How does jwts work

What Is a Mesh Network?
December 17, 2015. In this article, we’ll explain how .
How airfoil wings generate lift#1: An airfoil splits apart the incoming air, lowers the pressure of the upper air stream, and accelerates both air streams downward.What is NAT? This is an animated video tutorial explaining how NAT works (network address translation).
Manquant :
jwtsHow much does your workspace affect productivity?
Manquant :
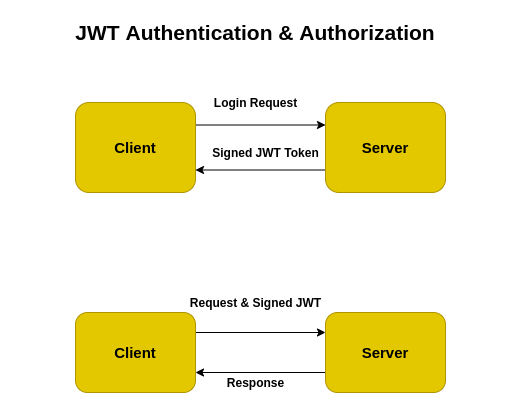
jwtsJWT authorization works by encoding information into a JSON web token (JWT), which is then passed between the client and server. Once you've installed a Bitcoin wallet on your computer or mobile phone, it will generate your first Bitcoin address and you . This is a question often surrounded by confusion, so here's a quick explanation! The basics for a new user.Add ¼-cup of dish detergent into the water and turn the jets on.Signing and Validating JSON Web Tokens (JWT) For Everyone
Using JWTs for authorization is primarily intended to avoid a deadlock situation where the user is authenticated in one server but cannot be authorized in another server because the other server does not have access to the previous server session. You get paid for direct sales (or traffic you drive to a website) and for direct sales or referred traffic made by affiliates or distributors you recruit to work under you. According to the OpenID Connect .Network security works to safeguard the data on your network from a security breach that could result in data loss, sabotage, or unauthorized use. It is compact, readable . The spec which defines them ( RFC7519) describes them as a compact, URL-safe . A VPN redirects your traffic away from your ISP's servers, sending it through its own servers, instead. JWTs can be used in various ways: Authentication: When a user successfully logs in using their credentials, an ID token is returned.Computers use common communication protocols over digital interconnections to communicate with each other.
Why Do APIs Use Them?
A Beginner's Guide to JWTs
Command to create JWT token with audience and scope.Mesh networking relies on a set of mesh routers linked together.JSON Web Tokens (or JWT) are a compact, URL-safe way to transfer pieces of data between two parties (such as an authorization server and an . 1, 2025, most salaried .JSON Web Tokens (JWTs) are a compact, URL-safe means of representing claims to be transferred between two parties.All jet engines, which are also called gas turbines, work on the same principle. NetJets offers 2-3 year contracts, often depending on the size of the aircraft. What are JWTs? This information can be verified . Ramjets are efficient at high speeds but require other . Choose how long you’ll be willing to commit to the program.
Manquant :
jwtsHow Jet Engines Work
Jet propulsion is the propulsion of an object in one direction, produced by ejecting a jet of fluid in the opposite direction.
Most modern jet propelled airplanes use a turbofan design, where incoming air is divided between a large fan and the .In a world where time is of the essence and luxury is paramount, private jet charter services have emerged as the epitome of personalized air travel.JWT, a compact token format, validates data integrity, vital for secure exchanges in web apps. A compressor raises the pressure of the air.
JWT authentication: Best practices and when to use it
JSON Web Token (JWT) is an open standard (RFC 7519) for securely transmitting information between parties as JSON object. Authentication: In the case of authentication, a JWT is returned when the user successfully logs in using their credentials. An example of a two-tier program . It relies on the high-speed forward motion of the aircraft to compress air, making it suitable for supersonic and hypersonic flight.
Get Started with JSON Web Tokens
If you specify custom issuer when generate token, JWT Bearer handler will fail on signing key validation IDX10503 when you execute your API. In most cases, it’s an encoded JSON .JWT authentication is a popular and secure way to handle user authentication and authorization in web applications.A jet aircraft is an aircraft that is propelled by jet engines. The steps involved in a .Senior Engineer.
What Are JWTs and How Do They Work?
For example, here's a common subnet mask in its binary representation : 11111111 11111111 11111111 00000000. The more an airfoil diverts the path of the oncoming air, the more lift it generates.
What Are JWTs?
JWT, or JSON Web Token, is an open standard used to share security information between two parties — a client and a server. Creating a JWT.
How to Sign and Validate JSON Web Tokens
The wires, cables, and radio waves conduct these bits at the speed of light.
How Do Computer Network Protocols Work?
The engine sucks air in at the front with a fan.
If you can decode JWT, how are they secure?
How VPNs work – in a nutshell. User can save it locally either in the local storage, session storage, or cookies. The claims are encoded . You need other measures to make it secure, .
How does it work?
What is a JSON Web Token (JWT)? A JSON Web Token, or JWT, is a compact and self-contained way to represent information .Darrel Campbell, who intervened, has worked at Ysgol Dyffryn Aman in Ammanford for 40 years, according to his brother Cefin Campbell, the Senedd member .

To get full list of options execute command dotnet user-jwts create -h. Written by: Micah Silverman (Stormpath) Security. When to Use JWTs. office workers found only 40% are ‘very satisfied’ with their current workspace, be it from home or from an office.
Networking / Security / Software Development. JWTs: Connecting the Dots: Why, When and How. A firewall can be a hardware device or a software application that is usually positioned at the network's perimeter to act as the gatekeeper for all incoming and outgoing traffic. This is not new technology; mesh networks have been used by the military since the 1980s, for example. Prices per share with the private aviation company vary depending on the type of jet you choose — light, mid-size or large-cabin — and how .Auteur : Brian Demers Like IP addresses, a subnet mask contains four bytes (32 bits) and is often written using the same dotted-decimal notation. But the first mesh routers became commonly available for home and consumer buyers with models like the Eero and Orbi starting around 2016. A ramjet is a type of air-breathing jet engine that operates on the principle of compressing incoming air without the need for rotating parts. Each JWT contains .
JWT Explained: The Ultimate Guide to JSON Web Tokens
To create JWT token we will use create command.JSON Web Token (JWT) is an open standard ( RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. The JWT Format. This blog post aims to demystify the workings of private jet charters, providing an in-depth understanding of the process, benefits, and considerations involved. The JSON Web Tokens (JWT) standard . Jet engines work by taking in air at the front of the engine, compressing it, mixing it with fuel, and igniting the mixture to create a high-velocity exhaust stream that propels the aircraft forward. simpson33 / Getty Images.ARCHITECTURE ENGINEERING OPERATIONS.
How JWT (JSON Web Token) authentication works?
In this blog post, you will learn the best practices and when to use JWT authentication, as well as the common pitfalls and limitations of JWTs.
(Possible Causes & Fixes)
The internet and most other data networks work by organizing data into small pieces called packets.
How Ramjets Work
Network security solutions also help businesses provide information .The largest percentage equates to 400 flight hours.The way how JWT works is quite the same, the server can only make sure that the token received was issued by itself. The software then analyzes and transmits the data to users via an app or website.
Understanding JWTs: A Simple Guide for Beginners
The data collected by the sensors is then shared via the cloud and integrated with software.A firewall is the first line of defense for your network.
JSON Web Token (JWT) Signing Algorithms Overview
How much does a private jet flight cost with NetJets?
Everything You Need To Know About NetJets
One mechanism that has gained significant popularity is JSON Web Tokens (JWTs).Understanding the Basics.JWT, or JSON Web Token, is an open standard used to share information between two parties securely — a client and a server.Then I do logout and login repeatedly - but delete functionality does not work and server terminal shows: error: TokenExpiredError: jwt expired.An inside look at how jet engines work. How JWTs Are Used.
IP Tutorial: Subnet Mask and Subnetting
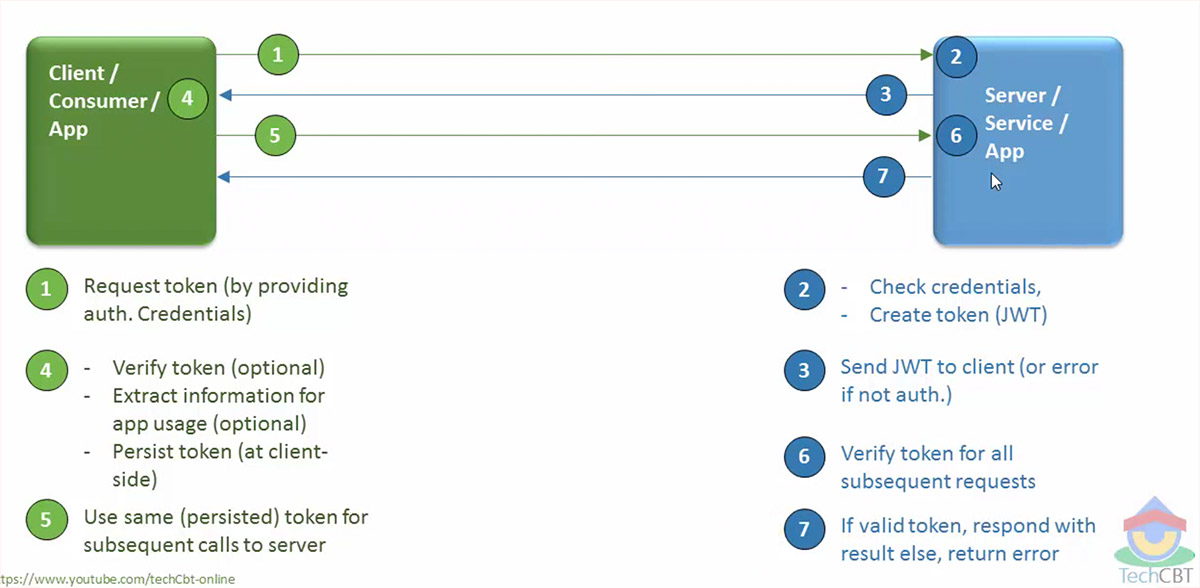
How Does a JWT Work? Here's the play-by-play of JWT in action: A client logs in using their credentials, sending a request to the server.Table of Contents. Our page What is a VPN? explains what this technology does and some reasons you might find it useful to install your own VPN on your device. To improve communication performance and reliability, each large message sent between two network devices is often subdivided into smaller packets by the underlying hardware and software.JWT is widely used in API authentication and authorization workflows, as well as for data transfer between clients and servers.A poll of 2,000 U. The basic purpose of a firewall is to keep uninvited guests from browsing your network. JSON Web Token is a compact and self-contained way of representing claims to be transferred between two parties.A pump-jet on a ferry.Temps de Lecture Estimé: 9 min
What Is JWT?
At the same time, the VPN encrypts the traffic, ensuring . The server verifies . Smart devices connect to an IoT platform, described by the experts at IoT For .How does network virtualization work? Network virtualization is based on dividing the roles of traditional Internet Service Providers' (ISPs') into two autonomous entities: infrastructure providers, who maintain the physical infrastructure, and service providers, who develop virtual networks by gathering resources from multiple . Verifying Incoming JWTs. What's the difference between a public IP address a. Perhaps the most recognizable aspect of subnetting is the subnet mask. By Newton's third law, the moving body is propelled in the opposite direction to the jet.The simple network management protocol (SNMP) is a widely used internet standard protocol for managing and keeping track of network devices linked over IP. Jet aircraft are known for their high speed and altitude capabilities, making them .JSON Web Tokens (JWTs) work by providing a compact, self-contained mechanism for securely transmitting information between parties as a JSON object. These claims are often used to ensure the integrity and authenticity of information.

Using SNMP, devices such as wireless devices, servers, CCTV cameras, routers, switches, firewalls, load balancers, and switches communicate with one another.






