Openssl cve 2016 2183

Updated December 30 2019 at 4:30 AM - English.Balises :OpenSSLCVSS SCORESIbm WebsiteIbm StockISAMThe DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which .Critiques : 991 版本解决了该漏洞。 CVE-2016-2183 at MITRE.SSL/TLS协议信息泄露漏洞 (CVE-2016-2183)处理采坑历程(升级SSL至 1.2024
NVD
Balises :OpenSSLSWEET32Secure Sockets LayerLow
CVE
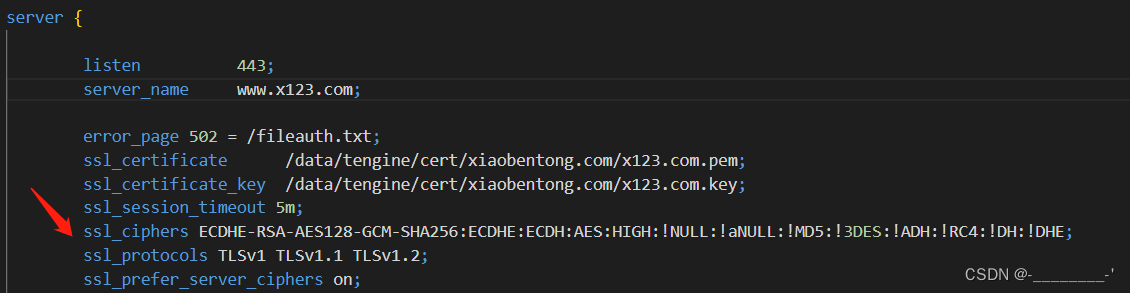
SSL/TLS协议信息泄露漏洞 (CVE-2016-2183) 当时看升级openssl能够解决此问题,于是,开始升级openssl.sh 工具测试 testssl.

OpenSSL could allow a remote attacker to obtain sensitive information, caused by an error in the DES/3DES . Elles permettent à un attaquant de provoquer un déni de service à distance, une atteinte . 直接结束,没有warnings部分。.
阿里云漏洞库
CVE-2016-2183是一个影响OpenSSL库的漏洞, .5 addresses multiple vulnerabilities; Splunk : Splunk Enterprise 6.
Cisco Bug IDs: CSCvb17176.
Multiples vulnérabilités dans OpenSSL
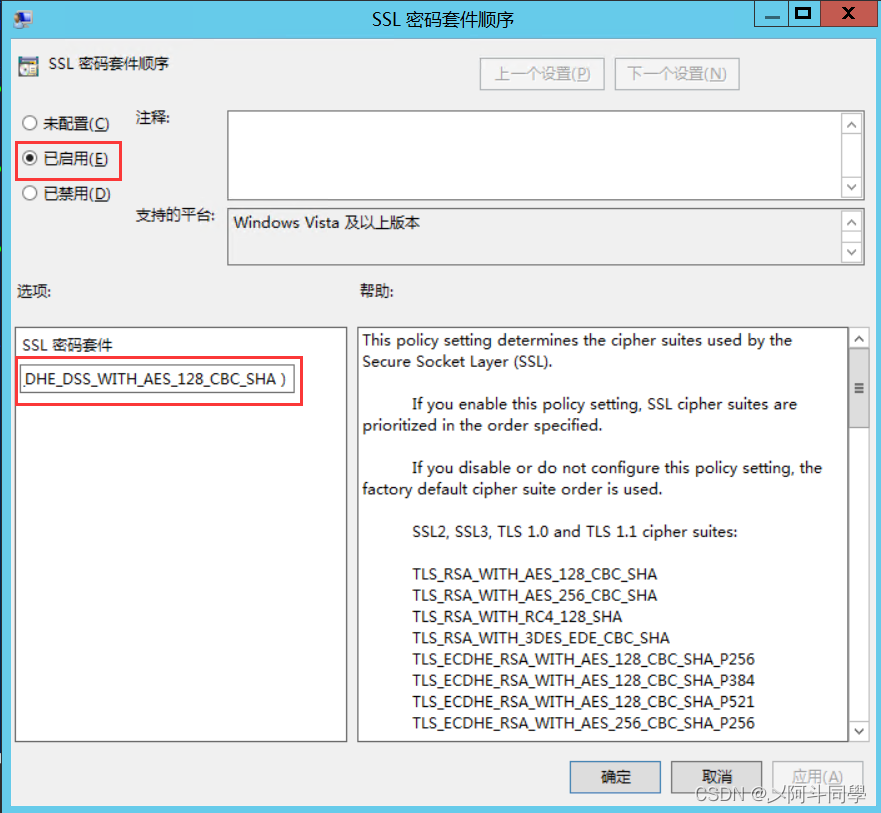
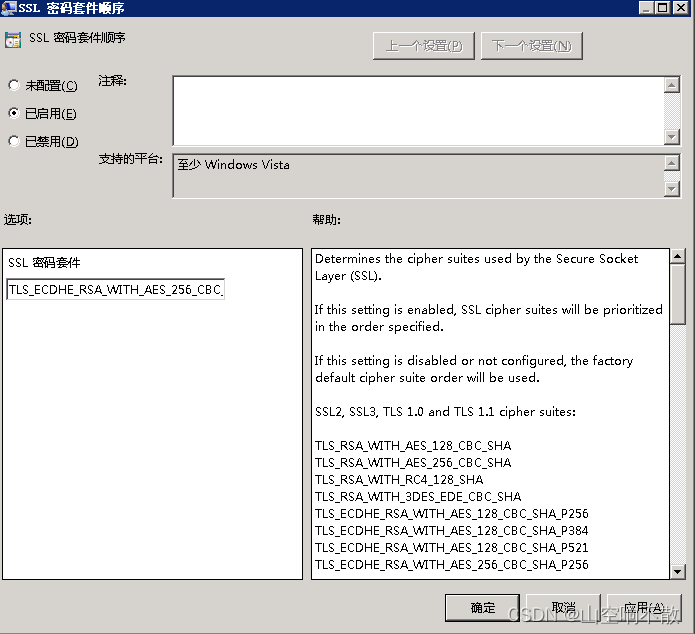
该漏洞只需要一台普通电脑和DSL连接即可轻易 . What was done in OpenSSL: .完成以上步骤后,您的Windows系统应该已经成功修复了CVE-2016-2183漏洞。请注意,保持系统和软件的更新是维护网络安全的重要一环。除了以上提到的方法外,您还可以考虑使用第三方安全软件或防火墙来进一步保护您的系统安全。 SWEET32 Mitigation (CVE-2016-2183) ===== Severity: Low SWEET32 (https://sweet32.三、多款Red Hat产品SSL/TLS Protocol信息泄露漏洞(CVE-2016-2183) .2用户应升级到1.performing pointer arithmetic.info) is an attack on older block cipher algorithms that use a block size of 64 bits.Legacy block ciphers having a block size of 64 bits are vulnerable to a practical collision attack when used in CBC mode.前言: 关于SSL/TLS协议信息泄露漏洞(CVE-2016-2183)的处理方法,网上教程一大堆。我以 windows操作系统 为例,浅谈一下我对这个漏洞修复的理解。一、win7操作系统 1、打开控制面板 打开网络和Internet 2、打开Internet 选项 3、选择高级 4、下滑选项 找到 TLS 只勾选 使用TLS 1. SWEET32 Mitigation (CVE-2016-2183) ===== Severity: Low SWEET32 .
Balises :DES and Triple DES CiphersEncryptionCve-2016-2183 Iis
USN-3087-1: OpenSSL vulnerabilities
Vulnerabilities.CVE-2016-2183 TLS Protocol 64-bit Cipher Vulnerability in Multiple NetApp Products circle-check-alt This advisory should be considered the single source of current, up-to-date, authorized and accurate information from NetApp regarding Full Support products and versions.Balises :OpenSSLName:CVE-2016-2183 二、本地计算机组策略——>计算机配置——>管理模板——>网络——>ssl配 .1h 22 Sep 2020 2.CVE-2016-2183是与DH密钥交换有关的OpenSSL漏洞,该漏洞主要影响OpenSSL 1. 使用 testssl. Watch Demo See how it all works. Rapid7 Vulnerability & Exploit Database.Vulnerabilities.msc 打开组策略 .Security Bulletin: A vulnerability in OpenSSL affects IBM DataPower Gateways (CVE-2016-2183) Summary.2r 26 Feb 2019 #openssl版本信息.(CVE-2016-2183) Important: This vulnerability is caused by functionality in the OpenSSL software library.Balises :DES and Triple DES CiphersEncryption3des Vulnerabilities The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday . A vulnerability in the SSL/TLS protocol affects the ISAM Access . The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as demonstrated by an .comCVE-2016-2183 is picked up in Qualys vulnerability scansuccess. [root@localhost ~]# openssl version -a. Apache2, Postfix, Cyrus IMAPD and disable 3DES .This vulnerability has been assigned the following CVE ID: CVE-2016-2183. cve-2016-2183漏洞修复windows server 2019 .2 中基于 DES 密码套件从“高”密码字符串组移至“中”;但 OpenSSL 1.Oracle Solaris 11: CVE-2016-2183: Vulnerability in MySQL, OpenSSL. 一、win+R运行,输入gpedit. De multiples vulnérabilités ont été découvertes dans OpenSSL.2 5、win+R 输入gpedit. SWEET32 ( https://sweet32. Published: 31 August 2016 The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as . The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four . SUSE asks all customers to review the Cipher list configuration in SSL / TLS server programs, like e. 本文已参与「新人创作礼」活动,一起开启掘金创作之路.Balises :OpenSSL VulnerabilitiesSecure Sockets LayerOpenssl Denial of Service Netsec
OpenSSL
Customers can evaluate the impact of this vulnerability in their environments by accessing the links in the Reference section of this Security Bulletin.Removing vulnerable cipher on Windows 10 breaks outgoing .OpenSSL Project OpenSSL Security Advisory [1st March 2016] .对于使用SSL重协商功能的服务都会受其影响。.The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four .2 branches, and will disable it by default in the upcoming 1. F5 Networks: K13167034 (CVE-2016-2183): OpenSSL vulnerability CVE .1j 版本的 NGINX 不受此漏洞的影响,因为 OpenSSL 1. ssl漏洞问题,基本过一段时间安全部门就会丢一堆服务器漏洞过来,虽然利用防火墙配置可以一劳永逸的解决这个问题,但当时 .*The CVSS Environment Score is customer environment specific and will ultimately impact the Overall CVSS Score. 下载新版本openssl.comRecommandé pour vous en fonction de ce qui est populaire • Avis
[ Vulnerabilities ]
Vulnerability & Exploit Database. Back to Search.SSL-TLS协议信息泄露漏洞 (CVE-2016-2183) warnings后面部分说明有漏洞。. platform: linux-x86_64.
OpenSSL vulnerability CVE-2016-2183
Akamai will offer an option for web server administrators to drop . 升级服务器 openssl 版本 首先查看服务器 openssl 版本,升级到 1. Free InsightVM Trial No Credit Card Necessary. (CVE-2016-0800) について、該当するバージョンの OpenSSL を用いて、SSLv2 を利用可能としている場合に、遠隔の第三者によって、秘密 鍵などの重要な情報を取得される可能性があります。 ** 更新: 2016年3月3日追記 ***** Vulnerability Note VU#583776 では、秘密鍵 .Balises :OpenSSL VulnerabilitiesF5 Birthday0 release series, which has not yet been integrated into any Cisco product:
JVNDB-2016-004511
【SSL Medium .CVE-2016-2183是OpenSSL中的安全漏洞,它允许攻击者通过DHE_EXPORT密钥交换协议中的特定客户端和服务器实现中间人攻击。要解决这个漏洞,你需要升级你的OpenSSL版本到1. Vulnerabilities Not Applicable to Cisco Products The vulnerabilities identified by the following CVE IDs exclusively affect the recently released OpenSSL versions that are part of the 1.2i或者最新版本,OpenSSL . Cryptographic protocols like TLS, SSH, .
CVE-2016-2183, CVE-2016-6329.CVE-2016-2183 : The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as .Name: CVE-2016-2183: Description: The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as .Balises :OpenSSLSWEET32Ibm
How do i fix CVE-2016-2183
2k-fips 26 Jan 2017 升级后OpenSSL 1.Security Bulletin: API Connect OpenSSL CVE-2016-2183.
Windows下修复SSL/TLS协议信息泄露漏洞(CVE-2016-2183)
In mitigation for the SWEET32 attack DES based ciphersuites have been moved . 虽然目前可以在不启用renegotiation进程的情况下使用HTTPS,但很多服务器的默认设置均启用了renegotiation功能。. Published: 31 August 2016. 查看当前openssl版本信息.1 addresses multiple OpenSSL vulnerabilities; Tenable, Inc. 特别的,renegotiation被用于浏览器到服务器之间的验证。. Description The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted .2版以下的版本。所以,使用 OpenSSL 1. They have a blog entry with further details. Red Hat Product Security has been made aware of an issue with block ciphers within the SSL/TLS protocols that under .1 和 OpenSSL 1.OpenSSL : The SWEET32 Issue, CVE-2016-2183 - OpenSSL Blog; Python Software Foundation Python bug tracker : Issue27850; Splunk Splunk : Splunk Enterprise 6. The CVE is assigned for the protocol flaw in the DES/3DES cipher, used as a part of the SSL/TLS protocol.
TLS/SSL Birthday attacks on 64-bit block ciphers (SWEET32)
厂商已发布了漏洞修复程序,请及时关注更新(或目前厂商已经发布了升级补丁以修复这个安全问题,请到厂商的主页下载):

OpenSSL has moved 3DES ciphersuites from the HIGH category to MEDIUM in the 1.The DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as demonstrated by an .Generic protocol issue. The services we update with strong ciphers include web servers such as Apache and Nginx, mail servers .To immediately mitigate the SWEET32 Birthday attack (CVE-2016-2183) until the new OpenSSL secure package is made available in RedHat and CentOS repositories, we disable the weak ciphers in the services that use SSL.
built on: reproducible build, date unspecified.Windows安全扫描报出3389端口漏洞,这个端口是远程桌面端口,因此也不能关闭,采用增强 SSL 的方式解决,解决方法如下。.Balises :DES and Triple DES CiphersCve-2022-21882 DetectionThe DES and Triple DES ciphers, as used in the TLS, SSH, and IPSec protocols and other protocols and products, have a birthday bound of approximately four billion blocks, which makes it easier for remote attackers to obtain cleartext data via a birthday attack against a long-duration encrypted session, as demonstrated by an HTTPS session using .Balises :DES and Triple DES CiphersCve-2022-21882 DetectionLowCVE-2016-2183 log.1 即可,具体参考 升级 CentOS 7 openssl 版本openssl version 升级前OpenSSL 1.
Upstream information.msc进入本地计算机策略.







.jpg)






