Requesting authentication services
Authentications Certificate .
Department of State.The authentication fee is $8. You can submit a service request either online through the document authentication portal or by completing a service request form for mail-in or in-person submission.
Authentication services contact details
Now, the StoreFront's Logon Data Provider service contacts the Federated Authentication Service and asks to generate a certificate for the authenticated user.Authentication Certificate Requirements.
Authentification et autorisation
After you send your document.Afficher plus de résultats Before you start. Les identifiants de . Building a custom Express middleware for JWT validation.SAP SuccessFactors has been encouraging and working with our remaining customers who need to migrate to the SAP Cloud Identity Authentication services that offers advanced identity management features, multi factors, and risk-based authentication.Télécharger l’Assistant. Authentication systems . With Authentication as a Service, organizations can control access to their applications and servers from various devices and networks. Under Suites, go to LiveOps > Authentication > Identity Providers. We will process your request in 12 weeks with the date we receive it.
Authentication: Methods, Protocols, and Strategies

Definition and Methods
The feature is enabled through app configuration: Configuration >> General Settings >> Client certificate mode. Check if your document is eligible for authentication by Official Documents Services and proceed to submit authentication request online for eligible documents. You should only use this service if you know the officer has given us their most recent home address. Either way, I do not like this . Authenticate an official document for use outside the U.
Choose Your Best Authentication Solutions in Azure App Service
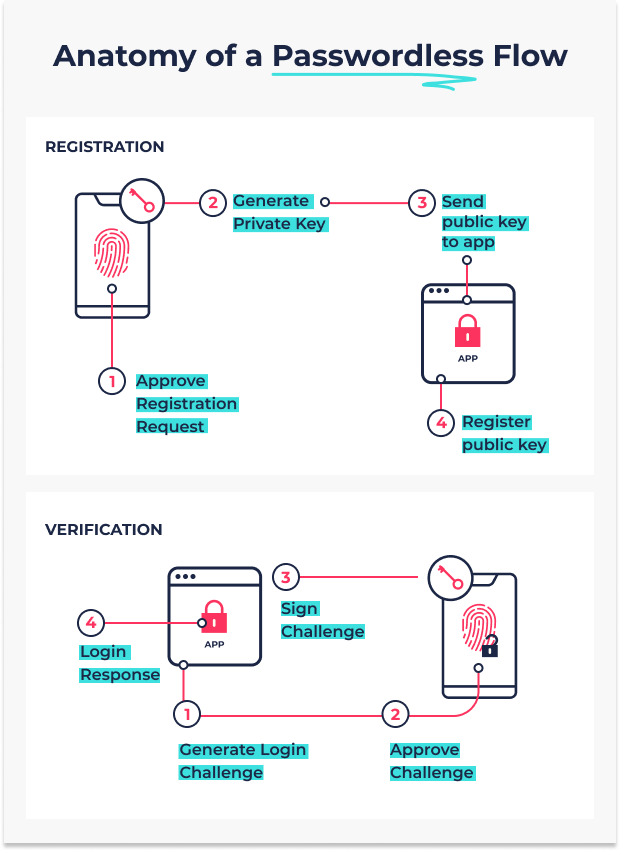
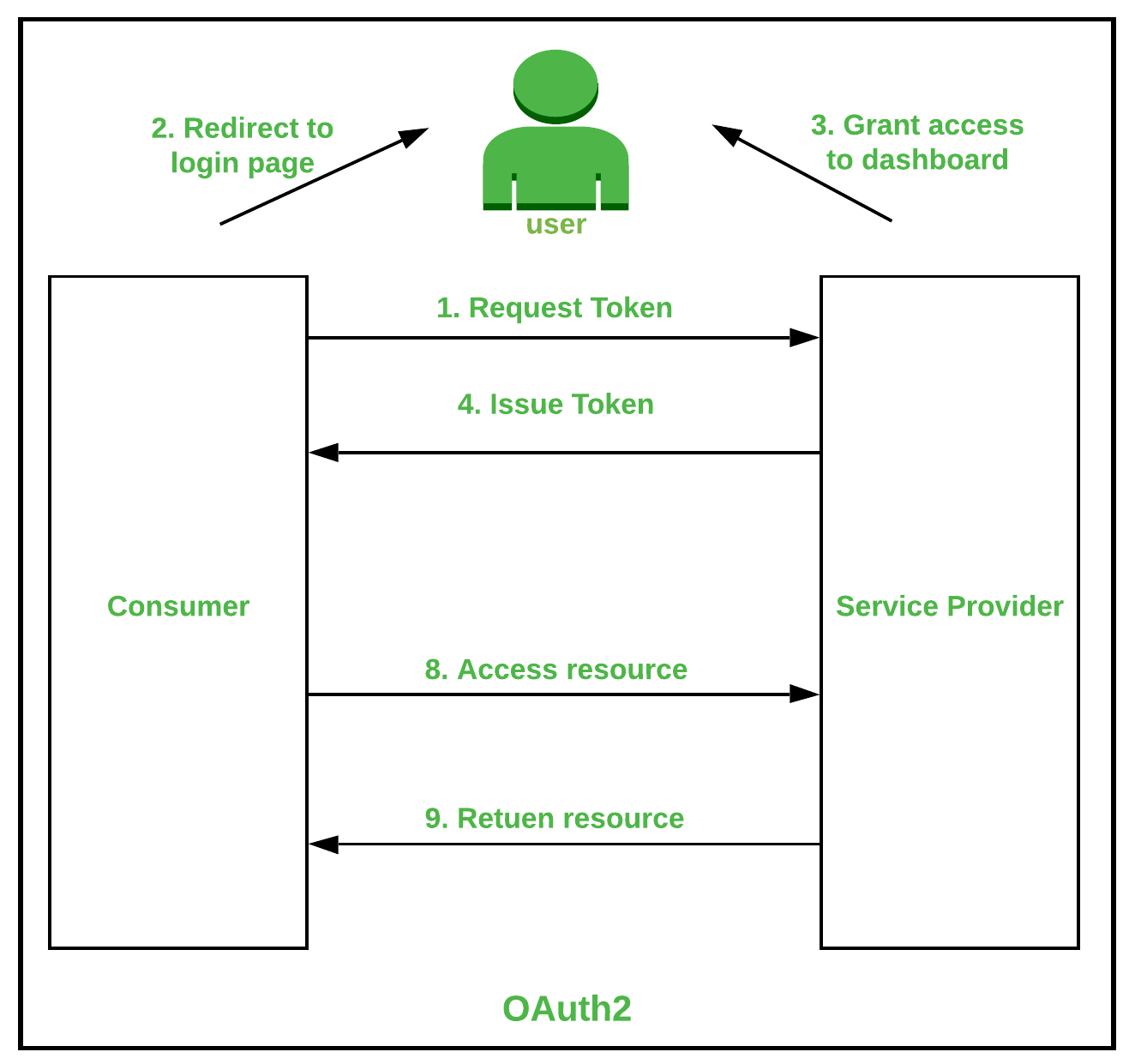
The authentication flow looks similar to the registration flow, the main differences being that authentication: Doesn't require user or relying party information; Creates an assertion using the previously-generated key pair for the service, rather than the authenticator's key pair.CAS, ou Central Authentication Service, est un protocole d’authentification unique (SSO) qui permet aux sites web d’authentifier les utilisateurs.IMPORTANT UPDATE: Walk-in apostille services have resumed at our New York City and Albany customer service locations. Mail Service The Authentication of documents takes approximately 5 business days to process from the time of receipt**. The FAS connects to the Active Directory to verify the user and their shadow accounts. Office Hours: 8:15 AM - 4:45 PM Walk-In Customer Hours: 9:00 AM - 1:00 PM, Monday-Friday, .Authentication for NAV Web Services with Windows User over HTTP Basic . To better understand what . The Apostille Convention took .If the country where you want to use your document is on the 1961 Hague Convention member list, you will need an apostille.Due to system changes, a CVV (a . Ensuite, sélectionnez Ajouter une méthode dans le volet Informations de sécurité. Before submitting your request, please follow steps 1, 2, 3 and 4. To verify that the switch can route packets, you must ping the server from the switch. Personal information will only be used for the purpose . ( 194) Authentication is the practice of verifying the identity of users or other entities as part of an access control system. AaaS providers offer . It is assumed that a cluster-independent service manages normal users in the following ways: an administrator distributing private keys a user store . If you submit the service request online, you will receive an email confirmation of submission with a service request number. Submit Document Authentication Request. Please also note that the Distribution Centre is unable to answer questions regarding our service or provide status updates. AaaS enables organizations to track . Department of State must be submitted with document. Contact Email: [email protected]. Apostilles and authentication certificates are both ways of certifying .Service Contact: Office of the Secretary, Office of Notary Commissions and Authentications.
Web Authentication API
Notarial and Authentication Services at U.Authentication in microservices can have three meanings: Authenticating end-users accessing the microservices application; Authenticating microservices . If you have received a document with an apostille from Ontario, verify the apostille here.Please note: If you drop off your request at our department’s Distribution Centre, it will be processed as per our current processing time. Authentication is provided by matching the sign-in credentials to a principal (an IAM user, federated user, IAM role, or application) trusted by the AWS account.0 protocol for authentication and authorization.1X authentication does not work unless the network access switch can route packets to the configured authentication RADIUS server.Authentication as a service is a cloud-based authentication solution that allows businesses to outsource their authentication needs. Verify an Apostille. The Authentication Services Section does not offer in-person service.What is an Authentication Server. Requesting Authentication Services. Best practices for REST API security: Authentication and authorization.To request authentications service, you must complete Form DS-4194.NET web service which is part of ASP .FiveM is a framework for multiplayer GTA V mods that lets you play on customized dedicated servers .Authentication is the process of determining if the person or entity accessing a computing system really is who they claim to be. Until a client is authenticated, only Extensible Authentication Protocol over LAN (EAPOL) traffic is Requirements for your document. Google supports common OAuth 2.October 6, 2021. Visa and Mastercard are accepted for Walk-in Service only. A typical authentication flow is as follows:
Reference Architecture: Federated Authentication Service
To set up the OIDC identity provider, follow these steps: Register and configure an application with the OIDC provider and find your Client ID and Issuer URL.Vue d’ensembleYou must request authentication services for mail. state will need an apostille from that state's secretary of state. Send your document.Please see ‘Walk-In Service’ section below for details.
![What's the Best Authentication Method? Analysis [2023]](https://www.iproov.com/wp-content/uploads/2021/09/best-authentication-methods-v3-ai-1.png)
User Service (RADIUS).
Apostille or Certificate of Authentication
An authentication server is used to verify credentials when a person or another server needs to prove who they are to an application.Authentication is the process that companies use to confirm that only the right people, services, and apps with the right permissions can get organizational resources.Taille du fichier : 105KB
Qu’est-ce que le protocole CAS (Central Authentication Service)
Step 4 - Storing and using the JWT on the client side. Users in Kubernetes All Kubernetes clusters have two categories of users: service accounts managed by Kubernetes, and normal users.API authentication is the process of verifying the identity of a user who is making an API request, and it is a crucial pillar of API security.First, a human user or an application uses their sign-in credentials to authenticate with AWS.Authentication services contact details Warning. Step 6 - Validating User Requests. Configure TLS mutual authentication for Azure App .From a design perspective, Authorization Services is based on a well-defined set of authorization patterns providing these capabilities: Policy Administration Point (PAP) . Then it speaks to Active Directory Certificate Services (AD CS) and submits a certificate . Our mailing address can be found in step 4. There are many types of API authentication, such as HTTP basic authentication, API key authentication, JWT, and OAuth, and each one has its own benefits, trade-offs, and ideal use cases.Visit the website of the US State Department and navigate to the section on Requesting Authentication Services. Department of .Authentication Services.Cookies vs Local Storage. To better understand what an authentication server is, let's look at what it does by taking a peek into what happens when an authentication request is made.
Request an authentication code to be sent to a home address
Azure App Service offre des capacités intégrées d’authentification et d’autorisation (parfois appelées « Authentification simple »), ce qui vous permet de .This form is used by individuals, institutions, and government agencies to request authentication and/or apostille certificates under the seal of the U. How to build an Authentication HTTP Interceptor.Authentication as a Service (AaaS) provides authentication services like multi-factor authentication, single sign-on, and password management in the cloud.
Client authentication
Google APIs use the OAuth 2.
We are asking our customers to plan, test, and make the move to IAS/IPS prior to the impact changes .Si vous êtes déjà inscrit, vous êtes invité à effectuer la vérification à deux facteurs. What to include when you order authentications by mail: Complete Form DS . A microservices application has multiple, independent services, each performing a specific predefined function.
Authenticate Your Document
Mailing address. Due to the impact of coronavirus (COVID-19), it may take longer than usual for post to be delivered. In this article, we’ll discuss the primary challenges of authentication in a microservices . Pour résoudre ce problème, utilisez PowerShell pour réinstaller les packages du plug-in WAM de Microsoft Entra (pour les comptes .00 per document.With this id and key, I can either authenticate each request, or create an authentication token to authenticate further requests.Step 5: Submit your service request. Checking User Expiration. Contact Phone: (202) 727-3117.
What is an Authentication Server
0 scenarios such as those for web .
Authentication-as-a-Service: What Is It and Why You Need It
Its designers aimed it primarily at a client–server model, and it provides mutual authentication—both the user and the server verify each . The app code is responsible for validating the client certificate. The Department collects this information under the authority of the Department of Foreign Affairs, Trade and Development Act, section 10(2)(a).It takes around 5 working days for an officer to receive an authentication code at their home address.
Requesting Authentication Services
A personal/company check or money order made payable to the U. Office of Authentications: Information about our office. ASAs offer their UIDAI-compliant network connectivity as a service to requesting entities (such as AUAs/KUAs) and transmit their authentication requests to CIDR. Documents such as vital records issued by a U. When a user generates an API key, let them give that key a label or name for their own records.Connector type Supported connectors; Built-in - Azure API Management - Azure App Services - Azure Functions - HTTP - HTTP + Webhook .Have your users provide their API keys as a header, like curl -H Authorization: apikey MY_APP_API_KEY https://myapp.
Angular Authentication With JWT: The Complete Guide
Note: HTTP operations can authenticate connections to Azure Storage accounts behind Azure firewalls with the system-assigned identity.When working, studying, or travelling abroad, end destination recipients may ask for certificates of authentication or apostilles to ensure that public documents (e. ASAs are agencies that have established secured leased line connectivity with the CIDR compliant with UIDAI’s standards and specifications. Our office may refuse to provide service to anyone showing behaviour deemed disrespectful, violent or abusive. Federal documents will need an apostille from the U. Enclose the certified copy of the birth certificate with the raised or sealed stamp of the court or .Kerberos (/ ˈ k ɜːr b ər ɒ s /) is a computer-network authentication protocol that works on the basis of tickets to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Go to the Unity Dashboard and select the project you want to authenticate.However, they don't support the user-assigned managed . Reminders: Verification if an authentication certificate or an apostille is needed.A completed Request for Authentication Service form is required by the Department for the purpose of responding to a request for authentication.











