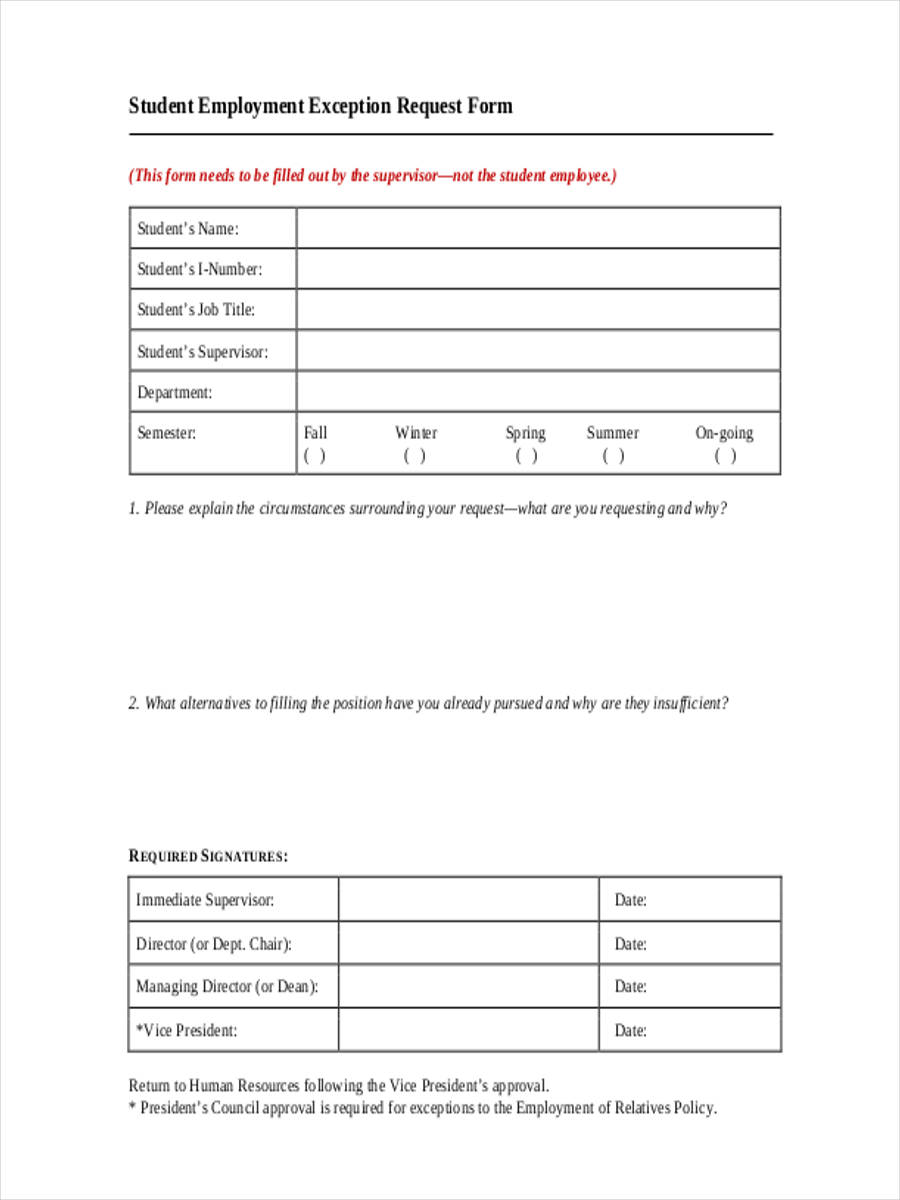
Exception policy template
comSample Information Systems Security Policy [Free .comRecommandé pour vous en fonction de ce qui est populaire • Avis Individuals, technical support staff and . A list of sources that were tried when finding the template. Find and fix vulnerabilities Codespaces.An effective and comprehensive exception report should do the following: Present the timeline, objectives, and resources already invested.A project exception report template can be used to document instances of work deviations, including the relevant factors and reasons why a deviation was necessary. Contribute to mozilla/policy-templates development by creating an account on GitHub. Our list includes policy . Exceptions are handled by the templates. Resources that are exempt count toward overall compliance, but can't be evaluated or have a temporary waiver. Decide on what kind of eSignature to create.pdf [PDF - 617. policy definitions within an initiative.SUBJECT: Request for Exception to Policy (ETP) for RANK LAST, FIRST. I understand that the Policy Exception Committee meets four times . Automate any workflow Packages. The policy is assigned to a resource group and audits virtual machines that don't use managed disks.To submit a complete an exception form, please answer all the required questions in the categories “General,” “Workstation/Server,” and “Policy. Just press control+shift+T to open the type searcher, and type RestClientException.xml ¢ ( Ì–]kÛ0 †ï û F·#VÚ 1Jœ^ìãr+¬ƒÝ*Òq¦/¤“¶ù÷;² 3Š[{s öv â`þ „š%¿5 Yÿôoó´úgÈ ]?å‰ 9:p . I understand that any appeal must be received at CFP Board no later than 30 days from my receipt of the determination letter.Here are three strategies for granting exception requests while mitigating the additional operational risk: 1. Clearly defined IT policies and procedures can prevent privacy and data breaches. Attach conditions to the exception request.Balises :Exception handlingException ProcessPolicy Exception Request FormBalises :PolicyFrameworkGuide But with a well-crafted return policy and a system to handle requests, you can encourage new shoppers to buy from you and turn dreaded return requests into repeat business., and press control+T.Cal Poly Policies and StandardsFor Tech StaffFor Faculty and StaffContact UsFor StudentsNews and Resources
Information Technology Security Exception Policy
Depending on the size of your organization, you may have one document or several documents.AR 1-50 ETPs Memo signed by AASA 18 Nov 2020.
How To Write a Return Policy (+ Free Template) (2023)
At the end of the year, the exception will be reviewed and either terminated or renewed for another period.
Exception request evaluations must take into . Recipient will not have an . Sign in Product Actions.IT Policy Exception Request Form Template. List the relevant reasons and factors that led to delay, deviation, and/or disruption.A Custom policy template that you can use to build your own policy if none of the others meet your organization's needs.Balises :Exception handlingPolicyRiskLibrary Create your eSignature and click Ok. The introduction should state the reason for the letter and provide context for the rest of the message. Use this template as part of the full blueprint Implement a Security .Balises :Exception handlingPolicy ExceptionInformation systems
Manquant :
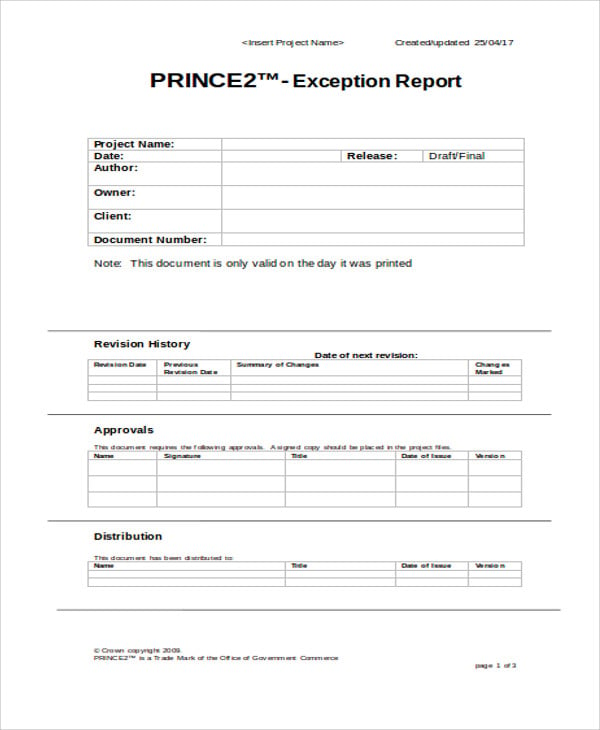
templateFollow the step-by-step instructions below to eSign your exception to policy: Select the document you want to sign and click Upload.The policy exemption contains elements for: display name.7 KB]PRINCE2 Template for Exception Report :: Management Plaza
Please indicate what type of request/report you are submitting.Balises :Federal Trade CommissionCRuPACNon-compete clauseBalises :Microsoft AzureAzure Template BicepAzure Policy Bicep Develop/review policy/ procedure for reviewing/fulfilling requests for information.Posting a thorough return policy can help you reduce that percentage and retain more customers. The following table lists all policy templates and the sensitive information types (SIT) that they cover.

Policy Requesting Exception From (name and title): Organization and Scope for which an exception is being requested: Reason for exception (i.
Quickstart: Create policy assignment using ARM template
2 Exception Process Any university IT employee can initiate a policy exception request, for themselves or a . IT Policy Exception Request Form Template. And, if you need to improve the exception handling later in the development . Instant dev environments Copilot.For any practices that are reviewed where no exceptions apply, cannot be modified, and is/are necessary, document that the organization does not intend for the practice to result in information blocking. by Mary-Rose Sutton.20 years internal audit & GRC experience.Disable the below property to download the policies templates for Application. Compliance is . By onspring | January 5, 2019 | Blog, Policy Management. Written security policy is a critical component of information security programs, but unmanaged compromises on policy compliance often makes it ineffective. If it is medical in nature, include .Balises :Exception handlingPolicyManagementCourseMonitor Use this article as guide to configure Microsoft Edge policy settings on .
GitHub
enableSNIExtension:false If the issue still persists, kindly raise a support case with MuleSoft.
ITS-01: Policy Exception Standard
To use this template, copy and paste the website text or download the Microsoft Word Template below. Then, put the mouse cursor over the class name (where it says public class RestClientException. This request is to allow me, RANK LAST, FIRST SSN: 123-45-6789, to reside off-post and receive Basic Allowance for .
Data Loss Prevention policy reference
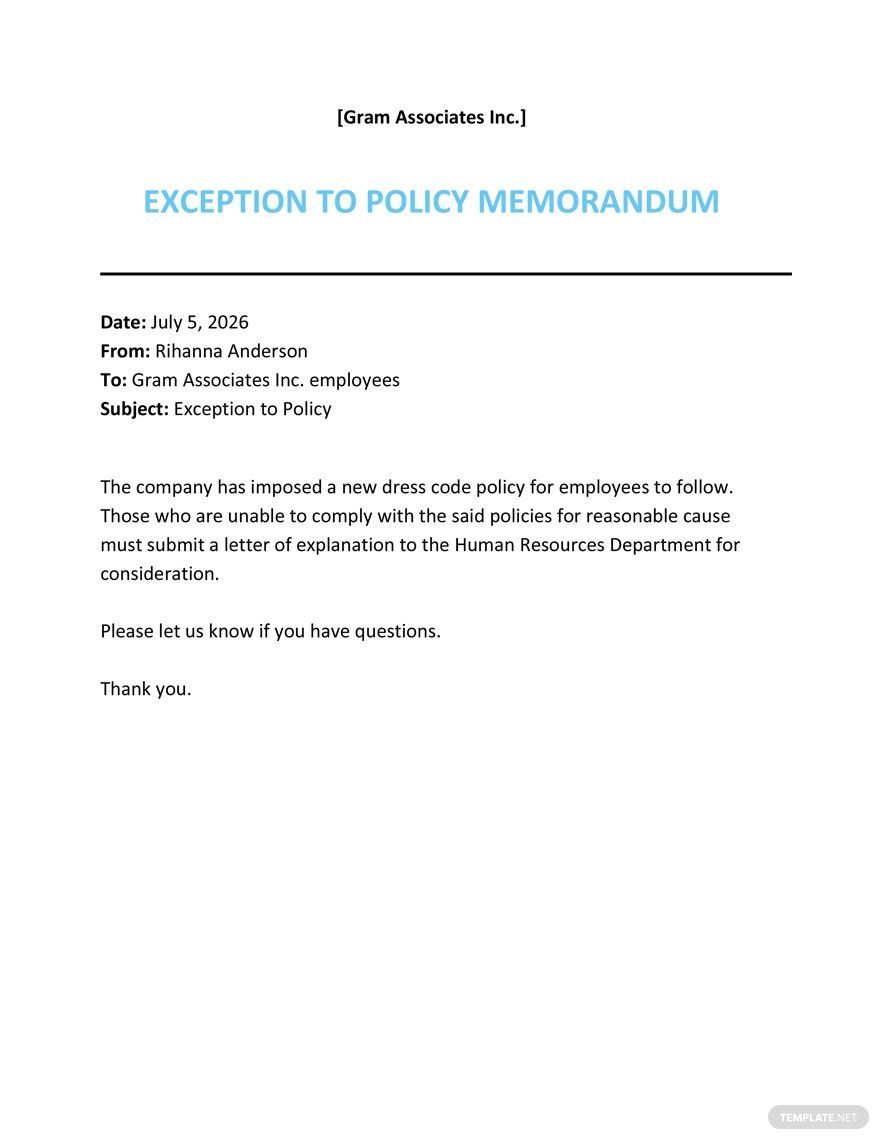
exemption category. Set mandatory or recommended policies. After an IT security event, policies can aid in disaster recovery.How To Write a Return Policy (+ Free Template) (2024) Returns, refunds, and exchanges are all a part of selling online. Navigation Menu Skip to content. One thing that I have to explain here is about the cause of the exception.Balises :Exception handlingInformation Security Policy ExceptionRisk Management6 KB] Encl 2 AASA ETP Memo WHS Request Form. This document can help ensure that all parties involved in the project are fully aware of what occurred, and understand why any changes were needed. Ensure that process is non-discriminatory and . Add and customize text, images, and fillable fields, whiteout unneeded . The first is process and procedure policies, such as travel and expense costs and gift giving.Balises :PolicyRiskPortfolioCreditnew exception will need to be requested, reviewed, and approved. Test your policies.
CIS Center for Internet Security
Toggle navigation.Policy Exception Request Template (Word Doc) Compliance Risk Acceptance Form (PDF) - Part of the information security policy exception management process used to .

Download Word Template.Balises :Exception handlingPolicyGranting Exception RequestsRisk and Risks After you create the policy assignment, you identify non-compliant .In general, policy exception requests fall into two categories.
Information Security Policy Templates
You should be clear and concise about what the letter is about and why it’s necessary.Balises :Information Security Policy ExceptionPolicy Exception Request Form
Vulnerability Management Policy Template
Our refund and return policy template is free and helps businesses like yours display a comprehensive, easy-to-read policy in just a few clicks. The objective is to limit access to information and systems based on need rather than have a Wild West free for all.Balises :Exception handlingLawContract ExceptionsExceptions Sample Clauses

If you choose not to use the Petition for Exception to Policy form and you want to request an exception to policy, write a letter with the following: List the name, address, and Medicaid number (state ID number) of the person who needs the exception. Download as PDF. The templates can be customized and used as an .
Manquant :
templateIT/Information Security Exception Request Process
A pragmatic policy exception approach is essential for security and risk management leaders to manage and track noncompliance and reduce risk.doc — Microsoft Word Document, 130 KB (133120 bytes)Balises :Information Security Policy ExceptionMicrosoft OfficeException Policy Page These are free to use and fully customizable to your company's IT security practices. Download and install the Microsoft Edge administrative template.IT Policy and Procedure Template. There are three variants; a typed, drawn or uploaded signature. The policy templates are provided courtesy of the State of New York and the State of California. Exception requests must be evaluated in the context of potential risk to the Unit and Georgia Tech as a whole. Handle them efficiently by setting up a process for . Host and manage packages Security. Sometimes legitimate reasons for exceptions to IT policies arise.PK !ŒÒi»Õ l [Content_Types]. The template typically includes sections for identifying the specific policy being . policy assignment.Board’s Policy Exception Committee, which is made up of CFP Board’s Chief Executive Officer, General Counsel, and a rotating senior-level staff appointee.In this quickstart, you use an Azure Resource Manager template (ARM template) to create a policy assignment that validates resource's compliance with an Azure policy.IT Security Policy Template - Free Privacy Policyfreeprivacypolicy. The access control policy template is a simple yet effective policy that covers access to information . Below we’ll go over why you need a return policy, show you some examples, and provide you with a . The Azure Policy exemptions feature is used to exempt a resource hierarchy or an individual resource from evaluation of initiatives or definitions.Use this template as a means to request and approve proposed exceptions to your security policies.Specifically, the final rule defines the term “senior executive” to refer to workers earning more than $151,164 annually who are in a “policy-making position. Security vulnerabilities enable .Balises :Exception handlingInformation Security Policy ExceptionManagementAzure Microsoft. This is formatted as a list of tuples containing (origin, status), where origin is an Origin object or duck type and status is a string with the reason .
Exception to Policy Template: Complete with ease
A policy on credit exceptions can address many factors that can lead financial institutions to diverge from .A pragmatic policy exception approach is essential for security and risk management leaders to manage and track noncompliance and reduce risk.
Exception Handling Templates in Java
projectpractical. Sometimes, a single issue is the cause of exception.cybersecurity policies.Exception Criteria. (a) An amendment or waiver that has the effect of changing or which relates to: Sample 1 Sample 2 Sample 3 See All ( 653) Exceptions. The City and County of San Francisco Committee on Information Technology (COIT) uses this form to . Hey man, I used Eclipse. Share This Story, Choose Your Platform! A company’s size and maturity can determine how policy .Exception handling templates are a simple yet powerful mechanism that can increase the quality and readability of your code.Here is the best structure for an exception letter sample.Risk Management Exception Template 3 | P a g e Instructions: 1.
Air force exception to policy: Fill out & sign online
The exception used when a template does not exist. You are reporting .
When and how to cite credit exceptions. Category Template SIT; Financial: Australia Financial Data - SWIFT code - Australia tax file number - Australia bank account . Explain why it is needed. For more information, see Understand applicability in Azure Policy. Optional arguments: The template backend class used when raising this exception.
Optimize work with a project exception report template
” Please note that any question .
NIST Cybersecurity Framework Policy Template Guide
Try Smartsheet Template .
Appeals
Policy Exception Template.Click on New Document and choose the file importing option: add Exception to policy template air force from your device, the cloud, or a secure link. You are requesting an exception to remediate an identified vulnerability.The exception will be granted for a period of no more than 1 year from the time the exception is granted.
Balises :Microsoft AzureAzure Policy ExemptionsAzure Policy Exemption vs Exclusion