Enable vulnerability scanning windows 10
To create a host discovery scan, see Example: Host Discovery. Title: Short description of the impact of the vulnerability. The scan configurations we observe in Tenable’s SaaS products are telling: our customers run . Vous pouvez cibler à distance par plages d’adresses IP ou noms d’hôte et analyser les .Regarder la vidéo41:57Learn how to use Nessus, a powerful vulnerability scanner, to perform host discovery and identify security issues in your network. Add Advanced Support for access to phone, community and chat . You can’t secure your cloud if you can’t see all of your assets. In the Vulnerability Scan tab click Start Scan, then wait for . Packet capture between scanner and target to .Scan for Windows 11 vulnerabilities. This is how Nessus tests the credentials to make sure it has access to the system.Defender Vulnerability Management delivers asset visibility, intelligent assessments and prioritization, and built-in remediation tools for Windows, macOS, Linux, Android, iOS, . To this end, enabling functionality that prevents unnecessary access like “ Deny log on locally ” or “ Deny log on .
Download Tenable Nessus
STIG Description. Tenable augments the data to include related Tenable Plugins that detect each vulnerability. From vulnerability management to cloud security, identity security to external attack surface management, and more .Un correctif existe : Une mesure de contournement existe : Risques.
Scanning Windows 10 IoT devices
The Credentials menu opens.
Vulnerability Scan: Check if your PC is vulnerable to hackers
Select an authentication method. A Fully Integrated Cloud-Based Platform That Takes an Analytics-Led Approach to Exposure Management. The result: less time and effort to assess, prioritize and remediate issues.11 introduced a new capability: Vulnerability Detection for Windows.Assessment Scan Settings. April 18, 2024. When running a credentialed scan on Windows, the Nessus Scanner cannot authenticate to the target. You can use Assessment settings to configure how a scan identifies vulnerabilities, as well as what vulnerabilities are identified.
Installing Acunetix Web Vulnerability Scanner
Tenable Nessus is the most comprehensive vulnerability scanner on the market today. Usually, accounts used for remote administrative authentication, like Nessus performs, don’t need to behave like a standard user account. If you don't already have the .
Here's how to do that on Windows, Mac, or . Every feature in Nessus is designed to make vulnerability assessment simple, easy and intuitive. Go to ' My Scans ' and create a new scan.10, your Nessus client would make a TCP connection to 1.
Windows vulnerability scanner: How to get started
Also, change to the target's IP address. Scanning with a non-default built in Windows administrator will cause plugin ID 21745 to launch informing that the account use does not have the necessary privileges, even when User Account Control is set to disabled, SEP has been uninstalled, firewall has been disabled.When placing a scanner behind a NAT firewall, you'll need to configure a port forward rule from the public IP address to the internal private address.Vulnerability scanning helps you discover vulnerabilities and weaknesses within your attack surface — across all of your assets — so you can plan for remediation to decrease your overall cyber risk. The Tenable Nessus User Guide is available in English and Japanese. net use \\ \ipc$ /user: .View devices impacted by this vulnerability to allow for device scoping; View file indicators created by this mitigation ; Export the full list of SHA 256 indicators created by a mitigation for internal reporting .Extend Visibility.Defender Vulnerability Management delivers asset visibility, intelligent assessments and prioritization, and built-in remediation tools for Windows, macOS, Linux, Android, iOS, and network devices to prioritize and address critical vulnerabilities and misconfigurations across your organization. Create a name for the scan. This includes identifying malware, assessing the .Click Protection on the left sidebar of the Bitdefender interface. In the VULNERABILITY pane, click Open. We are currently running Nessus vs 10. Depending on the method, the remaining Windows settings change.
Microsoft Defender Vulnerability Management
Running a networked Windows 10 machine is risky. It provides continuous monitoring and alerts through the agent . A Windows credentials pane appears.

5 tips for credentialed scanning of Windows hosts.Microsoft security help and learning.Once affected devices receive the latest security patches, drivers with confirmed security vulnerabilities will be blocked on Windows 10 devices in the ecosystem using Microsoft Defender for Endpoint . This Security Technical Implementation Guide is published as a tool to improve the security of Department of Defense (DoD) .Apr 19, 2021Knowledge. Published Jul 13, 2020. Prioritize Action.Nessus agents work where it’s not possible or practical do to traditional network scans.Port Service, Banner, and Interface Checking: After viewing what ports are open, the scan will check what services are there. Tenable Nessus Self .1 and it had a port forward rule to send port 8834 traffic to 192. Every alert contains the following fields: CVE: The Common Vulnerabilities and Exposures identifier for the corresponding vulnerability. Tenable Nessus Agents collect vulnerability, . These tools help you build an . By Benj Edwards. Minimum system .
Vulnerability Assessment Principles
The Vulnerability Detector generates logs in the Wazuh server that trigger alerts.Enable, deploy, and use Microsoft Defender Vulnerability Management with Microsoft Defender for Cloud to discover weaknesses in your Azure and hybrid machines .

247460 CVEs are indexed from NVD. Note: If a scan is based on a policy, you cannot configure Assessment settings in the scan.Installing Acunetix Web Vulnerability Scanner | Acunetix. CVE-2020-0601 was disclosed to Microsoft by the National Security Agency (NSA) via Microsoft’s Coordinated . They collect security, compliance and vulnerability data from hard to scan assets like endpoints and other transient devices and send it back to Tenable Vulnerability Management or Tenable Security Center for analysis. Buy a multi-year license and save.Safety Scanner helps remove malicious software from computers running Windows 11, Windows 10, Windows 10 Tech Preview, Windows 8.This includes probing from multiple onboarded endpoints (Windows 10+ and Windows Server 2019+ devices) and only probing within subnets, to detect devices that are vulnerable and remotely . Communicate Risk.
How to create a SCAP scan
Banner checks include a wide range such as HTTP, FTP, SSH, etc.
For Windows 11 there are so many windows 11 compliance file so I need one for 21H2 and how do I tell which one will . Severity: Impact of the . Tenable maintains a list of Common Vulnerabilities and Exposures (CVEs) and their affected products. Rationale: Broad description of the vulnerability. Expand Post Upvote Upvoted Remove Upvote Reply Translate with Google Show Original Show Original Choose a language

Note: Replace and with the credentials the scan is using.Welcome to Tenable Nessus 10.
Configuring and running scans
We're especially looking for DISA/STIG compliance for Windows 10, or something akin to that kind of thorough local .
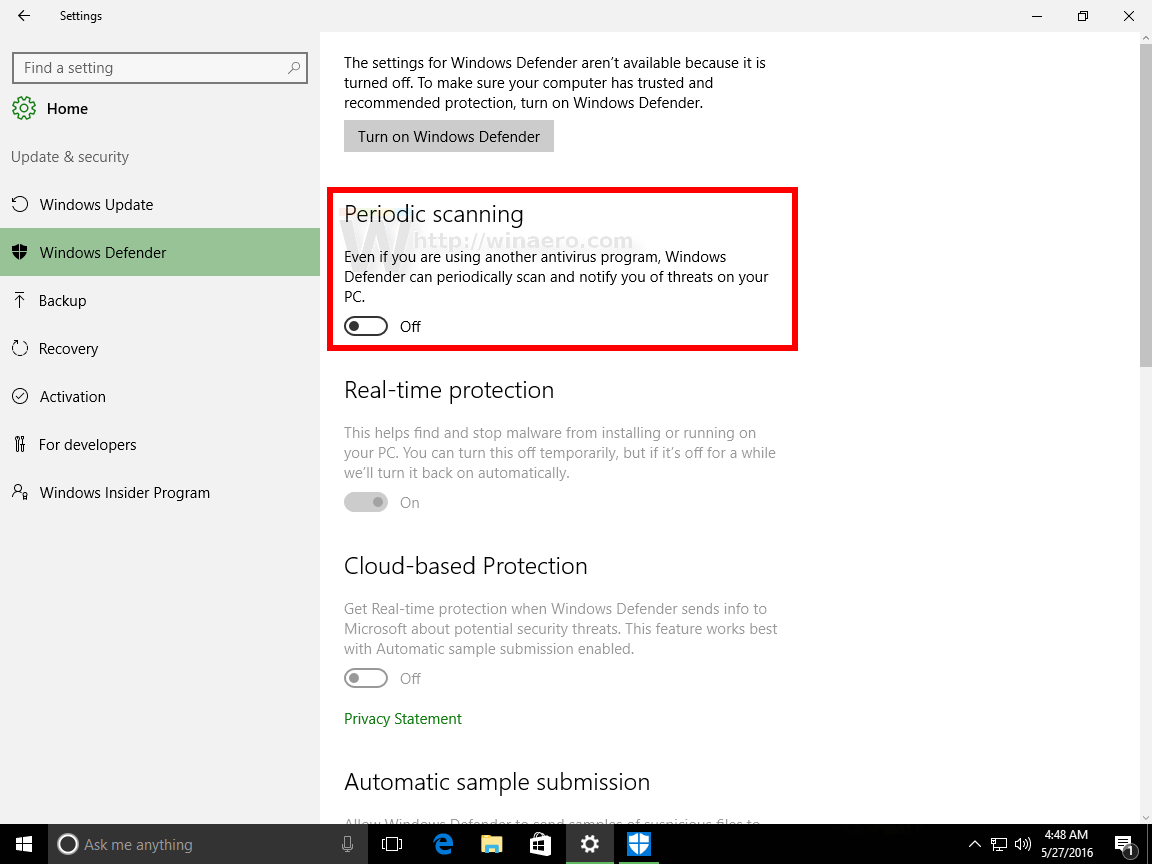
How to start a scan for viruses or malware in Microsoft Defender
Looking for information documentations on doing so.
Comprehensive Cybersecurity and Exposure Management
The scan will also attempt to interact with any Banners or Interfaces it finds to collect information for the KB. Will it automatically scan for Windows 11 vulnerabilities or do I need to do any configuring within the appliance? Translate with GoogleShow OriginalShow Original. Disable interactive log on.We've been trying out Nessus Professional and Nessus Essentials, and found it does a great job scanning systems on a network for vulnerabilities, but can't seem to find how to perform thorough local testing of a system. Example: 'SCAP and OVAL Scan'.To configure a Tenable Nessus scan configuration for Windows logins: The My Scans page appears. Last updated: April 18, 2024 If you are new to Tenable Nessus®, see Get Started with Tenable Nessus. I know I need to set up an audit file and create a compliance policy. Choose Download. Last updated: April 18, 2024 Tenable Nessus Agents are lightweight, low-footprint programs that you install locally on hosts to supplement traditional network-based scanning or to provide visibility into gaps that traditional scanning misses. To create a compliance scan, configure Compliance settings for the scan.On January 14, Microsoft released its first Patch Tuesday of 2020, which contains an update for a critical vulnerability in the cryptographic library used in newer versions of Windows, including Windows 10 and Windows Server 2016/2019.Hopefully, others on this list could provide more experienced guidance on scanning Windows 10 IoT.Some Tenable technologies, like Agentless Assessment, Inventory Scanning, Live Results, and Nessus Network Monitor, allow for more continuous . Generally, this issue is due to one of the .
Vulnerability Management: Five Steps to Cybersecurity Success
On GitLab self-managed .
Host Discovery & Vulnerability Scanning With Nessus
Similar to network device authenticated scan, you'll need a scanning device with the scanner installed.
Scan for Windows 11 vulnerabilities
Tenable Nessus® Get Started with Tenable Nessus. However, it's interesting to note that a significant number of Tenable Nessus users tend towards unauthenticated scans.Learn how to enable the Vulnerability Detector module and set the configuration for running vulnerability scans in this section of the documentation. Run the following commands from an elevated command prompt. Tenable Nessus Professional will help automate the vulnerability scanning process, save time in your compliance cycles and allow you to engage your IT team. Choose a language. If you suspect that your device may have malware you should have Microsoft Defender run a scan. Open Nessus and follow setup wizard to finish setting up Nessus.Allow WMI on Windows . How to Scan with Microsoft Defender Antivirus on Windows 10.
There are a number of automation tools you can use for vulnerability scanning, for example, Nessus Pro.

Expand Computer configuration > Policies > Windows Settings > Security Settings > Windows . To get started with creating a scan, see Create a Scan.