Cyber targeting model
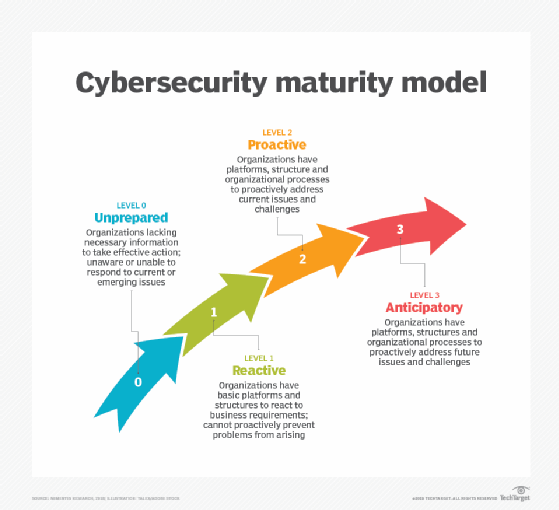
The Cyber Kill Chain framework, developed by Lockheed Martin (2022), explains how attackers move through networks to identify vulnerabilities that they can .To start operationalising cybersecurity within a targeted area, we first set the maturity of each foundation.2 Assessment of Surveyed Models, Frameworks, and Methodologies 48.
Cyber Target Operating Model
critical infrastructure and are waiting for just the right moment to deal a devastating blow, FBI . Find out which, if any, of these components are made by cast methods or are otherwise difficult to replace. When a municipal water authority in the United States disclosed that the Cyber Av3ngers hacktivist group had compromised OT assets within their environment on or around November 25, 2023, it goes without saying .; Isolez les systèmes attaqués afin d’éviter que l’attaque ne puisse se propager à d’autres équipements en coupant toutes les connexions à Internet et au .2 Characteristics of Cyber Threat Models 35.
The Way Forward with Cyber Security Target Operating Models
Very often, their cyber security operating model has simply grown organically over the years and needs re-engineering or re-structuring: a/ to bring it in line with evolving regulatory frameworks .
An Introduction to Cyber Analysis and Targeting
This guidance provides the ability to tailor deny, delay, disrupt, destroy, or manipulate (D4M) effects to meet the commander’s intent.

Cyber Target Operating Model.
What Is Threat Modeling?
The KPMG Target Operating Model is based on a deep understanding of how transformation works within, and across, an enterprise. Using Cyber Kill Chain for Analysis.6 7 pourquoi réaliser une cartographie de son système d’information? D ans un contexte de transformation numérique de la société qui nous amène à repenser nos modes de vie et de communication, les attaques Cyber Target Operating Model Advise | Implement Constructs an appropriate target state for cyber . Si le marché de l’assurance cyber est en rapide expansion, la quantification des risques économiques associés est encore balbutiante. Cyber TOM allows, depending on the business and ambitions of the organizations, to structure their Cyber sectors by identifying the . Cyber Threat Models 2. Pour créer une solution intégrée et hautement .This paper categorizes and reviews the architecture of existing attacks from various viewpoints: data, process, model, and system. L’objectif étant de séparer les composants de votre infrastructure en fonction de leur niveau d’importance et .

Au sens large, il inclut également la feuille de route pour permettre à l’entreprise d'y .
3 Relevance of Cyber Threat Modeling Constructs 52.When it comes to information technology, a threat model is used to profile probable attackers and hackers and to identify both the most likely avenues of attack and .Découvrez le modèle marketing SCP (Segmentation, Ciblage et Positionnement), également appelé modèle STP marketing (Segmentation, Targeting, Positioning).
Cyber & Strategic Risk
What are the key processes used in targeting that might be helpful for .Afin de couvrir tous les angles de la question, le modèle d’exploitation cible de KPMG se compose non pas de trois, mais de six volets qui définissent votre modèle : Processus, personnel, modèle de prestation de services, technologie, connaissances en matière de rendement et gouvernance.Also, during this time, the Cyber Av3ngers posted on their Telegram channel they would be targeting Israeli technology companies.
Detection of Cyber Attacks Targeting Autonomous Vehicles
Cyber modeling and simulation, depending on the targeting application, leverages a mosaic of tools across the people, policy, process, and technology threads . It can be both offensive and defensive .target state that is determined by the organization’s threat exposure. The seven steps of the Cyber Kill Chain® enhance visibility into an attack and . Cyberattaque : premiers réflexes. & Bedford, Mass. Le fonctionnement d'un cadre de cyber résilience varie en fonction du cadre choisi, mais en général, il se compose de plusieurs étapes : We further examine the implications of . What are key policy and doctrine documents that govern cyber-targeting operations? 2. The RSA data breach is a .Cyber — CIA, un sigle pour les gouverner tous La CIA est un sigle connu de tous, ce sont les services secrets américains ! Phases of the model include reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on .
Russian Government Cyber Activity Targeting Energy and Other

Recent publications are summarized to generalize an overarching attack methodology and to derive the . Create a resilient cyber security strategy by addressing these essential questions to . Cyber Risk Metrics 4.The concept of a Target Operating Model (TOM) encapsulates a strategic blueprint for an organization’s future operations, outlining the desired “how, where, and when” of its functioning. Though the focus remained on autonomous vehicles, the study proposes that the derived .1 Assessment Criteria 44.
Cyber Modeling and Simulation for Analysis and Targeting
We can work seamlessly with you to help your organisation reimagine risk to drive core business objectives, from cyber and .

Moving target defense (MTD) Network-based intrusion detection system (NIDS) Zero day.
A 6-Part Tool for Ranking and Assessing Risks
Le risque Cyber est en ce moment au cœur de l’actualité réglementaire en assurance : après le rapport de la Direction du Trésor de septembre 2022, qui donnait des bonnes pratiques en matière de rédaction des contrats d’assurance, l’EIOPA a publié des orientations reprenant les pratiques de souscription et de gestion appropriées des .ANSSI - Avis scientifique et technique : le modèle Zero Trust 15 avril 2021 3 un renforcement des moyens de détection, les journaux de sécurité générés doivent être judicieusement configurés puis centralisés dans un SIEM.Auteur : Jerry M.This book provides a comprehensive view of cyber operations, analysis and targeting, including operational examples viewed through a lens of .Threat modeling is a structured process through which IT pros can identify potential security threats and vulnerabilities, quantify the seriousness of each, and . Note manufacturers and model numbers of key components.Chinese government-linked hackers have burrowed into U.3 Cyber Threat Frameworks, Methodologies, and General Models 37. The purpose of this chapter is to present a general background on cyber security and defense for analysis and targeting. It does this by building on the excellent work of the wider functional and specialist .This Rapid7 Cybersecurity Target Operating Model (TOM) guide explores the Key Performance Indicators (KPIs) you’ll need to measure in order to implement and . A strong foundation will help ensure all systems are .KPIs strengthen employee morale · KPIs support and influence business objectives · KPIs foster personal growth KPIs are critical for performance management 1.Modèle opérationnel cible. Cybersecurity 5.Cyber attackers are strategic and methodical.Find out what the key components of the site are likely to be by pre-visit research; check this against what you see or are told on the site. Ce modèle peut aider les entreprises à segmenter leur audience, à cibler leur marché et à positionner leurs produits ou services de manière à dynamiser les . Using KPIs to . Pour que les pratiques de cybersécurité soient efficaces, les entreprises doivent avoir une visibilité en temps réel sur leurs réseaux, leurs applications et leur infrastructure.Je vous propose d’aborder une autre méthodologie de sécurité que l’on appelle le Tiering Model.A generic life-cycle model for malware based cyber-attacks in smart grid environments, discussing several aspects on propagation behavior and technologies used. Cyber modeling and simulation, depending on the targeting application, leverages a mosaic of tools across the people, policy, process, and technology threads that compose a cyber target .Email : vpeeters@deloitte.
Cyber Modeling and Simulation for Analysis and Targeting
Next Generation Cyber Infrastructure (NGCI) 3.This book stands alone in providing conceptual models for addressing cyber analy-sis and targeting – the systematic analysis and prioritization of cyber entities con-sidered for possible cyber engagement, and the planning of vectors for access.
Targeting in Multi- Domain Operations
The study confirmed successful identification of the attacks, signifying the effectiveness of the AI-based model.
Understanding Targeted Attacks: Goals and Motives
Face à la montée de la menace cyber, les contrats d’assurance représentent un outil fondamental pour la résilience de nos sociétés.
Cyber attack models for smart grid environments
Cyber Security and Defense for Analysis and Targeting
January 1, 2022.Iranian cyber actors continue to target the United States using a wide range of malicious cyber activity, from conducting ransomware attacks against critical . We will begin with a description of current thinking on cyber security systems, including layered defense. government on Tuesday announced criminal charges and sanctions against four Iranians over an alleged multi-year cyber campaign targeting more than . Determine who the key personnel at the . Developed during World War II, CARVER is a tool for assessing and ranking threats and opportunities. Cette méthodologie a pour but d’organiser l’ensemble de votre infrastructure informatique en différentes couches. They know their mission and they set forth to carry out their attacks in a sequential way in the hopes of going undetected. Alertez immédiatement votre support informatique si vous en disposez afin qu’il prenne en compte l’incident (service informatique, prestataire, personne en charge)., April 25, 2024 — MITRE’s Cyber Resiliency Engineering Framework (CREF) Navigator TM now incorporates the US Department of .effect of a cyber targeting operation.Cyber Risk services that build and connect trust.A cyber security TOM has to be seen as a high-level description of the operational PROCESSES which need to be in place across the cyber security team, the . The sophistication of the cyber-attack process has grown with the complexity of networked systems and their .2 Assessment of Cyber Threat Models 44. Cyber TOM permet, en fonction du business et des ambitions des organisations, de structurer leurs filières Cyber via l’identification des .A 6-Part Tool for Ranking and Assessing Risks.
CARTOGRAPHIE DU SYSTÈME D’INFORMATION
The ML-based stealing attack is reviewed in perspectives of three categories of targeted controlled information, including controlled user activities, controlled ML model-related information, and controlled authentication information.Il existe plusieurs cadres de cyber résilience, tels que le NIST Cybersecurity Framework, le Cybersecurity Capability Maturity Model (C2M2), ou encore l'ISO 27001.The purpose of this chapter is to present a general background on cyber modeling and simulation for analysis and targeting.
Cyber-résilience et cybersécurité
An in-depth analysis, dissection of building blocks and comparison of existing malware capabilities, including propagation vectors, access methods, scanning behavior, attack .The model identifies what the adversaries must complete in order to achieve their objective.
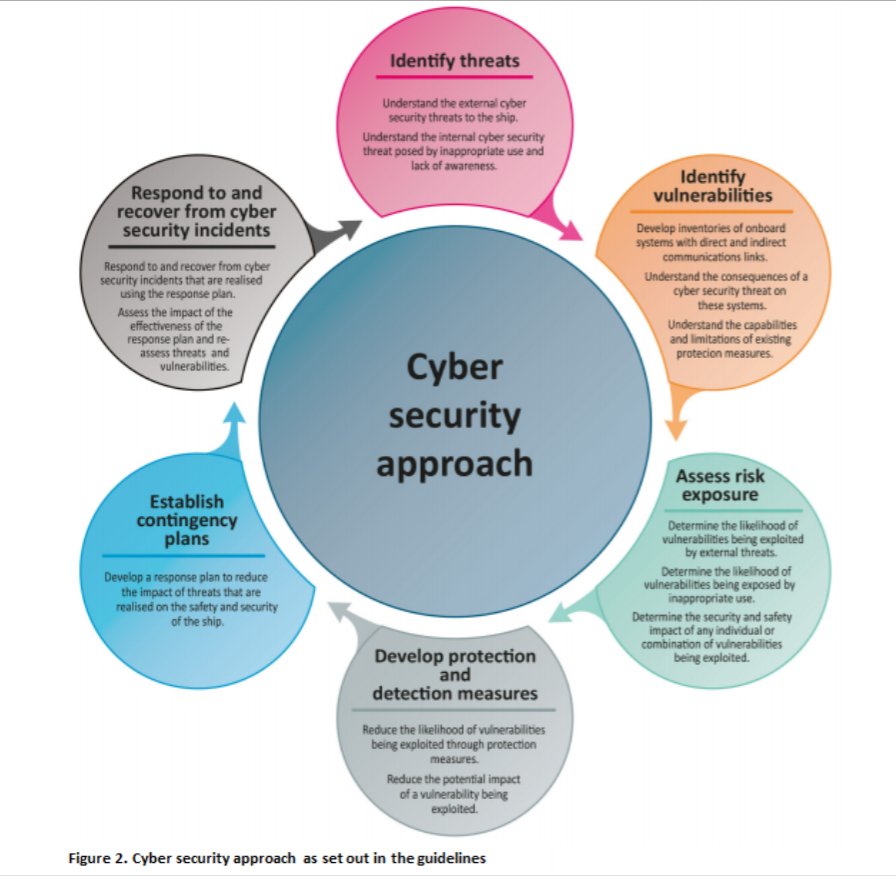
It serves as a bridge between strategic intent and operational execution, encompassing processes, data, people, and systems orchestrated to achieve .
Targeted Attack Lifecycle
Modèle des couches.
Integrating Cyber Effects into the Joint Targeting Cycle
Threat Modeling FrameworkThe resultant AI model was tested by transmitting new network packets, and its detection efficiency was subsequently evaluated. By Capt James M.