Security log management and logging

AWS offers managed services, such as Amazon GuardDuty for threat detection and Amazon Detective for .
A09:2021
CIS Controls v8 and Resources. There are three types of the logs available at the Azure platform: Azure resource log: Logging of operations that are performed within an Azure resource (the data plane). Logging and Monitoring. Security Analytics and Logging can be expanded at the user’s discretion, allowing for longer retention and analysis, and even alerts on potential .
With Loggly, you don’t have to configure multiple tools for log managemen t and security log analysis. Collect, alert, review, and retain audit logs of events that could help detect, understand, or recover from an attack.This book teaches IT professionals how to analyze, manage, and automate their security log files to generate useful, repeatable information that can be use to make their .
Log Management Software for Linux and Windows
It involves defining the depth and scope of the SOC’s visibility.
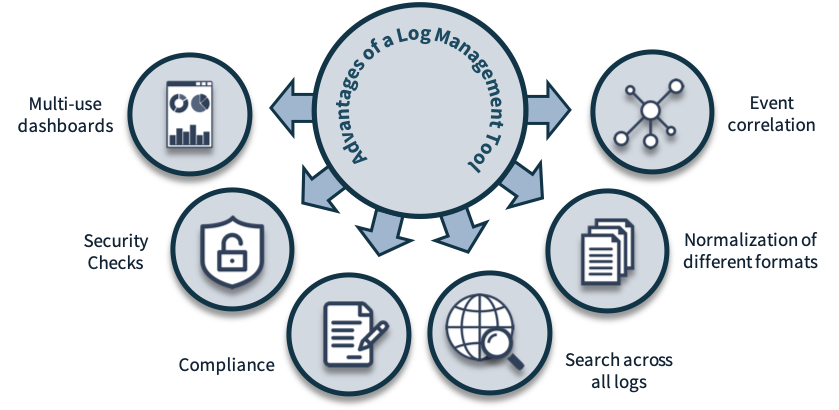
syslog-ng Premium Edition. February 4, 2023. Formulate a Strategy and Establish Policies. A sound strategy and clear policies are foundational to every organization’s security logging best practices. Enterprise class log management software.Security log management and logging best practices.Home CIS Critical Security Controls CIS Critical Security Control 8: Audit Log Management.In this article, we will spotlight 11 log management best practices you should know to build efficient logging and monitoring programs. Effective logging helps developers to optimize application performance, quickly diagnose and troubleshoot issues, and enhance a system’s overall security. Why EventLog Analyzer: Your Best Bet. But in these sources, there's plenty of irrelevant and relevant data.A log is a record of events that occur within an organization’s computing assets, including physical and virtual platforms, networks, services, and cloud . View all 18 CIS Controls Learn . From the exhaustive . Hacking into the billions of user accounts online is a lucrative enterprise for criminals. Learn how to conduct security log management that provides visibility into IT . Instrument and collect. It provides practical, real-world guidance on . Log management covers all the aspects and policies necessary for logs to satisfy the business goals they support.Log management is the process for generating, transmitting, storing, accessing, and disposing of log data.SIEM and log management have the following key differences: SIEM combines event logs with contextual information about users, assets, threats, and vulnerabilities and can help .
Security Log Management: Challenges and Best Practices
A Complete Logging Guide.
Cisco Security Analytics and Logging
Log management is a core function of a security operations center (SOC).
Log management: the key to reliable and secure applications
Organizations use syslog-ng to reliably and securely collect, process and normalize log messages from across their IT environments, and forward . Many organizations use conventional tools like rsync or cron to collect log data, but these tools don’t support real .

Login security ensures that only genuine, authorized users can access online accounts, keeping bad actors out. Exabeam Security Log Management represents the Exabeam entry point to ingest, parse, store, and search security data in . Complete this procedure using a log collector tool. Log management tools improve security, help troubleshoot issues, and .With security log management you can continuously collect, examine, and visualize data and information related to security events (security logs), like intrusions or suspicious activity on networked systems and infrastructure. Loki is a log management system that is produced by the made by the Grafana team under the open source AGPLv3 license.Security log board and logging best practices. Loggly also allows you to create customized dashboards using different types of charts.Ingest logs via Azure Monitor to aggregate security data generated by endpoint devices, network resources, and other security systems. Collect log data.Log management is the practice of continuously gathering, storing, processing, synthesizing and analyzing data from disparate programs and applications in order to optimize system performance, .Secure log company consisting the generation, transmission, data, analysis and disposal from security log data, ensuring its confidentiality, integrity furthermore available. This book was written for anyone interested in learning more about logging and log management.Security Log Management with Exabeam.Discover the world’s leading AI-native platform for next-gen SIEM and log management.In addition, the book addresses logging for programmers; logging and compliance with regulations and policies; planning for log analysis system deployment; cloud logging; and the future of log standards, logging, and log analysis.Security logs track application and network activity. A security log offers a chronological record that collects and holds information related to security events . You’ll learn how to establish policies and take a proactive approach to collecting, analyzing, and storing business-critical log data. These aspects include log generation, collection, storage, archiving, data transfer, analysis, search, retention, .The Graylog blog. Learn how to conduct security log management that provides clarity into THIS infrastructure activities both . This includes enabling detection, investigation, and remediation processes with controls to generate high quality alerts with native . Logging refers to the tasks of generating, collecting, and storing logs.64 the cost-effective security and privacy of other than national security-related information in 65 federal information systems.Log management refers to the processes and tools involved in the collection, storage, and management of log data—often from disparate sources into a single system.Generally, there are five basic steps in the log management process. Security log data is used to detect security events, assess threats, and understand what has happened. You can sync all the charts in a dashboard in a single click.Arfan Sharif - April 12, 2023.Taille du fichier : 1MB
The Ultimate Guide
Ensure log data is encoded correctly to prevent injections or attacks on the logging or monitoring systems.
Cybersecurity Log Management Planning Guide
For the first step in the log management process, collect from separate locations throughout your tech stack to support log aggregation in step two.
What Is Login Security?
Logging and Threat Detection covers controls for detecting threats on cloud, and enabling, collecting, and storing audit logs for cloud services, including enabling . Cyber threat intelligence gathers data from all clients on a platform and provides immunization from a new threat . SolarWinds offers IT management software and monitoring tools such as their Log & Event manager.
7 Critical Log Management Best Practices
Log Managment and Security
The Special Publication 800-series reports on ITL’s research, 66 guidelines, and outreach efforts in information system security, and its collaborative activities 67 . Ensure that logs are generated in a format that log management solutions can easily consume.Azure provides a wide array of configurable security auditing and logging options to help you identify gaps in your security policies and mechanisms.
Guide to Cybersecurity Logging and Monitoring
Here are some security logging best practices you should follow to help protect your network from unauthorized . However, logging generates a . Another critical component of log management is log analytics. This guide provides a clear path forward, breaking down the key .
Guide to Computer Security Log Management
With an escalating landscape of cyber threats, understanding how to log and monitor your cybersecurity measures effectively is crucial. This publication provides . NIST has released Draft Special Publication (SP) 800-92 Revision 1, Cybersecurity Log Management Planning Guide for public comment through .This publication seeks to assist organizations in understanding the need for sound computer security log management. Log management and log analysis methods are covered in detail, including approaches to creating useful logs on systems and .An audit log is a document that records the activities within an application, system, or network.Auteur : Michael Cobb
4 Best Practices & More
Elevate your cybersecurity with the CrowdStrike Falcon ® platform, the premier AI-native platform for SIEM and log management.
What Is Log Management?
SolarWinds Log & Event Manager.Best Practices for Security Log Management.

Logging and Threat Detection covers controls for detecting threats on Azure and enabling, collecting, and storing audit logs for Azure services. Security logging and monitoring are critical security controls, but they can be effective only if you follow these six security logging best practices. Implement Structured Logging.
Top 46 Log Management Tools for Monitoring, Analytics and more
Log management
Whether it's user activity, performance metrics, Windows events logs, network traffic or any other log .Centralized logging goes with CLM: Centralized log management is done in a 3-step process.
Log Management
Alternatively, you may enable and on-board . This term refers to the analysis of log data to extract insights and generate information, with the end goal of . At one time, the only way to protect sensitive personal, financial, and business information in online accounts was a .We’ll cover some of the most important best practices that can help you make the best use of logs to manage performance, security, and compliance.
11 Efficient Log Management Best Practices to Know in 2024
This log management tool handles security, compliance, and troubleshooting by normalizing your log data to quickly spot security incidents and make troubleshooting a breeze.
CIS Critical Security Control 8: Audit Log Management
This process is so key is the Core for Internet Security lists log management as one of its critical security controls. Here's how: Step 1.See NIST SP 800-92 Guide to Computer Security Log Management for more guidance.
Security log management and logging best practices
Monitoring of events¶ The logged event data needs to be available to review and there are processes in place for appropriate monitoring, alerting, and reporting: Incorporate the application logging into any existing log management systems/infrastructure e.Login security defined.
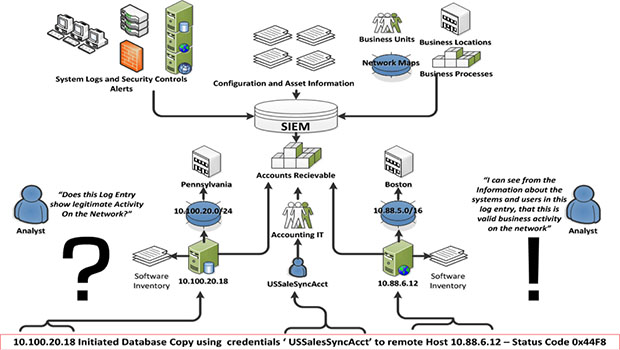
We will share logging options across the typical cloud application stack, log analysis options, and sample queries. Structured logging is a best practice in log management because it makes log data more consistent, structured, and easy to analyze. As we’ve discussed, logs come from a number of different systems and applications, such as operating systems, software applications, cloud infrastructure, network devices and more. Jeff Darrington. Effective log management is essential to enable fast detection and response and ensure compliance with regulatory requirements. Security Audit Logging Policy.The most up-to-date Azure Security Benchmark is available here.Be mindful about different types of logs for security, audit, and other operational logs at the management/control plane and data plane tiers. With a view to include security log management in your organization, your audit plan should have a requirement of an event log management tool with business intelligence imbibed, to analyze security event logs. It's critical due .