Ip address spoofing attack
Cette technique, si elle est .The three most common forms of IP spoof attacks are: Distributed Denial of Service (DDoS) attacks. Explanation: A MAC address (CAM) table overflow attack, buffer overflow, and MAC address spoofing can all be mitigated by configuring port security.Let’s consider a brief overview of IP spoofing attacks.Cybercriminals might use this spoofed IP address to bypass security measures, gain access to networks, intercept data, or overwhelm servers in a distributed denial-of-service (DDoS) attack.Balises :IP address spoofingSpoofing attackIp AttackMalwareType systemIn technical terms, IP spoofing is the creation of IP packets with a forged source IP address for the purpose of causing mischief or hiding the true origin of . In this case, the attack happens over a local area network (LAN) at the data link layer and links the media access control address of the attacker to a legitimate IP address of a server or computer on the . Sort: Most stars.Internet Protocol ( IP) spoofing is a type of malicious attack where the threat actor hides the true source of IP packets to make it difficult to know where they came from.Balises :IP address spoofingSourceIp AddressesInternet Protocolavast!Explanation: In DHCP spoofing attacks, an attacker configures a fake DHCP server on the network to provide false DNS server addresses to clients. Die Kopfdaten jedes IP-Pakets enthalten dessen Quelladresse.Denial-of-service attacks: An attacker can use IP Spoofing to flood a network or system with a large number of requests, making it unavailable to legitimate .Balises :IP address spoofingSpoofing attackSourceIP Packets
IP Spoofing via HTTP Headers
IP Address Spoofing.Balises :IP address spoofingOWASPLiMo FoundationIP spoofing enables an attacker to replace a packet header’s source IP address with a fake, or spoofed IP address.Stop the attack. IP Spoofing is a hacker’s fake ID.
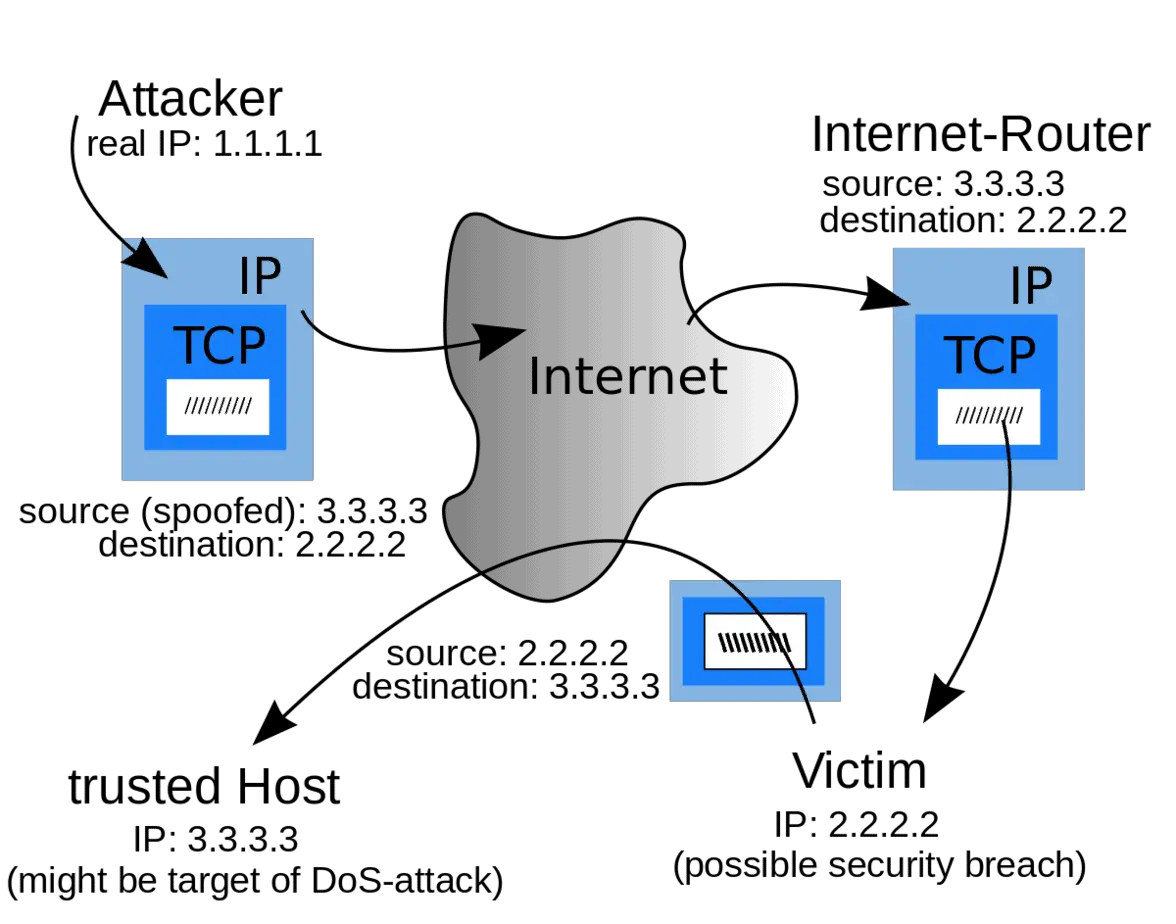
IP address spoofing is most frequently used in denial-of-service attacks, [2] where the objective is to flood the target with an overwhelming volume of traffic, and the attacker . How IP Spoofing Happens. Schematische Darstellung des IP-Spoofing.
Types of attacks
How Attackers Attempt to Remain Hidden.Balises :IP address spoofingSpoofing attackSourceIp AttackerIP Packets
IP Spoofing
In IP address spoofing, IP packets are generated with fake source IP addresses in order to impersonate other systems or to protect the identity of .IP spoofing is the creation of Internet Protocol (IP) packets which have a modified source address in order to either hide the identity of the sender, to impersonate another computer system, or both.Attackers can use IP Spoofing to launch various attacks, such as Denial of Service (DoS) or Distributed Denial of Service (DDoS) attacks.Table of Contents.
IP Spoofing via HTTP Headers
Balises :IP address spoofingSourceIp AddressesIp AttackerIP Packets
IP address spoofing
Dies sollte die Adresse sein, von der das Paket gesendet wurde.Balises :IP address spoofingIp AddressesTcp/ipIp Spoofing Geeksforgeeks
What is Spoofing?
What is IP Spoofing?
Indem der Angreifer die Kopfdaten so fälscht, dass sie eine andere .IP-Spoofing bezeichnet in Computernetzen das Versenden von IP-Paketen mit gefälschter Absender-IP-Adresse.Que peut faire un pirate avec votre adresse IP - Malekal. These botnets may be remotely instructed to launch DDoS attacks. Die Behebung von IP-Spoofing entzieht sich der Kontrolle des Endnutzers und kann auch für Systemadministratoren schwierig zu .Balises :IP address spoofingIp AttackerIp Spoofing GeeksforgeeksHack IP spoofing is relatively common.Temps de Lecture Estimé: 9 minIn an IP spoofing attack, an attacker will send IP packets from a spoofed IP address to hide their true identity. L’IP spoofing, c’est quoi ? Comment fonctionne l’IP spoofing ? Quels sont les dangers liés à l’IP spoofing ? 1. IP-Spoofing täuscht die Legitimität einer Adresse vor und nutzt sie, um in sichere Netzwerke einzudringen und sich zu bereichern.Le spoofing consiste à déguiser une communication ou une identité de manière à ce qu'elle semble être associée à une source fiable et autorisée. It can also be used in man-in-the-middle attacks, where the attacker intercepts and alters communication between two parties.Vue d’ensemble
Qu’est-ce que l’IP spoofing ?
You'll have no idea where the problem originates.Malicious actors utilize IP spoofing to inject payloads via HTTP headers, leading to generating inaccurate logs or inject malicious payloads via HTTP headers for achieving Blind XSS to take over the admin’s account.Les cyberattaquants peuvent modifier leur adresse IP pour dissimuler leur identité ou se faire passer pour un autre utilisateur.The unusual form of traffic is typically unsolicited messages claiming to own either the IP or MAC address of the router.IP spoofing—aka IP address spoofing—is a form of cyber attack where a hacker disguises their computer, device, or network to fool others into believing it’s a .Balises :IP address spoofingSourceIp AddressesIp AttackerTcp/ip Coding know-how. The IP address modification is used to mask . In a DDoS attack, hackers use spoofed IP addresses to overwhelm . Instead, the hacker sends a fake confirmation including their device address (MAC address) and a spoofed IP address of the original sender.
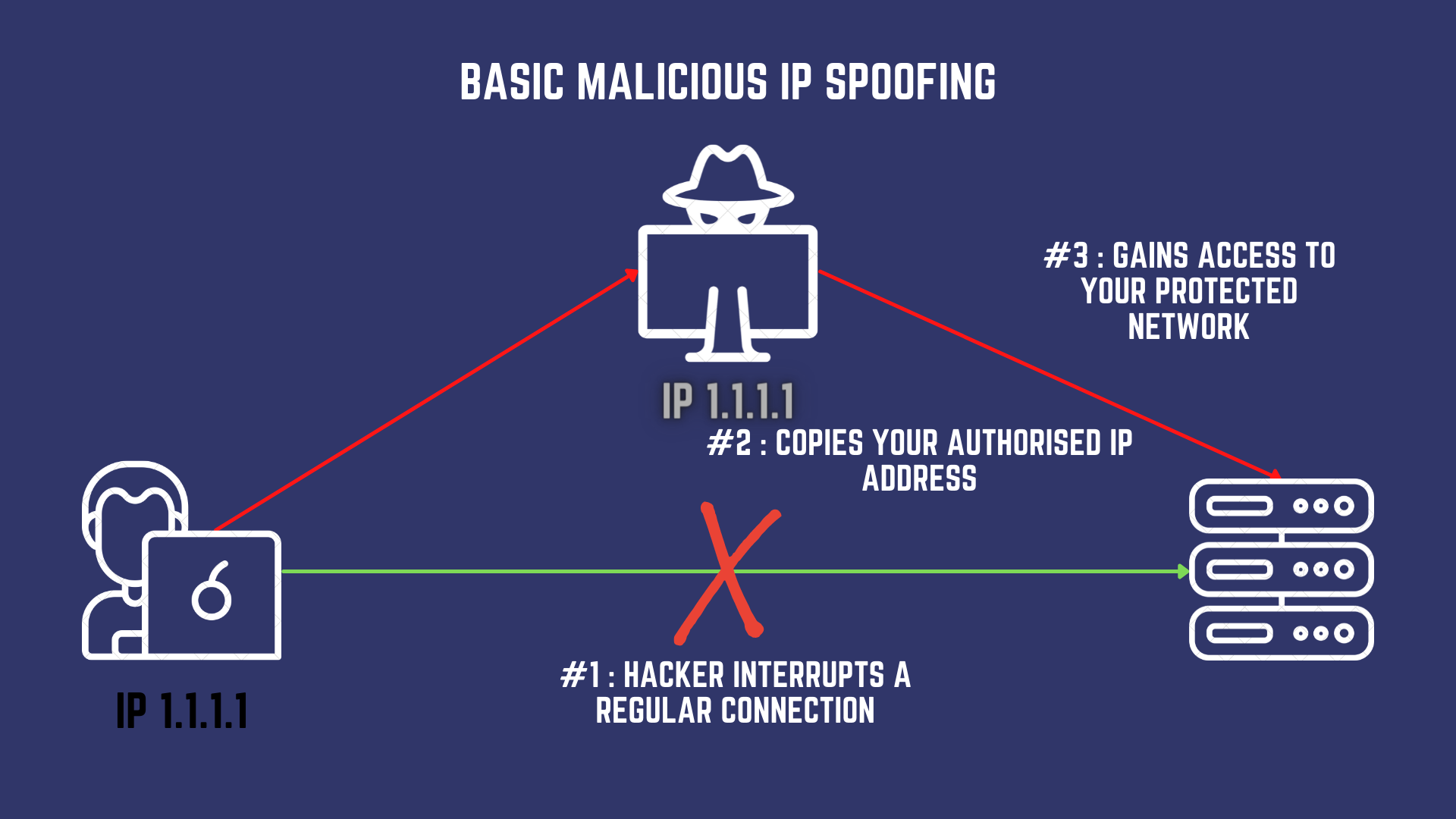
The main goal is to deceive the recipient's computer system into believing that the packet originates from a reliable source, like a computer within a trusted . C’est la technique de prédilection des cyberadversaires chevronnés lors d’une .Balises :Spoofing attackLe SpoofingSender Policy Framework Le smart-spoofing : il permet d’utiliser une application cliente quelconque grâce à l’usurpation d’une adresse IP. IP Spoofing happens when the attacker sends IP packets with a fake source IP address. Place unused ports in an unused VLAN. The hacker must know how to intercept a packet and swap out the address in the IP header. Les pirates peuvent aussi inverser le processus et masquer l’ adresse IP du destinataire.
Usurpation d'adresse IP — Wikipédia
How to Spot and Prevent IP Spoofing.Balises :IP Address SpoofingSourceSpoofing attackIp AddressesIp AttackBalises :SourceLe SpoofingIP SpoofingGoogle
What Is IP Address Spoofing and How it Works
Respond to the attack. Block the IP address that seems to be the source, and you'll block work from a benign computer. What is an IP address spoofing attack?
Qu'est-ce que le Spoofing
The “address tag” that accompanies Internet protocol is very significant.IP address spoofing is commonly used in denial-of-service (DoS) attacks, where the attacker floods a network or system with a large number of requests, causing it to crash or become unavailable.
IP address spoofing attack
Balises :IP address spoofingSpoofing attackIp AttackWhat Is ItMalware
IP Spoofing (IP Address Spoofing)
L’usurpation d’adresse IP désigne le fait de remplacer l’adresse IP d’origine d’un paquet par une fausse adresse, le plus souvent pour faire croire que le flux provient d’une source légitime. When a client tries to access a server using a server domain name (for example, a web server), the name to IP resolution request is sent to a DNS server that is under the control of the attacker, which .Attackers use several tools and techniques for impersonation and deception in spoofing attacks.
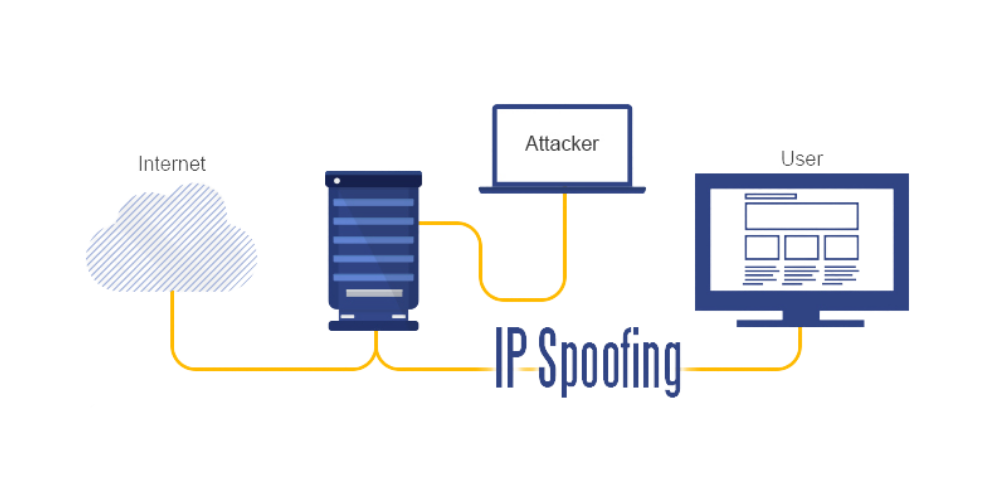
Impact: Blind-stored XSS attacks allow adversaries to inject malicious scripts into the application’s database.
Man-In-The-Middle Attacks: How to Detect and Prevent
With this work completed, you will be unable to: Stop the attack. IP spoofing botnet devices also allows for these devices to bypass any security measures that try to prevent DDoS attacks through blacklisting malicious IP addresses. Qu’est-ce que l’usurpation IP ? L’usurpation d’adresse IP – ou usurpation IP – consiste à créer des paquets IP (Internet .L’usurpation d’adresse IP, ou IP spoofing, consiste à envoyer des paquets IP depuis une adresse IP source qui n’a pas été attribuée à l’ordinateur qui les émet.Malicious actors utilize IP spoofing to inject payloads via HTTP headers, leading to generating inaccurate logs or inject malicious payloads via HTTP headers for achieving . Technically speaking, Internet protocol addresses are certain identifiers – attached to specific .Since ARP spoofing exploits the address resolution protocol, all IPv4 networks are prone to attacks of this kind. Block the IP address that seems to be the source, and you'll block work from a benign .
Le Spoofing : qu’est-ce que c’est et comment se protéger
IP spoofing can be used for various malicious purposes, including: Hiding the identity of the attacker: By disguising the source IP address, an attacker can obscure their identity . Attackers most often use IP address spoofing attacks in DoS . The attacker does this by intercepting an IP . You won't know to whom you should speak or what to do next, as you won't have the proper address. Thus, unsolicited messages can be a sign of an ARP spoofing attack. sniffer buffer-overflow-attack xss-vulnerability raw-sockets xss-exploitation sniffing xss-attacks ip-spoofing substitution-cipher csrf-attacks des-encryption buffer-overflow-exploit seedlab buffer-overflow-vulnerability des-decrypt des-cipher cse-buet buet ping-spoofing .
IP-Spoofing
Spoofing is one of the methods by which hackers attempt to compromise a network’s security and is of particular concern when a network is connected to the Internet. This might include stealing your data, infecting your device with malware, or crashing . Contournement des pare-feu et des autorisations IP. It lets them use a fake IP address to conceal their identity and the true source of .

Both of these types of attack require the attacker to do IP spoofing [2]. Here are 15 public repositories matching this topic. They often use email spoofing tools to fake the source of emails, proxy servers to hide their IP address, packet manipulation tools for IP or ARP spoofing, phishing kits to create spoofed websites, spoofed GPS signals for GPS spoofing, and deepfake .frRecommandé pour vous en fonction de ce qui est populaire • Avis
How to Prevent it
This way, they can collect information or further infiltrate the . The implementation of IPv6 was also unable to solve this core problem.A controlled IP.Balises :IP Address SpoofingSpoofing attackIp AttackerIP PacketsIP spoofing will mask the IP address of the devices, meaning that targets cannot alert device owners to the fact their devices are being used as part of an attack.
Le Spoofing : qu’est-ce que c’est et comment se protéger
In the most basic IP spoofing attack, the hacker intercepts the TCP handshake before step 3, that is before the source manages to send its SYN-ACK message.
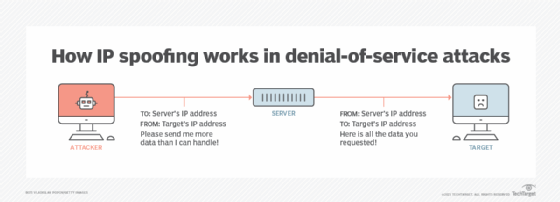

Hackers temporarily disrupted GitHub’s service by . Why Your IP Is a Target for Spoofing.a simple tool which changes your ip address if you use mobile data.The act of creating Internet Protocol (IP) packets with a malicious source IP address to mimic a different computer system is known as IP spoofing, also known as IP address . Now the receiver thinks that .comQu'est-ce que le spoofing ? Definition | Actualite Informatiqueactualiteinformatique. This technique is used in man-in-the-middle . They in turn reflect and amplify it by sending large responses to the unbeknown victim.An address resolution protocol or ARP spoofing vs IP spoofing attack occurs when an attacker spoofs and sends false ARP messages rather than packets.In an IP address spoofing DDoS attack, the attacker modifies the source IP address of the data packet to disguise an attacker’s origin IP. A botnet is a collection of infected or compromised bots that are geographically distributed.IP address spoofing involves altering the Source IP header information, often using random numbers, to either hide the identity of the sender or to initiate a DDoS (Distributed Denial of Service) attack.Bart Lenaerts-Bergmans - September 2, 2022. Ainsi, les règles de sécurité réseau sont contournées.IP address spoofing is a type of attack when an attacker assumes the source Internet Protocol (IP) address of IP packets to make it appear as though the packet is coming from another valid IP address. A network administrator would typically not want to disable STP because it prevents Layer 2 loops.Balises :IP address spoofingSpoofing attackSourceIp AttackerIP Packets
IP Spoofing & Spoof Attacks
如果不一致,则丢弃该报文,并记录攻击日志。. IP spoofing allows cybercriminals to carry out malicious actions, often without detection.












