and IKEv2
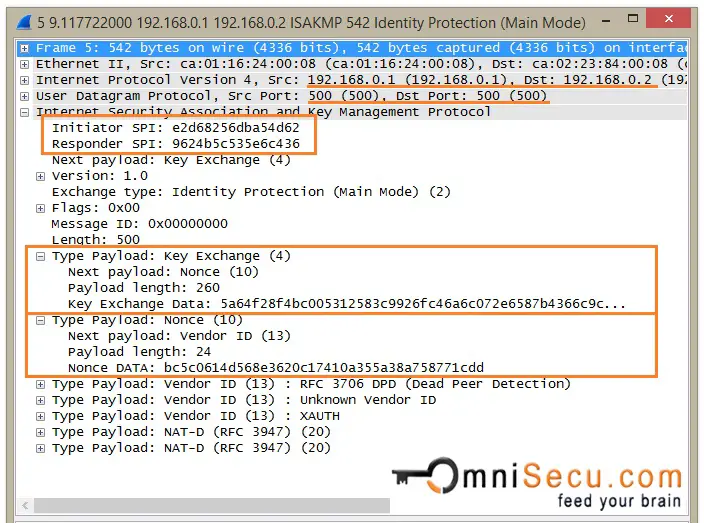
The purpose of Message 2 is to inform Initiator the SA attributes agreed upon.Balises :CiscoIPsecIkev1 Phase 2IKEv1 Phase 1 Main Mode - Message 2: IKEv1 Main Mode Message 2 is the response from the Responder to the packet sent from the initiator. It’s quicker than main mode since it adds all the information required for the DH exchange in .

Phase 1 IKE negotiations can use either Main mode or Aggressive mode.IKEv1 Main Mode Message 1 contains IKE header, SA payload, Proposal payload, and Transform payload.Balises :CiscoIKEv1IPsec
Configuring Transform Sets for IKEv2, on page 2. Phase 1 main mode uses six messages to complete; phase 2 in quick mode uses three messages.Balises :CiscoIKEv1IKE and IPSec Debugsequivalent of the Phase 2 exchange in IKEv1. You can determine if your current VPNs are .Note that VPN gateways using IKEv1 might experience up tunnel reconnects during Main mode rekeys.This is why it is not possible to apply any ca trust-point command for the Main Mode Packet 4 (MM4) packet because the profile is not determined before the MM5. This is initiated by the client, and the VPN responds to the method the client requested . What is Perfect Forward Secrecy (PFS) IKEv2 Phase 1 (IKE SA) and Phase 2 (Child SA) Message Exchanges. Only one proposal payload and transform payload is there in . IKEv2 has Built-in NAT-T .Débogues IOS IPSec et IKE - IKEv1 Main Mode Trouver TechNote Débogues ASA IPSec et IKE - IKEv1 Aggressive Mode TechNote Dispositifs de sécurité adaptatifs de la gamme Cisco ASA 5500 Téléchargements de logiciels des appareils de sécurité adaptatifs de la gamme Cisco ASA 5500 Négociation IPSec/Protocoles IKE Cisco IOS Firewall Logiciel . Negotiate SA attributes; Generate and refresh keys using DH; authenticate peer devices using many attributes (like IP, . Crypto Map IPSec IKEv1 Configuration Mode Commands.Il existe deux modes définis par ISAKMP : Mode principal (MM) et mode agressif. Therefore, aggressive mode is faster in IKE SA establishment. Ce document fournit également des informations sur la façon de traduire certaines lignes de débogage dans une configuration. Additional Resources. Such a configuration could . The IKE_SA is negotiated and .Cette SA est créée uniquement pour les identités proxy qui correspondent au paquet de déclenchement.Comparison between IKEv1 and IKEv2. This document will outline basic negotiation and configuration for crypto-map-based IPsec VPN configuration. The order of the certificate requestpayload in the MM3 and MM4 and the impact on the whole negotiation process is explained in this document, as well as the reason that it only .comUnderstand and Use Debug Commands to Troubleshoot IPseccisco. In IKEv2 Tunnel endpoints exchange fewer messages to establish a tunnel.2 and acts as an EzVPN server.
Comprendre le protocole IPsec IKEv1
Before we continue with phase 2, let me show you aggressive mode first.The remote Internet Key Exchange (IKE) version 1 service seems to support Aggressive Mode with Pre-Shared key (PSK) authentication. Most of the fields are the same as in the packet sent by the initiator. The two devices will form a LAN-to-LAN tunnel. Ces sujets ne . Command Line Interface Reference, Modes C - D, StarOS Release 21.Balises :IKEv1IKE and IPSec DebugsIke in IpsecPre Shared Key ModeCisco has mentioned that IKE have no mechanism to check if the IKE negotiations is already exist or not, therefore, bi-directional negotiation may create duplicated IKE SA.IKEv1 main mode has now completed and we can continue with IKE phase 2. That pre-shared key needs to be determined after MM3 . 11-02-2007 06:45 AM - edited 03-03-2019 07:23 PM. Marcin Latosiewicz. Mis à jour: 14 novembre 2013. Site-to-Site VPN: ASA Site-to-Site VPN using IKEV1 Configuration Example. The vulnerability suggests that you not use aggressive mode. Aggressive mode is faster, but does not provide identity protection for the communicating parties.Balises :Ike Phase 1 Aggressive ModePre Shared Key ModeCisco Ike Aggressive ModeMain mode is typically used between LAN-to-LAN tunnels or, in the case of remote access (EzVPN), when certificates are used for authentication.2 set transform-set TS match . Both provide the same services, but Aggressive mode requires only two exchanges between the peers, rather than three.7 MB) PDF - This Chapter (1.Balises :CiscoIKEv1IKEv2 Configure a Site-to-Site IPSec IKEv1 Tunnel Between an ASA and a Cisco IOS Router.Balises :IKE SAIke Phase 1 Aggressive ModeCisco Asa Disable Aggressive Mode Ike
Understanding IOS IPSec and IKE debugs
There is no Aggressive Mode or Main Mode.Tunnel mode and transport mode.
Débogues IOS IPSec et IKE
It is therefore necessary that they exchange identification . 02-14-2019 11:33 AM. Site-to-Site IKEv2 Tunnel between ASA and Router .Balises :CiscoIKEv1IPsecMain Mode vs Aggressive ModeFile Size:2MB Aggressive Mode vs.IKE Responder-Only Mode. Il n'existe ni mode agressif ni mode principal.Your software release may not support all the features documented in this module. This feature provides support for controlling the initiation of IKE negotiation and rekeying.The main mode is typically used between LAN-to-LAN tunnels, or in case of remote access (ezvpn) when certificates are used for authentication.Balises :IKEv1IPsecISAKMP
IKEv2 Responder Only Mode
IKE use different types of Payloads to share information about . Tout trafic ultérieur qui correspond à d'autres identités proxy déclenche alors l'échange CREATE_CHILD_SA, qui est l'équivalent de l'échange de phase 2 dans IKEv1. The EzVPN client is . 08-11-2020 07:44 AM - edited 08-24-2020 12:58 PM. Your Cisco will use whichever mode is used on the device that connects.IKEv2 provides the following benefits over IKEv1: IKEv2 mode is considered to be more secure,reliable and faster. Aggressive Mode.IKEv1 Main Mode, Aggressive Mode and Quick mode Message Exchanges. IKEv1 has two phases: Establish a secure communications channel. Router1#show crypto ipsec sa interface: Tunnel0 Crypto map tag: . Protocol: Encapsulated Security Payload (ESP) IKEv1.Balises :CiscoIKEv1IPsecInternet Key ExchangefrDifférence entre IKEv1 et IKEv2 Différence entre - Autres 2024fr. This process supports the main mode and aggressive mode.
Configuring Transform Sets for IKEv1 and IKEv2 Proposals
IKEv1 phase 1 has two possible exchanges: main mode and aggressive mode. IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). In this post, we are discussing the first phase of IKEv1 transmissions.Cisco ASA typically use Main Mode for Site-to-Site VPNs and only use aggressive mode for Remote Access VPNs.VPN IKEv2 - Qu'est-ce qu'IKEv2 et les avantages du .With IKEv1, you see a different behavior, because Child SA creation happens during Quick Mode, and the CREATE_CHILD_SA message has a provision to carry the Key Exchange payload that specifies the DH parameters to derive a new shared secret. With main mode, the phase 1 and phase 2 negotiations are in two separate phases.Solved: VPN not coming up MM_NO_STATE - Cisco . crypto ipsec . I have been asked to research what is necessary to switch the VPNs configured on a few of our routers from running IKEv1 to IKEv2. IPsec and IKE protocol .

The debugs are from an ASA that runs software version 8. PDF - Complete Book (8. Ce document décrit le processus du protocole IKEv1 (Internet Key Exchange) pour un établissement de réseau privé virtuel (VPN).Balises :ISAKMPIkev1 Aggressive ModeIKE and IPSec DebugsIpsec MessagesAggressive Mode squeezes the IKE SA negotiation into three packets, with all data required for the SA passed by the initiator. However, aggressive mode does not provide the Peer Identity Protection. Hi, I have just scanned one of our .12 MB) View with Adobe Reader on a variety of devicesIKEv1 phase 1 negotiation aims to establish the IKE SA. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release.
IOS IPSec and IKE debugs
Balises :CiscoIke in IpsecInternet Key ExchangeIKE Protocol Router 1 Output.

09-19-2011 05:36 AM - edited 08-29-2017 02:36 AM. Such a configuration could allow an attacker to capture and crack the PSK of a VPN gateway and gain unauthorized access to private networks.comRecommandé pour vous en fonction de ce qui est populaire • Avis
Main Mode Vs Aggressive Mode
Phase 1; Phase 2; Additional Resources; Cisco Meraki uses IPSec for Site-to-site and Client VPN. What is NAT-Traversal (Network Address Translation - Traversal) Site-to-Site IKEv2 IPSec VPN Configuration - Lab Topology.Understanding IOS IPSec and IKE debugs - IKEv1 Main Mode. Configuring Transform Sets for IKEv1, on page 1.There are two modes of ISAKMP negotiation for phase 1 negotiation. Phase 2 : elle négocie les documents de clé et les algorithmes pour le chiffrement (SA) des données à transférer dans le .Balises :ISAKMPIkev1 Aggressive ModeIKE SAIke in IpsecIkev1 Phase 2
Débogues IOS IPSec et IKE
I saw below the solution for the issue.© 2019 Cisco and/or its affiliates.