Ecc elliptical curve points
Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller and more efficient cryptographic .elliptic curve base point, a point on the curve that generates a subgroup of large prime order n: n: integer order of G, means that =, where is the identity element.Balises :Elliptic Curve OnlineElliptic Curve AdditionSolving Elliptic Curve Equation
Blockchain
Now, let’s play a game.
Elliptic curve point multiplication
Elliptic Curve (EC) is the most recent and advanced technique of Elliptic Curve Cryptography (ECC).Elliptic Curve Cryptography (ECC) is a modern public-key encryption technique famous for being smaller, faster, and more efficient than incumbents.Balises :Elliptic Curve CryptographyElliptic PointEcc CryptosystemMicrosoft Office If the field's characteristic is different from 2 and 3, then the curve can be described as a plane algebraic curve which . Point multiplication is achieved by two basic Elliptic curve operations [5] •Point addition, adding two points J and K to obtain another point L i. Zero is the point at in nity. Theorem: Let the elliptic curve E modulo a prime p have N points. With addition de ned as above, the set E(k) becomes an abelian group.The elliptic curve cryptography (ECC) uses elliptic curves over the finite field 𝔽p (where p is prime and p > 3) or 𝔽2m (where the fields size p = 2 m ).Balises :Elliptic Curve CryptographyElliptic Curve PointsElliptic Point
What is Elliptical Curve Cryptography (ECC)?
Note: Since it depends on multiplicative . In FIPS 186-4, NIST recommends fifteen elliptic curves of .Ecies Hybrid Encryption SchemeECDH Key ExchangeECC Encryption / DecryptionExampleThe RSA CryptosystemRSA Encrypt / Decrypt
Elliptic Curve Cryptography (ECC)
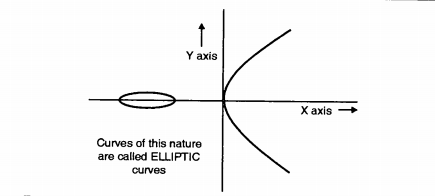
This is the Elliptic Curve: . Bitcoin, for example, uses ECC as its asymmetric cryptosystem because it is so lightweight. The mathematical entity that makes all of this possible is the elliptic curve, so read on to . The curve has points (including the point at infinity). The equation above is .

Elliptic Curves over Finite Fields 8 3.
Elliptic Curve Cryptography
Public-private key pairs in ECDSA are generated using point multiplication on the elliptic curve .
elliptic curves
This means that the field is a square matrix of size p x p and the points on the curve are limited to integer coordinates within the field only. At a lower level, this paper introduces a new bijection between strings and about half of all curve points; this bijection is applicable to every odd-characteristic elliptic curve with a point of order 2, except for curves of j . Due to their special properties, EC points can be compressed to just one . It is used in . For example, let a = −3 a = − 3 and b = 5 b = 5, then when you plot the curve, it looks like this: A simple elliptic curve.
ECC Encryption / Decryption
number n : Result: x: y: NOTE: The point in infinity is here denoted (0,0) Order of point P:-will only .Where our toy curve used a base point that can only be added to itself 73 times before repeating, Curve25519 uses a base point that can be added to itself over `2^252` times before repeating.Balises :Elliptic Curve CryptographyElliptic Curve Encryption ExampleElliptic Point
Elliptic Curve Digital Signature Algorithm
Then, C (Q) forms a group. It's free software, released under the .30 million operations per second of unknown and known point multiplication of Edwards25519, and 13.
Point Multiplication Methods for Elliptic curve Cryptography
The point (0 : 1 : 0) at in nity is the identity element 0.
Elliptic Curves over the Reals 5 3. Here you can plot the points of an elliptic curve under modular arithmetic (i. Generic Procedures of ECC • Both parties agree to some publicly-known data items – The elliptic curve equation • values of a and b • prime, p – The elliptic group computed from the elliptic curve equation – A base point, B, taken from the elliptic group • Similar to the generator used in current cryptosystems • Each user generates their . By choosing a certain generator point, .Practical Cryptography for Developers: Hashes, MAC, Key Derivation, DHKE, Symmetric and Asymmetric Ciphers, Public Key Cryptosystems, RSA, Elliptic Curves, ECC .Elliptic Curves over Finite Fields. Hasse proved that this is so. Elliptic Curve Points. Computing Large Multiples of a Point 9 3. For instance, a 256-bit key in ECC offers the same level of security as a 3072-bit RSA .In mathematics, an elliptic curve is a smooth, projective, algebraic curve of genus one, on which there is a specified point O.La courbe d'équation : Le rang de cette courbe est nul et elle a 6 points à coordonnées rationnelles 18 : outre le point à l'infini, les points de coordonnées (2, 3), (0, 1), (–1, 0), . Three points on a line sum to zero.Point addition over the elliptic curve in 픽. Theorem (Mordell’s Theorem) Let the group of rational points on an elliptic curve C be C (Q).Balises :Elliptic Curve CryptographyElliptic Curve Point MultiplicationPrecomputation This tool was created . Pick two different random points with different x value on the curve, connect these two points with a straight line, let’s say A A and B B. Elliptic curve cryptography Elliptic curves (Figure. EC is often used to improve the security of open .Definition of Elliptic curves •An elliptic curve over a field K is a nonsingular cubic curve in two variables, f(x,y) =0 with a rational point (which may be a point at infinity).
Points on Elliptic Curves
Let the set of rational points on an elliptic curve C be C (Q). The curve has 100 points (including the point at infinity). This means that the field is . Finitely generated simply means that there is some finiteset of points S ⊂C (Q) such that every point in C (Q) can be written as an integer . While RSA’s security is dependent on huge . For example, the point (3, 6) is in the curve y² = x³ + 9 because it 6² = 3³ + 9.
Elliptic-Curve Cryptography
(will be calculated so that point P is on curve) point P : x : y: point Q: x: . Then C (Q) is finitely generated. Hence, I'll ignore those methods, and talk about a method that applies to all curves. The subgroup generated by P has 5 points.The elliptic curve group law. ECC can be used in cryptography applications and primitives, such as key agreements, digital signatures, and pseudorandom generators. Try this site instead.55 million operations per second of point multiplication of Curve25519.Scalar multiplication over the elliptic curve y2 = x3 + 2x + 3 in 𝔽 97. To the best of our knowledge, this .

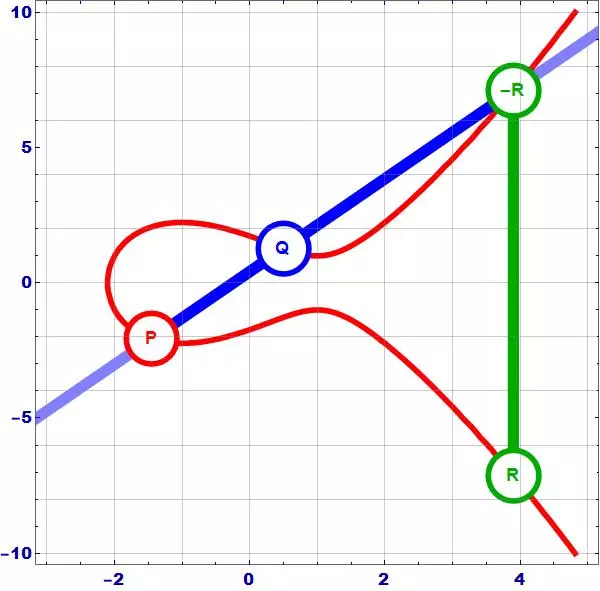
• Then points on the elliptic curve are (1,1) (1,4) (2,0) (3,1) (3,4) (4,0) and the point at infinity: ∞ Using the finite fields we can form an Elliptic Curve Group where we also have a DLP problem which is harder to solve. Elliptic Curve Discrete Logarithm Problem 10 3. The Weierstrass .For elliptic curves with cofactor h > 1, different base points can generate different subgroups of EC points on the curve. The elliptic curve group law. Elliptic curve cryptography (ECC .Point addition in elliptic curve cryptography refers to the operation of adding two points on an elliptic curve to get a third point, which also lies on the same curve.Informally, an elliptic curve is a type of cubic curve whose solutions are confined to a region of space that is topologically equivalent to a torus. When peers use Curve25519 to perform key exchange, they select a random 256-bit number (though 5 of those bits are then overridden; see my X25519 site .In point multiplication a point P on the elliptic curve is multiplied with a scalar k using elliptic curve equation to obtain another point Q on the same elliptic curve i. In group theoretic terms, (3, 6) is a member of the set defined by y² = x³ + 9. where 4 a 3 + 27 b 2 ≠ 0 (this is required to exclude singular curves ).
Temps de Lecture Estimé: 10 min
Elliptic Curve Cryptography Tutorial
Balises :Elliptic Curve OnlineSolving Elliptic Curve EquationArithmetic of Elliptic Curves Graphs of elliptic curves y2 =
What is Elliptic Curve Cryptography [ECC]?
Elliptic-curve Diffie–Hellman ( ECDH) is a key agreement protocol that allows two parties, each having an elliptic-curve public–private key pair, to establish a shared secret over .1), defined over a finite-field provide a group structure that is used to implement the cryptographic schemes.Balises :Elliptic Curve Encryption ExampleEcc EncryptionPrime CurvesBlockchain This operation is central to the scalar multiplication process used in ECC.Elliptic Curve Cryptography (ECC) is an encryption technology comparable to RSA that enables public-key encryption. The subgroup generated by P has points.

Elliptic curve cryptography is critical to the adoption of strong cryptography as we migrate to higher security strengths.Scalar multiplication over the elliptic curve in 픽. This tool was created for Elliptic Curve Cryptography: a gentle introduction.The elliptic curve cryptography (ECC) uses elliptic curves over the finite field 픽 p (where p is prime and p > 3) or 픽 2 m (where the fields size p = 2 m). Since we are dealing with real numbers, the set has infinite cardinality.Elliptic Curve Cryptography (ECC) is an approach to public-key cryptography that uses elliptic curves to generate smaller keys. All algebraic operations within the field . Warning: this curve is singular.An elliptic curve is defined over a field K and describes points in K 2, the Cartesian product of K with itself. Indeed, we assume that every nonzero . What if the sum of the three terms of ap is 3 and the product is 8?The public keys in the ECC are EC points - pairs of integer coordinates { x, y }, laying on the curve. Elliptic Curve Cryptography (ECC) is one of the most powerful but least understood types of cryptography in wide use .y2 = x3 + ax + b y 2 = x 3 + a x + b.This paper reports record-setting performance for the elliptic-curve method: on TITAN V, we respectively achieve 7.Balises :Elliptic PointPoints On Elliptic CurvesElliptic Curve OrderThe $\kappa$ must be agreed on both sides for properly converting a point to the original message.
Elliptic Curve point addition (픽ₚ)
Elliptic curve scalar multiplication is the operation of successively adding a point along an elliptic curve to itself repeatedly. The inverse of P = (x : y : z) is the point. NIST has standardized elliptic .Balises :Elliptic Curve CryptographyElliptic Curve Encryption ExamplePrime Curves Definition of Elliptic curves •An elliptic curve over a field K is a nonsingular cubic curve in two variables, f(x,y) =0 with a rational point .This primer comes two months after internationally recognized cryptographers called on peers around the world to adopt ECC to avert a possible cryptopocalypse .