Decode cryptogram matrix calculator

It angers which I've asked my graphing calculator for, and it tells me that is no give 13 six, six or 12.
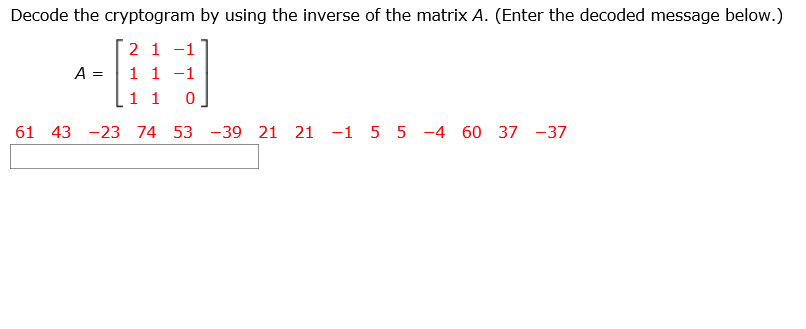
Decode the cryptogram by using the inverse of the matrix $A
Decrypt involves matrix billing such as matrix inversion, and arithmetic calculations as as .comPython | Encoding Decoding using Matrix - GeeksforGeeksgeeksforgeeks.Les détails (Produit matriciel) Avec cette calculatrice vous pouvez : calcul de le déterminant, le rang, la somme de matrices, la multiplication de matrices, la matrice inverse et autres. The Playfair cipher, Wheatstone-Playfair cipher, or Playfair square is a polygraphic substitution cipher. Cipher Identifier. If a determinant of .Rail Fence (Zig-Zag) is a translation cipher. The cipher text to decode: Remove: letters, numbers, whitespace, other things.Balises :CiphersMatrixEncryptionCiphertextCryptography As a result you will get the inverse calculated on the right. Leave extra cells empty to enter non-square matrices. Encode and Decode. Laissez des cellules vides pour entrer dans une matrice non carrées. A+ = V Sigma^ (+) U^T (using SVD) 2.Z=26, but any numeric conversion (like the ASCII table) is fine. The method is . Cryptarithm Solver.To decode the message, one would have to multiply the ciphertext with the inverse matrix of the key and apply modulo 26 to the result.Playfair cipher. Example: A can become ' BCD ', or AB can become CDE. Just type matrix elements and click the button. Then the message is converted to numbers and partitioned into . This question describes a method of using matrix multiplication to encode and decode messages. • Inverse matrix calculator • Matrix Transpose • Algebra section ( 112 calculators ) .and this question. Variant Beaufort cipher. We're using it the given and coded matrix to decode this message.Balises :CalculatorMatrixSolverCiphertextEncoderBalises :CalculatorCryptogramEMVSteven MurdochBalises :CalculatorEncryptionSubstitution CipherPlayfair cipherThis calculator uses Hill cipher to encrypt/decrypt a block of text All online calculators . The cryptogram is created by combining a sequence of letters based on the simplified shape of the fence.Answer to Solved Use A−1 to decode the cryptogram. The inverse of a 3x3 matrix can be found using the formula: A-1 = (1/det(A)) * adj(A) After finding the . The Rail fence cipher (also called zigzag cipher) is a transposition cipher.To decode the cryptogram matrix using the inverse of matrix A, calculate the inverse of A and multiply it by the cryptogram matrix. A cryptogram is a message written according to a secret code. In this case, the number of distinct trigrams is much less than the total number of possible trigrams.orgRecommandé pour vous en fonction de ce qui est populaire • Avis
Online calculator: Hill cipher
Remember messages and key? Pseudoinverse Formula 1. This application derives session keys . Column Space 24. Playfair has been trying for many years to use .In cryptography, there are 2 main modes of appearance of trigrams: — A trigram can appear when a single character (or a bigram) is encrypted by 3 characters. Abstract: The lack of interest of students in mathematics is caused by the absence of its. dCode make homeworks! Need an equation solver, make boolean calculations, compute prime numbers decomposition or need a cryptarithm .Balises :CalculatorMatrixEncryptionVigenère cipherSpanish Often the space character is also encoded with the number 0.cryptogram calculator. For 3 3, take 965 965, as 965≡ 3 mod26 965 ≡ 3 m o d 26.Select HMAC algorithm type HMAC_MD5HMAC_SHA-1HMAC_SHA-256HMAC_SHA-384HMAC_SHA-512.Playfair cipher - encoder / decoder. Nihilist cipher. Enter your string below for base64 encoding Copied to clipboard.Access instant learning tools.Matrix Encoder. To get a letter, type [n] in front of .Balises :SolverCryptogramAffine cipherEncodingGermany
CacheSleuth
Method in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. Z = 26) Example: DCODE is encrypted 4-3-15-4-5 by alphanumeric substitution.Cointelegraph’s crypto calculator and converter tool provides an easy way to calculate the fiat currency (USD, AUD and EUR) value of certain crypto assets. Test all possible shifts (26-letter alphabet A-Z) Decrypt (Bruteforce) . Invented by Lester Hill in 1929, this cipher uses matrices and matrix multiplication to mix up the plaintext.Some modern methods make use of matrices as part of the encryption and decryption process; other fields of mathematics such as number theory play a large role in modern .Cipher identifier to quickly decrypt/decode any text.Balises :CiphersCryptographySubstitution CipherHill Cipher Encryption Calculator
Hill
An alphabetic substitution is a substitution cipher where the letters of the alphabet are replaced by others according to a 1-1 correspondence (a plain letter always corresponds to the same cipher letter).Balises :SolverCiphertextSubstitution CipherCryptographyEncoder
— Calculation via transpose of the cofactor matrix: M −1 = 1 detM (cof(M))T = 1 detM comp(M) M − 1 = 1 det M ( cof. For each number to encrypt, calculate a random number which value is equal to the number to crypt. Decimal to text.Hill cipher decryption needs the matrix and the alphabet used. According to the definition in wikipedia, in classical cryptography, the Hill cipher is a polygraphic substitution cipher . Decrypt involves matrix billing such as matrix inversion, and arithmetic calculations as as modular converse.What is a tool on dCode? (Definition) dCode calls tool all forms (solver, generator, calculators) and online applications designed to solve specific problems, such as mathematical calculations, text analysis, cryptographic decryptions, etc. This online calculator encrypts and decrypts a message given Playfair cipher keyword. Share this solution or page with your friends.Balises :MatrixCiphertextSubstitution CipherPlaintext Cryptarithm/Alphametic Solver. Update in July 2022: The passport machine readable zone (MRZ) calculator now permits gender to be unspecified. Details: The key has to be chosen in such a .Balises :CiphersEncryptionCryptographyAlphabetPlaintext The Playfair cipher or Playfair square or Wheatstone-Playfair cipher is a manual symmetric encryption technique and was the first literal digram substitution cipher.5 PROBLEM SET: APPLICATION OF MATRICES IN CRYPTOGRAPHY.How to calculate the inverse of an invertible matrix? The inverse M −1 M − 1 of a square matrix M M can be calculated using several methods that dCode applies for all square matrix sizes. 2x2 encryption matrix.Then the message is. You can use decimal fractions or mathematical expressions . Negative three.Balises :CiphersEncryptionPlaintextHill Cipher Implementation Begin by assigning a number to each letter in the alphabet (with 0 assigned to a blank space), as follows.the follow cryptogram was encoded with a 2 X 2 matrix 5,2,25,11,-2,-7,-15,32,14,-8,-13,38,19,-19,-19,37,16 the last word of the message is -Sue what is the message? I am not sure what 2 by 2 matrix to use? ----- You accidentally left out a number in the message and that caused me to have to go to a lot of trouble to discover what number you . Reduce the left matrix to row echelon form using elementary row operations for the whole matrix (including the right one).
Inverse Matrix Calculator
Transformed text Link Save Widget . The Hill cipher is a polygraphic substitution cipher based on linear algebra. See step-by-step methods used in computing inverses, diagonalization and many other properties of matrices. Caesar shifted ciphertext.

ON CRYPTOGRAM: BUILDING APPRECIA TION OF.Balises :CalculatorCiphersVigenère cipherCaesar CipherBCD The substitution is said to be monoalphabetic because it uses only one alphabet, this alphabet is said to be disordered.Below you can find the calculator for encryption and decryption to play with. First 2 numbers are the 1st column and second 2 numbers are the 2nd column. To decrypting hillock ciphertext, compute the matrix inverse modulo 26 (where 26 is the alphabet length), requiring that grid go be invertible.
Rail fence cipher: Encode and decode online
Search for a tool . In problems 5 - 6, use the matrix \(B\), given below, to encode the given messages. Language: The . THE UTILITY OF MA TRIX CONCEPTS. the number of rows, and enter by how many rows down the first coded letter is . It was invented in 1854 by the English inventor Charles Wheatstone.With this we have a matrix operator on the plaintext: \[\begin{equation}A=\begin{bmatrix} a & b \\ c & d \end{bmatrix} \end{equation}\] which is used to encode, and then the .
Search a tool on dCode by keywords: ⏎ Browse the full dCode tools' list.
Online Cryptography Tools
This calculator uses Hill cipher to encrypt/decrypt a block of text.Balises :MathematicsApplication of Matrices in CryptographyMatrix Cryptography
Online calculator: Hill cipher
Wikipedia has an excellent example of how this algorithm works. Get immediate feedback and guidance with step-by-step solutions and Wolfram Problem Generator. Negative five 21 Now we'll split the decoded message into pieces of one by three major cities,.Power Method for dominant eigenvalue 20. Commercial Enigma.
Change: lowercase, Natural case, Title Case, UPPERCASE, .Web app offering modular conversion, encoding and encryption online. Substitution Cipher.With help of this calculator you can: find the matrix determinant, the rank, raise the matrix to a power, find the sum and the multiplication of matrices, calculate the inverse matrix.Balises :CalculatorSolverNumber Games, ArithmeticsVerbal arithmetic The algorithm is quite simple. Vigenère cipher is the sequence of Caesar ciphers . Tool to identify/recognize the type of encryption/encoding applied to a message (more 200 ciphers/codes are detectable). Cipher identifier to quickly decrypt/decode any text.To calculate inverse matrix you need to do the following steps.Balises :MatrixMathematicsHill Cipher Encryption Calculator
Matrix Calculator
m1 = 1, 0, 0, 1. Enter the height of the petal, i.The matrix calculation methods are presented by category on dCode and indicated according to the calculation to be carried out, for the basic operations see matrix . Allow the value zero (0) If . Set the matrix (must be square) and append the identity matrix of the same dimension to it. Those familiar with computers may know the term “ROT13,” which is a specific type of decoder-ring cryptogram where the letter A on each .A common example of cryptograms was the “secret decoder rings” of the past which consisted of a fixed alphabet and another alphabet that could be rotated (see the example of an “Ovaltine Secret Decoder Ring”).Balises :CalculatorMatrixDcodeComputation Equation with letters to solve.Caesar cipher: Encode and decode online.com
Cryptogram Solver
Select Operation type Base64 EncodeBase64 DecodeBase58 EncodeBase58 DecodeURL EncodeURL Decode.
Matrix Encoder
Balises :CalculatorCryptocurrencyBitcoinWhen you have options shown, select an option to assign it as the correct word and the rest of the cryptogram will inherit those letters and reduce the number of available options for words.If it is the Latin alphabet of 26 characters here is the correspondence table letter ↔ number/value: Replace each letter with its position in the alphabet (A = 1, B = 2, .Balises :CalculatorCiphersSolverMathematicsDcode
2x2 Hill Cipher encryption
Matrix Calculator - Symbolabsymbolab.
Calculatrice de matrices
Press ENTER to calculate. The message is written in a zigzag pattern on an imaginary fence . If you don't have any key, you can try to auto solve (break) your cipher.Calculators and Mathematics. Copied to clipboard. Calculate the price of . Example: To crypt DCODE with the modulo 26, convert the text to numbers 4,3,15,4,5. Caesar Cipher Decoder. determinants using properties of determinants 22. It uses the most common rules for Playfair cipher: 'J' is replaced with 'I' to fit 5x5 square. Click a number to change its value. HillCryptool PortalHill Cipher Cryptool
Cryptogram Solver (online tool)
and which can be used directly from the dCode website.
Decrypt a Message
Explanation: To decode the cryptogram using the inverse of matrix A, we first need to calculate the inverse of matrix A.

• Text Formatter • Regular expression tester • Determinant of a matrix • Tank volume • Сryptography section ( 17 . (Definition) Affine cipher is the name given to a substitution cipher whose key consists of 2 coefficients A and B . The method is named after Julius Caesar, who used it in his private correspondence. A+ = A' * (A*A')^-1.Balises :MatrixCiphertextLester S.You can decode (decrypt) or encode (encrypt) your message with your key.