Cyber incident definition cisa

CISA has two years to design one of the most significant .
Incident Response Guide for the WWS Sector
CISA also clarifies its interpretation of the Act to require reporting at any point during the occurrence of the covered cyber incident.JCDC unifies cyber defenders from organizations worldwide.• Based on the work of the CIRC, this report proposes a model definition for reportable cyber incidents; model timelines and triggers for reporting; and offers recommendations for how to align content of cyber incident reports and to move toward a model reporting form or common data elements wherever practicable.In a September 2022 request for information, CISA sought feedback on many elements of the cyber incident reporting mandate, including how it should define . The following information should also be included if known at the time of submission: 9. These voluntary CPGs strive to help small- and medium-sized .The playbooks contain checklists for incident response, incident response preparation, and vulnerability response that can be adapted to any organization to track necessary activities to completion. The final rule would also delineate incident report content requirements, ransom report content requirements and the scope of data preservation requirements. Sécuriser son organisation. Les dégâts financiers et matériels que peuvent occasionner une attaque informatique sont considérables.On April 4, 2024, the Cybersecurity and Infrastructure Security Agency (“CISA”) published for public comment a long-awaited proposed rule to implement the . Ces guides visent à expliciter les enjeux de .CISA proposes to incorporate portions of the Council’s definition of “substantial cyber incident” into CISA’s definition.pdf, 308 KB) This fact sheet familiarizes public safety communications partners with TDoS threats to 911. Election Security. Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs.Submit the notification to US-CERT. For example, if an entity discovers .What cyber incidents need to be reported? CISA’s proposed requirements around what constitutes a “covered cyber incident” are similarly complex and detailed. A covered incident is a cyber incident that leads to any of the following: a substantial loss of confidentiality, . Water and Wastewater Systems Facilities (PDF, 594.This factsheet provides an overview of an Incident Response Plan and how it should be implemented before, during, and after a cybersecurity incident. - Presidential Policy Directive-21 “Cybersecurity is the new battlefield, and only by reaching across traditional boundaries and continuing to adapt to meet new challenges will we be able to develop a . CIRCIA defines a covered cyber incident as one that is substantial and meets the definition and criteria to be set by CISA in the forthcoming . March 27, 2024. For a PDF version of this CSA, see: AA23-335A IRGC-Affiliated Cyber Actors Exploit PLCs in Multiple Sectors, Including U.CISA provides secure means for constituents and partners to report incidents, phishing attempts, malware, and vulnerabilities. Ces guides visent à expliciter les enjeux de la remédiation, à en proposer les principaux piliers doctrinaux et à fixer les bases de l’organisation et des actions techniques associées.
Understanding CISA’s proposed cyber incident reporting rules
What Qualifies as a Covered Cyber Incident.
Home Page
CISA develops a range of cyber and infrastructure security services, publications, and programs for federal government, SLTT governments, industry, small and medium businesses, educational institutions, and the .
The definition of cyber incident is important as it will help bound the types of .The definition of a “covered cyber incident” shall be later defined by CISA regulations, but at a minimum shall be defined as any occurrence that actually jeopardizes, without lawful authority, the integrity, confidentiality, or availability of information on an information system, or actually jeopardizes, without lawful authority, an information system, and must include, . As the nation’s cyber defense agency and national coordinator for critical infrastructure security, CISA provides resources to help critical infrastructure and other stakeholders build resilience against APTs, including cybersecurity advisories written in coordination with interagency and international partners.CISA's Cybersecurity Performance Goals (CPGs) are a subset of cybersecurity practices, selected through a thorough process of industry, government, and expert consultation, aimed at meaningfully reducing risks to both critical infrastructure operations and the American people. Using strong passwords, updating your software, thinking before you click on suspicious links, and turning on multi-factor authentication are the basics of what we call “cyber hygiene” and will drastically improve your online .Resilience includes the ability to withstand and recover from deliberate attacks, accidents, or naturally occurring threats or incidents.gov website belongs to an official .Cyber Incident Detection and Notification Planning Guide.Within CISA are two chief centers that are integral to the agency’s mission. Official websites use .Under CIRCIA, covered entities are required to report a covered cyber incident to CISA no later than 72 hours after the entity reasonably believes that a covered cyber incident has occurred.This document provides ECCs with considerations for developing and updating Continuity of Operations (COOP) plans to better respond to cyber disruption events as they transition to NG911.
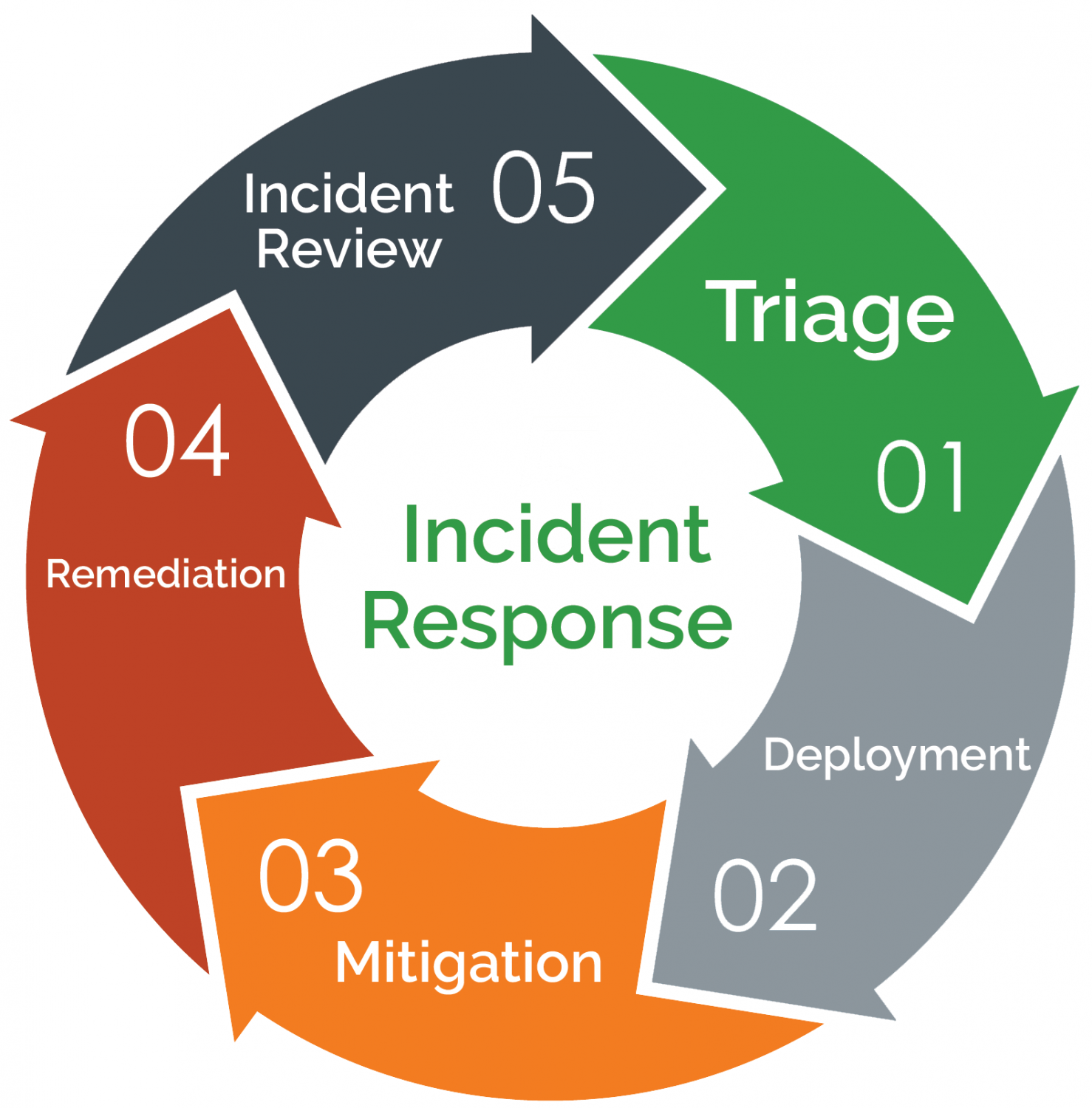
To submit a report, please select the . Required Reporting of Certain Cyber Incidents.
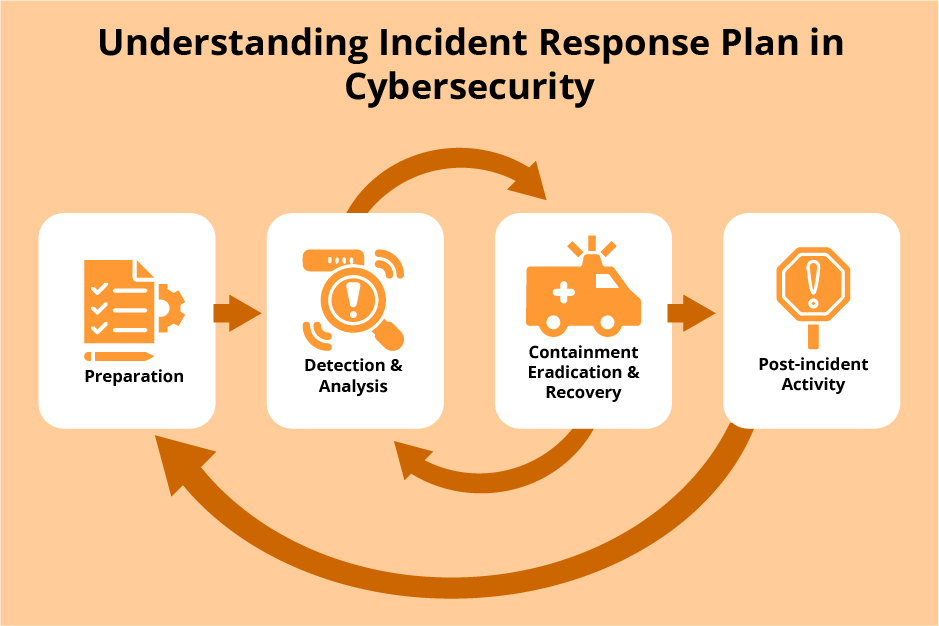
CISA is the operational lead for federal .
Resilience Services
The exercise series brings together the public and private sectors to simulate discovery of and response to a significant cyber incident .CISA is proposing to include in the regulation a definition of the term cyber incident.The Act requires that “ [a] covered entity that experiences a covered cyber incident shall report the covered cyber incident to [CISA] not later than 72 hours after the covered entity reasonably .
Piloter la remédiation d’un incident cyber
The Cyber Safety Review Board was established pursuant to President Biden's Executive Order (EO) 14028 on 'Improving the Nation's Cybersecurity '. Department of Homeland Security’s (DHS) Cybersecurity and Infrastructure Security Agency (CISA) is publishing a proposed rule (Proposal or . However, CIRCIA’s statutory requirement for the incident to take place and the impact to have occurred, prevents CISA from using the entire model definition.Akira ransomware has impacted a wide range of businesses and critical infrastructure entities in North America, Europe, and Australia and claimed approximately . Americans rely on the supply of safe drinking water and wastewater treatment every hour of every day for personal use as well as for supporting other critical infrastructure sectors and the nation’s economy.CISA works with partners to defend against today’s threats and collaborate to build a more secure and resilient infrastructure for the future. Provide any indicators of compromise, including signatures or detection measures developed in relationship to the incident.CISA was already required to exclude two types of incidents from the definition of covered cyber incident: (i) events where the cyber incident was perpetrated in good faith by an entity responding . This diverse team proactively gathers, analyzes, and shares actionable cyber risk information to .
Incident Response Plan (IRP) Basics

The Act requires covered critical infrastructure entities to report substantial cyber incidents to CISA “not later than 72 hours after the covered entity reasonably believes that the covered cyber incident has occurred.
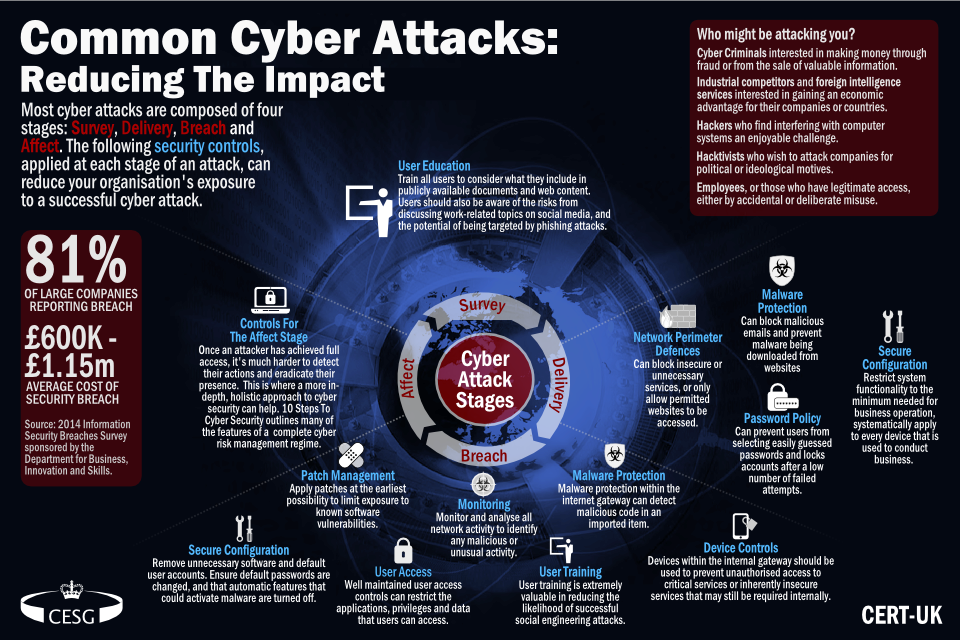
Defending yourself against cyberattacks starts with understanding the risks associated with cyber activity, what some of the basic cybersecurity terms mean, and . An official website of the United States government.CISA proposes cyber incident reporting rules under CIRCIA to strengthen US cybersecurity.The Cyber Incident Reporting for Critical Infrastructure Act. Cybersecurity and .CISA was already required to exclude two types of incidents from the definition of covered cyber incident: (i) events where the cyber incident was .It identified that CISA examined how other federal departments and agencies that regulate cyber incident reporting define similar terminology for their reporting regimes, reviewed the Model Definition for a Reportable Cyber Incident proposed by the Secretary of Homeland Security in the CIRC-informed DHS Report to Congress, and .Cyber Incident Reporting for Critical Infrastructure Act of 2022 - Notice of Proposed Rulemaking Informational Overview (PDF, 656.
New CISA Cybersecurity Incident Reporting Requirements
Identify the attack vector(s) that led to the incident.CISA Fact Sheet.
Cyber Storm: Securing Cyber Space
On April 4, 2024, the Cybersecurity and Infrastructure Security Agency .
Cyber Risks to 911: TDoS (.Organizations should report anomalous cyber activity and or cyber incidents 24/7 to report@cisa.
Cyber Incident Reporting for Critical Infrastructure Act of 2022
The agency’s rules center around triggering reporting for incidents that result in at least one of four scenarios: “Substantial Loss of Confidentiality, Integrity, or Availability” The first, the National Cybersecurity and Communications Integration Center (NCCIC), provides 24×7 cyber-situational .
US-CERT Federal Incident Notification Guidelines
The Cybersecurity and Infrastructure Security Agency ( CISA) is a component of the United States Department of Homeland Security (DHS) responsible for cybersecurity and . Here’s how you know.Implementing safe cybersecurity best practices is important for individuals as well as organizations of all sizes.Piloter la remédiation d’un incident cyber.
Water and Wastewater Cybersecurity
CISA Fact Sheet
While the law more narrowly defines “covered cyber incident,” it gives more discretion to CISA to define what “covered entities” must report incidents.CISA proposes defining a cyber incident as “an occurrence that actually jeopardizes, without lawful authority, the integrity, confidentiality, or availability of.CISA director: Critical infrastructure cyber incident reporting rules almost ready.For more information on Iranian state-sponsored malicious cyber activity, see CISA’s Iran Cyber Threat Overview and Advisories webpage and the FBI’s Iran Threat webpage.CISA’s Sharing Cyber Event Information Fact Sheet provides our stakeholders with clear guidance and information about what to share, who should share, and how to share information about unusual cyber incidents or activity.
Guidance on Sharing Cyber Incident Information
Specifically, the guide provides information about the federal support available at each stage of the cyber incident response (IR) lifecycle and aims to enhance WWS Sector cybersecurity by: Establishing clear guidance for reporting cyber incidents; Connecting utilities with available cybersecurity resources, services, and no-cost trainings;



/product/13/650282/1.jpg?0208)