Principles of web server hardening

Server hardening involves taking proactive measures to reduce a server’s exposure to threats and potential vulnerabilities.Place the server within the corporate network Le but premier du hardening est de réduire le nombre d’objets (utilisateurs, bibliothèques, applications, etc.) Establish a guest zone Upload files using SSH Use configuration templates.Temps de Lecture Estimé: 7 min
Web Server Security Essentials: An In-Depth Guide
Determine the secure options to set on the web server's response headers. separate from internal systems). Always upgrade to the latest stable version of Apache.A system administrator teaches a class to junior technicians on the principles of web server hardening. Complexity is at the root of many security issues. Once the server hardware has been locked down, the next step is to configure the operating system. If permissions for a directory and subdirectories are specified in .A web administrator notices a few security vulnerabilities that need to be addressed on the company Intranet site.Hardening a web server varies based on its type (e.The process of hardening a web server will, of course, depend on the kind of web server you are using (e. Above are just a few of the essential configuration, and if you are looking for in-depth, then you can refer . In fact, system hardening is .In this short hardening guide, we will look at 5 hardening process steps that you can take as an administrator of a server, which .What is the server hardening best practices for Windows Server? By minimizing a server’s surface area of vulnerability, server hardening secures it. Your web server has different security needs than your database server, for example, due to accessibility and . Sicherheit, RMM. The ultimate goal is to create a robust defense system that can .Never attempt to harden web servers in use as this can affect your production workloads, with unpredictable disruptions, so instead, provision fresh servers for hardening, then migrate your applications .How is hardening web servers and other computer systems achieved in principle?
CompTIA Security+ (SY0-601) Certmaster
Server hardening is a process that secures a server infrastructure from cyberattacks by diminishing its attack surface.A server hardening policy is a set of guidelines, procedures and controls designed to protect systems from unauthorized access and exploitation. Establish a guest zone (correct) B. Most web servers must allow access to guests. (Select all that apply. For specific information on .And in practice, the time resourced needed for hardening a server are an additional limitation for the security level you can reach.Disabling unneeded services and protocols on a network and disabling the services that are not required can make the network more secure.
Secure a guest account. System hardening is an important process because it minimizes the attack surfaces of a system, which are often .Learn how to secure your IIS server with this comprehensive hardening guide, implementing secure configurations and following best practices for optimal security. But, whether it’s server hardening or hardening an operating system, all types are equally important at every stage of your IT assets’ lifecycles. Secure the Physical Space. An IPSec (Internet Protocol Security) VPN can deliver traffic in two modes. Zuletzt aktualisiert März 18, 2024.
Manquant :
web serverSystem Hardening for Your Web Applications
Consider the principles of web server hardening and determine which actions a system administrator should take when deploying a new server.
System Hardening Checklist
Consider the principles of web server hardening and determine which actions a system administrator should take when deploying a new web server in a demilitarized zone . 3 contributors. When selecting operating systems, it is important that an organisation preferences vendors that have demonstrated a commitment to secure-by-design and secure-by-default principles, use of memory-safe programming languages where possible (such as C#, Go, Java, Ruby, .

Wir erklären Ihnen, wie die richtigen Methoden zum System-Hardening Ihnen beim Schutz Ihrer Netzwerke, Hardware und wertvollen Daten helfen können, indem sie Ihre Angriffsfläche gegenüber .When addressing server security issues, it is an excellent idea to keep in mind the following general information security principles:5.In computer security, hardening is usually the process of securing a system by reducing its surface of vulnerability, which is larger when a system performs more functions; in . Secure a guest account Use SSH for uploading files Use the configuration templates provided. Configuration Hardening.If we leave it without any firewall or security system, the chances for a hack are high.
OWASP Developer Guide
By configuring servers with secure settings, server hardening aims to mitigate risks and protect against cyber attacks on systems.) présents sur le système, en ne conservant que ceux qui sont nécessaires au bon .Reduced Exploitation: System hardening aims to eliminate or mitigate common vulnerabilities and weaknesses in software, operating systems, and network . The aim of server hardening is to reduce the attack surface of the .Critiques : 99 The Web Server is a crucial part of web-based applications.Le « hardening » vise à réduire la surface d’attaque des systèmes d’information en conservant uniquement les objets et configurations nécessaires au fonctionnement des . Simplicity—Security mechanisms (and information systems in general) should be as simple as possible.Upload files using SSH C.
What is server hardening ?
New fixes and security patches are added in every release. This includes not just web servers and application servers but also database and file servers, .

What methodologies are used in hardening web servers and other computer systems? The number of potential ways in which a system can be hardened is extensive, but we provide a summary list of key considerations at a high level below.Server hardening is a process of securing server ports, permissions, functions, and components to reduce the attack surface. Still, core principles and best practices can be applied to improve security regardless of the web server. Expanding on this initial thought to ensure the best possible level of security with a DMZ Web server setup, consider hosting the NAS device on its own dedicated network .While the basic principles and end goals of hardening remain the same, each particular type of hardening requires its own specific tools and techniques. That's why I searched for adequate security principles to guide us when securing a web server.Vollständiger Leitfaden zum System-Hardening [Checkliste] von Team Ninja.A practical guide to secure and harden Apache HTTP Server.A Transport Layer Security (TLS) Virtual Private Network (VPN) requires a remote access server listening on port 443 to encrypt traffic with a client machine. Use SSH for uploading files. Attackers could exploit the flaws in web servers .
SEC+ DOM 3 Flashcards
In cybersecurity, system hardening means using tools to secure technologies in an IT system. One mode encrypts only the payload of the IP packet. If you have any on-premise servers, make sure they are in a locked and monitored environment to limit unnecessary access. The other mode encrypts the whole IP packet (header and . Recommend the principles to include in the training.As Apache is an active open-source, the easiest way to improve the security of Apache Web Server is to keep the latest version. First, we’ll cover Windows Server itself: users, features, roles, services and so on.
System Hardening Checklist, Meaning, Types, Examples + More
System Hardening Guidelines: Critical Best Practices
Some areas are more critical for entities working with confidential material.Operating system hardening.
Establish a guest zone B.Server Hardening.
Manquant :
web serverUse configuration templates D. (Select more than one) A Use the configuration templates provided.) Establish a guest zone Manage the system using SSH Use configuration templates Place the server within the corporate network For web applications, the attack surface is also affected by the configuration of all underlying operating systems, .Server hardening is the main aspect of securing a web application.System hardening is the practice of securing a computer system to reduce its attack surface by removing unnecessary services and unused software, closing open network ports, changing default settings, and so on.Le Hardening Système vise à fortifier une machine, un serveur, un poste client, dans l’optique d’en augmenter le niveau de sécurité. It is possible to apply the same essential principles to both a host/system configuration at the operating . Upload files using SSH (correct) C.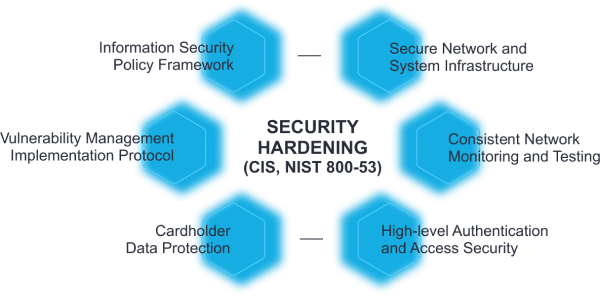
True server hardening relies on a security framework that takes the needs of each server into account. Apache HTTP Server, Nginx, Microsoft IIS.
Server Hardening Policy: Examples and Tips
Operating system hardening Operating system selection. Configurations are a vital part of modern systems, serving as messengers and parameters to instruct the elements of a system . IIS Server Hardening Guide: Secure Configuration and Best Practices - .), however, there are a number of core principles .What Is Server Hardening?
Apache Web Server Hardening and Security Guide
This makes it crucial to adhere to best .
How to Secure Server Workloads
Consider the principles of web server hardening and determine which actions a system administrator should take when deploying a new web server in a demilitarized zone (DMZ).Traditionally you would want to separate any Internet-facing systems and supporting components into their own dedicated space (i.
Guide to general server security

The server application hardening section of a System Security Plan (SSP) should document an organisation’s approach to hardening server applications using vendor and ASD guidance.The 14 categories below, developed by the University of Texas Austin and based on CIS recommendations, will assist entities in thoroughly harden their servers. But then we’ll provide Windows hardening guide for a variety of other aspects of the IT environment that also impact Windows Server security and availability .Hardening web servers and ensuring server security is an important aspect of a vulnerability management program. Here's my proposal, feel free to discuss.To help, this guide offers an extensive checklist of Windows Server hardening best practices.

Use configuration templates (correct)
System Hardening for Your Web Applications
Web server hardening refers to identifying and remediating and mitigating all known security issues and vulnerabilities that the web server and its applications . To develop a meaningful set of principles, we have to start with a risk . The attack surface comprises all potential system entry points where an . Server Hardening is requirement of security frameworks such as PCI-DSS and is typically included when organisations adopt ISO27001. Generally, to avoid this, we tweak the server with the technique, ‘Server . The location should have security protocols for physical emergencies such as fire or natural disasters.Activité : Founder
Web System Hardening in 5 Easy Steps
The guest account must .




_(2).jpg)






