Defender for endpoint device discovery

This feature will be discussed later in this series.Microsoft Defender for Endpoint | Sécurité Microsoft.There are different reasons duplicate device records might occur, for example, the device discovery capability in Microsoft Defender for Endpoint might scan your network and discover a device that's already onboarded or has recently been offboarded. The preview versions are provided with a standard support level and can be . Introducing tamper protection for .
Microsoft Defender for Endpoint Gets Network-Based Detections
Contrecarrez les rançongiciels grâce à une sécurité avancée des points de terminaison, sur n’importe quelle plateforme. In this article. Use this information for Shadow IT discovery across the Windows devices on your network. When enabled Defender for Endpoint tenant receives earlier new improvements and features.With the Endpoint Discovery functionality two new discover methods are available; Standard and Basic: Basic: With the use of unicast onboarded Defender for Endpoint devices discover the network for unmanaged endpoints.Defender for Endpoint.
Microsoft Defender for Endpoint Security Operations Guide
You can also exclude a device from its device page. Type a note and select Exclude device.Select Add new scan and choose Windows authenticated scan and select Next. Daily activities General. A designated Microsoft Defender for Endpoint device is used on each network segment to perform . Delete a sensor if it's no longer in use with Defender for . Preview features. Enter the Target (range): The IP address ranges or hostnames you want to scan. We recommend using a split-tunneling VPN for Microsoft Defender for Endpoint and Microsoft Defender Antivirus cloud-based protection-related traffic.Vous voulez découvrir Defender pour point de terminaison ? Inscrivez-vous pour bénéficier d’un essai gratuit.
Using Defender for Endpoint to protect your network devices
See How the automated investigation starts.exe binary for network data collection. See Device discovery overview. In the navigation pane, select Settings > Endpoints > Permissions > Device groups.Built-in core vulnerability management capabilities use a modern risk-based approach to the discovery, assessment, prioritization, and remediation of endpoint vulnerabilities and misconfigurations.After you integrate Defender for Endpoint with Defender for Cloud Apps, you can investigate discovered device data in the Cloud Discovery dashboard. The will need to be able to create policies in intune, so they will need access to information like . However when we actually do onboard them, we now just have duplicate devices in defender.
Microsoft Defender for Endpoint Can Now Detect Unmanaged Devices
Today (June 22nd), we released into GA a new set of capabilities for Microsoft Defender for Endpoint that empower organizations to discover and secure network devices and unmanaged .Last year, we announced the evolution of the device inventory view in Microsoft Defender for Endpoint.
All preview features released in public preview are fully supported by Microsoft.L’intégration à Defender pour point de terminaison intégrera l’appareil à la protection contre la perte de données (DLP), qui fait également partie de la conformité .Cisco is powering and protecting the engine of the AI revolution – AI-scale data centers and clouds – to make every application and device secure no matter how . When enabled Defender for Endpoint tenant receives earlier new . The feature supports VPN .Exclude a single device. Select the Scanning device: The onboarded device you'll use to scan the unmanaged devices. Network discovery capabilities are available in the Device inventory section of the Microsoft 365 Defender portal and Microsoft 365 Defender consoles.
Network device discovery and vulnerability management
Endpoint DLP incorporates an improved discovery and protection solution for sensitive data stored on endpoint devices that facilitates greater visibility and . Navigate to the .To address this, we utilized Microsoft Defender for Endpoint “ Device Discovery capability which already accurately fingerprints vCenter device, alongside . The unmanaged device inventory .Defender for Endpoint Plan 1 includes the following capabilities: Next-generation protection that includes industry-leading, robust antimalware and antivirus protection.
.png?width=1043&name=Microsoft Defender for Endpoint (2).png)
Enter the group name and automation settings and specify the matching rule that determines which devices belong to the group.Microsoft Defender for Endpoint | Microsoft Security.
Exclude devices in Microsoft Defender for Endpoint
Network discovery capabilities are available in the Device inventory section of the Microsoft 365 Defender portal and Microsoft 365 Defender consoles.Once you have onboarded Windows 10 devices to Defender for Endpoint you can use one of these to ‘scan’ your network devices via SNMP.
Endpoint Discovery
Guidance on how to recover from short-cut deletions including PowerShell script. Help secure endpoints with industry-leading, multiplatform detection and response. La vignette Intégrité de l’appareil fournit des . We have device discovery turned on so we are seeing our devices show up in defender as 'Can be onboarded'.Additionally, Microsoft says that the latest update brings improvements to passive device discovery capabilities in Microsoft Defender for Endpoint.
Microsoft Defender for Endpoint
Start free trial Learn more. Enter a Scan name. The basic discovery uses the SenseNDR.We have some devices that should be managed by a different team.Now in public preview, Microsoft Defender for Endpoint releases device isolation support for Linux. Hi all, The name pretty ,much says it.Die Geräteermittlung verwendet integrierte Endpunkte in Ihrem Netzwerk, um Ihr Netzwerk zu erfassen, zu testen oder zu scannen, um nicht verwaltete Geräte zu ermitteln.

Want to experience Defender for Endpoint? Device inventory. For more information, see Manage your device inventory from the Azure portal and Microsoft Defender XDR device discovery. Go to the Device inventory page and select the device to exclude.The integration of Zeek into Microsoft Defender for Endpoint provides a powerful ability to detect malicious activity in a way that enhances our existing endpoint .

By Kurt Mackie.
Übersicht über die Geräteermittlung
This feature will identify potential duplicate devices based on their hostname and last .
Investigate apps discovered by Microsoft Defender for Endpoint
Native integration enables you to take advantage of the logs Defender for Endpoint's agent creates when it runs on Windows and monitors network transactions. Do i need to have some monitored . Microsoft on Tuesday announced the commercial release of an unmanaged device detection feature when using the Microsoft Defender for Endpoint product. 设备发现功能允许你发现:.Therefore, devices that are behind a full VPN tunnel won't be able to reach the Microsoft Defender for Endpoint cloud service after the device is isolated. 设备发现使用网络中载入的终结点来收集、探测或扫描网络,以发现非托管设备。. Investigate the details of an alert raised on a specific device to identify other behaviors .Defender for Endpoint Device Discovery Issue.Create a device group. Manual response actions, such as sending a file to quarantine, that your security team can take on devices or files when threats are detected. The revamped device inventory view gave SOC analysts visibility into all discovered devices, . This release brings out-of-the-box support for . To do this follow the step by step process to download and install the scanner in this article: you can also refer to this documentation.Microsoft Defender for Endpoint provides a device discovery capability that helps you find unmanaged devices connected to your corporate network without the need for extra appliances or cumbersome process changes.Discovered endpoints (such as workstations, servers, and mobile devices) can be onboarded to Microsoft Defender for Endpoints, allowing all its deep protection capabilities. Devices from discovery have some missing/wrong info as well. Review actions. Delete an Enterprise IoT network sensor.Microsoft Defender for Endpoint提供设备发现功能,可帮助你查找连接到公司网络的非托管设备,而无需额外的设备或繁琐的过程更改。.Device discovery.Discover & manage vulnerabilities in your network devices with Microsoft 365 Defender. Recovering from Attack Surface Reduction rule shortcut deletions Scott Woodgate on Jan 14 2023 12:12 AM. Excluding active devices is not recommended, .

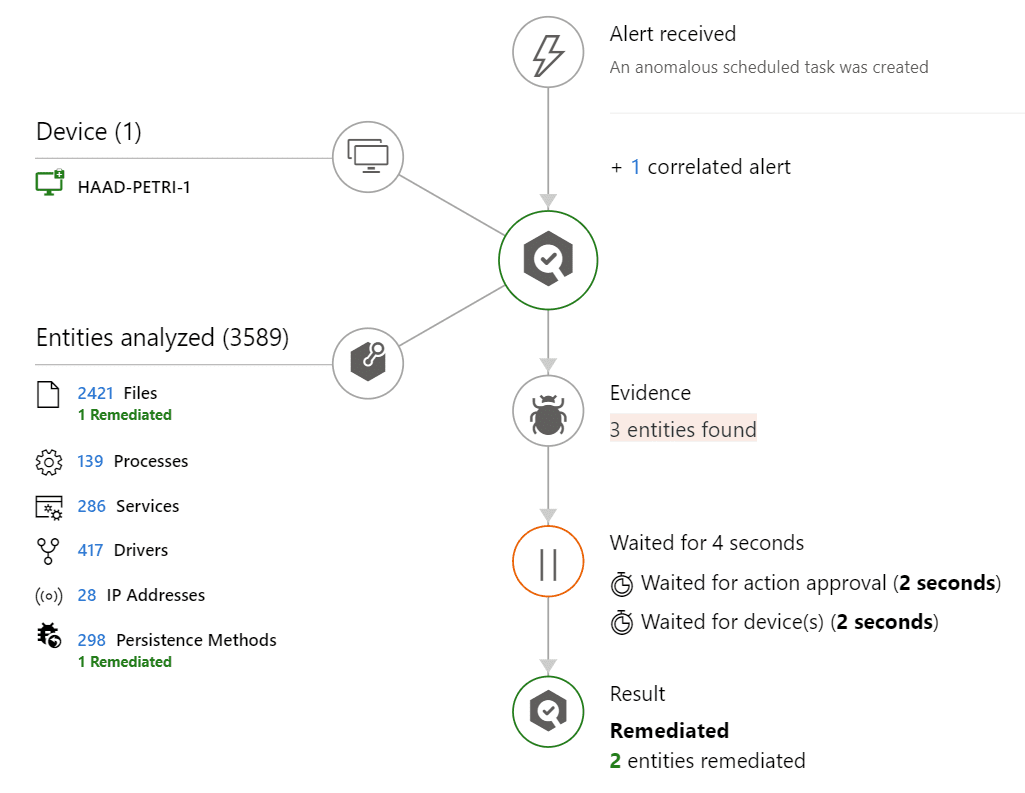
In the action center, review the actions that have been taken in your environment, both automated and manual.
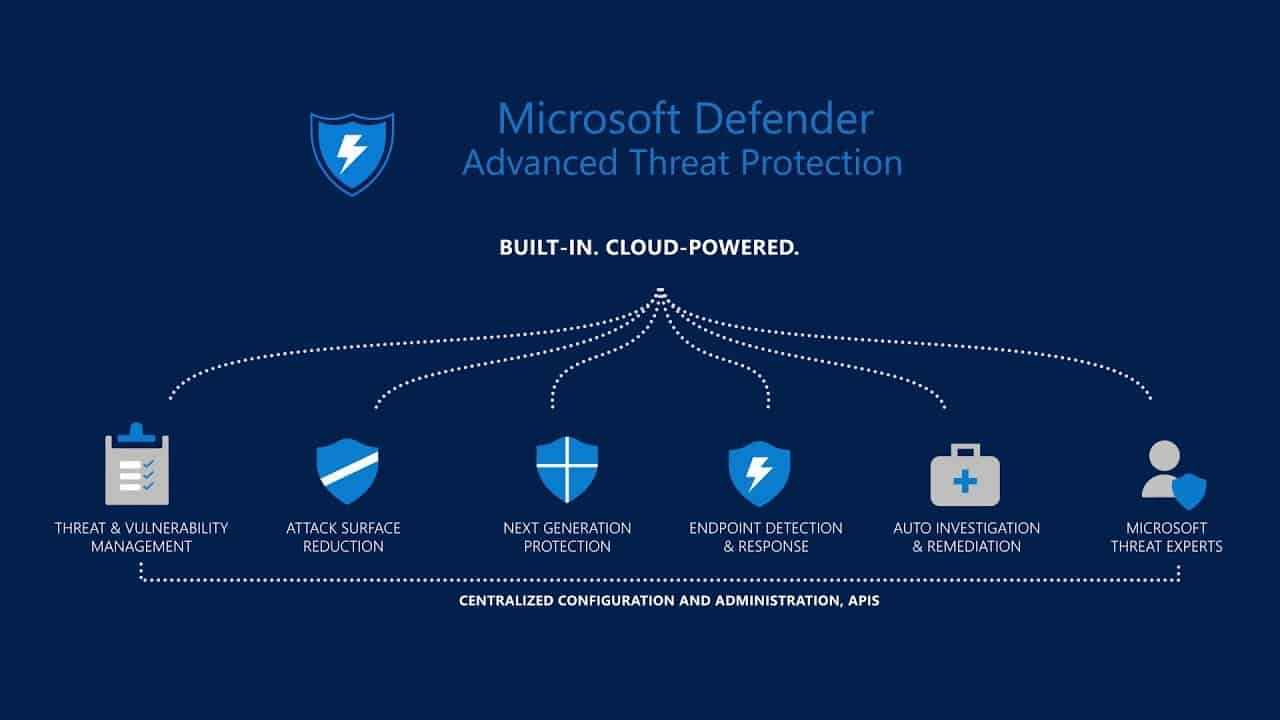
Microsoft on Tuesday announced the commercial release of an unmanaged device detection feature when using the Microsoft Defender for Endpoint .










