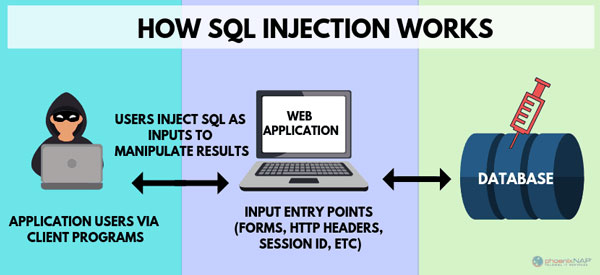
How to scrub for sql injection

SQL injection (SQLi) is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. Here are a few ways to do that—they will be eff...
SQL injection (SQLi) is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. Here are a few ways to do that—they will be effective against SQL injection and many other vulnerabilities that can affect your Python code.If SqlAlchemy hadn't overloaded the python operators like ==, then Python would evaluate the == before a method like filter () receives anything. The OP asked how can i perform[. It’s kind of like a . Finding SQL Injections. The best you can do is to whitelist the parameters you can use, which means you don't use any parameters that come from untrusted sources in . So SqlAlchemy has overloaded the python operators like == to return Sql statements wrapped in python objects. If your intent is to allow users to execute arbitrary SQL, then it would seem like you wouldn't be too worried about SQL injection (since that is the aim . SQL stands for Structured Query Language. The main purpose of this attack is to get the database to behave in an undesirable or insecure manner.well, with non-sanitized data that might be used in sql statements a sql injection would be the first scenario for the malicious hacker that sees like the input .
python
Escaping output. This might result in the database displaying confidential data or allowing an unauthorized user to modify, add, or delete data.This is intended as a brief guide to protecting your MySQL database from SQL injection attacks. SQL injection cheat sheet.Stack Overflow Public questions & answers; Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers; Talent Build your employer brand ; Advertising Reach developers & technologists worldwide; Labs The future of collective knowledge sharing; About the company Unfortunately, a large amount of the code that I’ve seen written by people on forums, and in countless crappy PHP tutorials lurking around on the net, and in the many websites that display the magic breeding slashed-quote (''' see below) show that many . SQL injection is a common attack vector that remains one of the most prevalent security risks for applications today.NET SQL injection is a security weakness in a .At the moment your site is still susceptible to various . It's all too easy to leave yourself vulnerable to these attacks, regardless of which version of ASP., delete, select or drop) could be used in common language.@AbeMiessler : Yes sure, but the answer should be clear on the fact that it's not always possible to UPDATE/DELETE/INSERT. The most important way to prevent SQL injection is to avoid vulnerable code and insecure coding practices. After discovering this object injection vulnerability, the WordPress team quickly issued an update that addresses this security issue. Some web development practices use a dictionary of banned words (blacklists) as an SQL injection prevention. Luckily for us, I've already written a tutorial about extracting and filling forms in Python.
What are good ways to prevent SQL injection?
A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application. WordPress uses SQL to retrieve critical information from your .SQL injection explained. When it comes to protecting your WordPress website, the number one piece of advice is always the same: keep your site up-to-date. In fact, you don't even need to be using ASP. This can be used to retrieve some sensitive . public static Boolean checkForSQLInjection ( string userInput) How to safely execute queries in a database. Injection, but validation has its own set of problems and sometimes requires a complex set of logic code to determine if .@marc_s: Parameterized queries are only a partial solution. One way to reduce the risk of SQL injection is to check the type of input you expect from your users, such as numbers, text, dates, or email addresses. Insecure Packages.

Parmi les approches utiles pour prévenir les attaques par injection SQL figurent la restriction des procédures de base de données, l'assainissement des entrées de base .
Data Security: Stop SQL Injection Attacks Before They Stop You
NET SQL injection. We gonna need the below functions: def . This can be used to retrieve some sensitive information, like database structure, tables, columns, and their underlying data.SQL injection is the lowest of the low-hanging fruit for both attackers and defenders.
Manquant :
scrubsanitize data for SQL with JavaScript
Manquant :
scrub Using prepared statements, or/and filtering with mysql_real_escape_string is definitely a must.SQL Injection Prevention
Rather, as @Donal says, what you need is the parameter substitution concept of the Python DB API -- that makes things db safe as you need. Keep WordPress Core Up-to-Date.1 Validate input types.Mar 24, 2010 at 3:01. However, to answer your question your clean method seems to be missing the fundamental trigger for SQL Injection - unescaped characters. A SQL injectionattack involves the injection/insertion of untrusted data into a SQL query, causing a transition from the . SQL injection usually occurs when you ask a user for input, like their username/userid, and instead of a name/id, the user gives you an SQL statement that you will unknowingly run on your database. Adding this method returns true and false.

An SQL Injection is a code injection technique that attackers use to exploit vulnerabilities in a website or application’s database layer.The five key methods to prevent SQL injection attacks include: Filter database inputs: Detect and filter out malicious code from user inputs. The only proven way to protect a website from . That is poor practice in most cases.So what should we do? Make sure the data is never in a position to do harm.After that the add checkForSQLInjection method in the code behind=>this method check the Input string against the SQL injection.Since SQL injection is all about user inputs, we will need to extract web forms first.It's impossible to detect SQL injection after the fact (in other words, once you've constructed a dynamic query string, it's impossible to differentiate what the real SQL is versus any injected SQL). The proper way to sanitize data for insertion into your database is to use placeholders for all variables to be inserted . Look at the following example which creates a SELECT statement by adding a variable (txtUserId) to a select string. Any procedure .
Manquant :
scrubHow to cleanse (prevent SQL injection) dynamic SQL in SQL Server?
Affected is an unknown function of the file .Despite its reputation, how to prevent SQL injection remains one of the leading vulnerabilities, and attacks continue to grow.NET you are using.To prevent SQL injection in different programming languages and frameworks, consider the following suggestions: In Java EE, you should use PreparedStatement() and bind .What Python SQL injection is and how to prevent it.Exemple d'utilisationstatement = insert into mytable (id, name) values (' + theId + ', ' + theName + ')See more on stackoverflowCommentairesMerci !Dites-nous en davantageNET application that lets hackers take control of the software’s database by tricking the application into sending unauthorized SQL commands.

How to Prevent SQL Injection: A Complete Guide
NET SQL injection is made possible by an application that uses untrusted data from a web form .I think the only reliable way you will prevent SQL Injection would be to put the hard work in and convert all the requests to use SQL Parameters. For example, suppose an application uses the following query to fetch someone’s login details:SQL in Web Pages. One of the reasons SQL injection attacks are so pervasive is the fact that injection vulnerabilities are very easy for attackers to discover and exploit, sometimes with devastating consequences. You will learn the basics of SQL injection, how to exploit it, and how to use various tools and techniques to protect your data. You can use built-in .Security teams can address many other kinds of injection attacks, like SQL injections and cross-site scripting (XSS), by clearly separating system commands from . 1) User input should always be assumed to be bad.escape makes a string re -safe -- nothing to do with making it db safe. The first and simplest approach for SQL injection is the approach to end the current string and statement by starting your value with a single or double quote . Restrict database .4 Tips for Preventing SQL Injection in Python.Yes, you could validate each of the user inputs to scrub the data for SQL.How Applications Become Vulnerable to SQL Injection? It's always a good idea to sanitize the input before sending it to the database.
How to Prevent SQL Injection: 5 Key Prevention Methods
How to compose queries with both literals and identifiers as parameters. It’s kind of like a situation when we can push some custom .SQL injection is an attack in which malicious code is inserted into strings that are later passed to an instance of SQL Server for parsing and execution.Preventing SQL Injection Using Parameters.SQL Injection Tutorial: Learn with Example is a comprehensive guide that teaches you how to prevent and detect SQL injection attacks on web applications.SQL injection occurs when an attacker inserts malicious SQL code into a query, bypassing the intended security measures and gaining unauthorized access to the application’s database. Then, we’ll show you five tactics that you can implement to avoid falling victim to one.
SQL Injection: A Detailed Guide for WordPress Users
SQL injection is a web security vulnerability that allows an attacker to alter the SQL queries made to the database.
PHP also has filter_input built in which is a good place to start.escape (title) to add escape chars into the strings to make them db safe.
Manquant :
scrubComment prévenir les attaques par injection SQL
If a user sends a malicious javascript code into your form, and you store it successfully in your database, and you display the same . The variable is . They don't protect against SQL injection into a dynamic SQL query, javascript injection into a varchar field, . I believe there are three different cases that you have to worry about: strings (anything that requires quotes): '''' + replace(@string, '''', '''''') . Parameterized queries might save you from SQL injection attacks, but might not prove beneficial in case of stored XSS attacks.
Manquant :
scrubHow can I sanitize user input with PHP?
Dec 18, 2018 at 20:04.

The best way to achieve this is to avoid interpretation of the data in the first place.ProgrammingSecuritySQL. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete), execute administration operations on the database (such as shutdown the DBMS), recover the . Let’s dive right in! An introduction to SQL injection WordPress attacks. 2) This is a large topic, and it depends on the context of the data being output.What is SQL Injection. The boolean won't result in a useful SQL query.The SQL (structured query language) injection is a well-known, if not, one of the best known, software weaknesses and security vulnerabilities.Critiques : 1
Tutorial & Examples
Manquant :
scrubSQL Injection and How to Prevent It?
This tutorial is suitable for beginners and professionals . And it would result in a boolean.