Seedlab dns rebinding attack
DNS Rebinding
2019-01-23 14:27:24.
How to simulate an IoT device with web service?2.
SeedLab9: DNS Rebinding Attack Lab
Reduce Firefox’s DNS caching time.这个实验的目标是使用DNS重绑定攻击来绕过沙箱保护,这样攻击者的javascript代码就可以成功地从设备获得必要的信息,并使用这些信息来获得温度测量的一个非常高的值。.Regarder la vidéo48:351.This lab uses the SEED Internet Emulator as the basis to show show students how the DNS Infrastructure works. It includes the necessary components to rebind the IP address of the attack server DNS name to the target machine's IP address and to serve attack payloads to exploit vulnerable software on the target machine. Writing a simple packet-filter firewall; playing with Linux's built . 上面一种方法只写入了一个域名的缓存,我们想要对一个域进行攻击. 下面是Kaminsky DNS Attack的步骤:.
Dns rebinding
The objective of this lab is for students to gain the first-hand .
【Seed Lab】DNS Rebinding Attack Lab
我们的攻击目标是防火墙后面的一个物联网设备。我们不能从外部直接访问这个物联网设备。我们的目标是让内部用户运行我们的JavaScript代码,这样我们就可以使用DNS重新绑定攻击与物联网设备交互。 许多物联网设备都有一个 . By default, the cache’s expiration time is 60 seconds. We did not encounter any trouble porting this lab. Just need to modify the filed of www in the attacker nameserver will work.04/Networking/DNS_Rebinding/ 在这个实验中模拟 . The first breaking change window begins 2024-04-22 09:00UTC and ends .This lab focuses on seveal DNS Pharming attack techniques. Task1: Configure the User VM. Also, modify the TTL field would make it work faster.dnsCacheExpiration的值更改为10,重启浏览器使之生效。 Step 3 配置本地DNS服务器 实验环境下载: https://seedsecuritylabs. Students will first set up and configure a DNS server, and then they will try various DNS Pharming attacks on the target that is also within the lab environment. firebox浏览器默认缓存DNS查询结果60s,这意味着DNS rebinding attack至少需要等待60s。 浏览器地址栏中键入 ,进 . 这意味着我们的DNS重新绑定攻击需要等待至少60秒。.5 中通过 nslookup 命令发送DNS request包,比如 nslookup www. DNS Rebinding 域名重新绑定攻击技术.
SeedLab DNS Rebind Attack
Kaminsky DNS Attack是一种针对DNS的攻击方式,攻击者利用DNS服务器的缺陷,通过伪造DNS响应包来实现对域名解析的欺骗。. 08-10 3840 本实验中模拟的物联网设备是一个恒温器,用于控制室内温度。客户端需要能够与服务器交互,以此设置温度。物联网设备在防火墙后面,外部设备不能与之交互,因此不能控制恒温器。为了击败防火墙保护,攻击代码必须首先进入内部网络 .Updated lab Feb 2020 为了减少DNS服务器的负载并加快响应时间,Firefox浏览器缓存DNS结果。.DNS工作原理如下:当用户在浏览器中输入一个域名时,操作系统会向本地DNS解析器发送一个DNS查询请求。 本地DNS解析器首先查询自己的缓存,如果找到了 . 本实验涵盖以下主题: • DNS server setup. 这里要用scapy了(Guideline里有模版照着写. Our system provides scalable .
Manquant :
How to setup local DNS server, Kaminsky attacker machine and malicious DNS server?2.Auteur : 潜龙勿用DNS Rebinding Attack Lab
firebox浏览器默认缓存DNS查询结果60s,这意味着DNS rebinding attack至少需要等待60s。浏览器地址栏中键入 ,进入设置,搜索dnsCache,将network.task 5:配置本地DNS服务器.com域的DNS服务器. Firewall Exploration Lab.
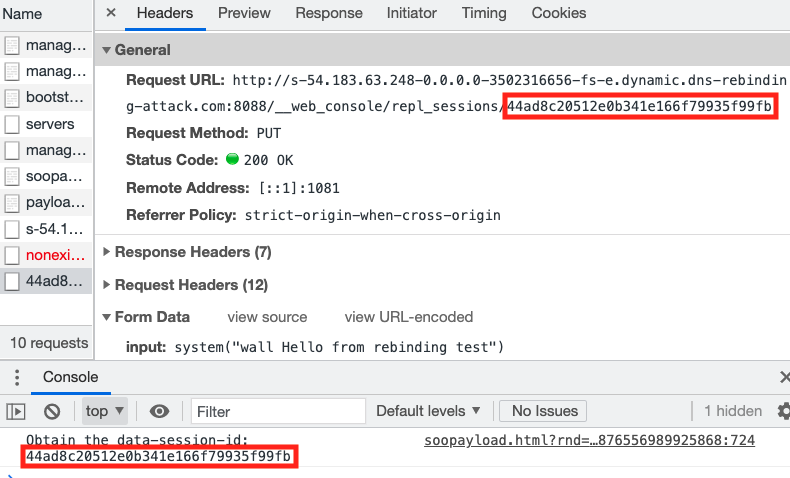
• DNS rebinding attack. Using the DNS rebinding technique to launch attacks on IoT devices behind the firewall. 它充当了互联网上的电话簿,将人类可读的域名(例如example.The objective of this lab is to use the DNS rebinding attack to circumvent the sandbox protection, so the JavaScript code from the attacker can successfully get the essential .Step 2: Conduct the DNS rebinding.com nameserver, so an NS record is added to its database.
Manquant :
seedlabDNS Rebinding Attack Lab
We are introducing three breaking change windows during which we expect breaking changes to be deployed to GitLab. DNS Infrastructure Lab. Task 3: Spoofing NS Records. In order for others to find this nameserver, we need to register our nameserver with the .关于DNS-rebinding的总结 一般来说浏览器通过向DNS服务器发送请求将用户输入的域名转换为ip地址,然后向对应的IP地址请求资源,最后回显给用户。 这是一 .【Seed Lab】DNS Rebinding Attack Lab.04/Networking/DNS/DNS_Rebindingالفيرشول مشين https . Zait told The Daily Swig: “The IP Address will be automatically . Contribute to seed-labs/seed-labs development by creating an account on GitHub.A successful DNS rebinding attack usually exploits a series of vulnerabilities: Cross-Site Scripting—XSS, Default or Misconfigured DNS settings, Poorly implemented Same-Origin Policy (SOP) that allows scripts from different origins to interact with restricted resources, Absence of hostname validation.DNS Rebinding Attack Lab. Skip to content. SEED Lab: A Hands-on Lab for Security Education. 包里写入的就是 . 让其他的DNS服务器可以看到刚刚配置的attacker32.This version brings many exciting improvements to GitLab, but also removes some deprecated features.com)映射到计算机可理解的IP地址(例如192. You can read more about it on our blogpost.
DNS (Domain Name System) is the . SEED Labs developed in the last 20 years.
The objective of this lab is for students to gain the first-hand experience on the remote DNS cache poisoning attack, also called the Kaminsky DNS attack. Writing a simple packet-filter firewall; playing with Linux's built-in firewall software and web-proxy firewall; experimenting with ways to evade firewalls. Le but d'une attaque de rebinding DNS est de tromper le navigateur Web d'une victime en lui faisant faire des requêtes .Une attaque de rebinding DNS est un type d'attaque qui exploite le protocole DNS (Domain Name System) pour contourner les contrôles de sécurité et obtenir un accès non autorisé au réseau ou aux données d'une victime.
dns rebinding attack lab
Our goal is to get an inside user to run our JavaScript code, so we can use the DNS rebinding attack to interact with the IoT device. DNS (Domain Name System)是一个用于将域名转换为与之关联的IP地址的分布式命名系统。. 近期斗哥在学习有关于浏览器同源策略方面的知识点,发现了一个有趣的绕过浏览器同源策略 .
DNS Labs
Firewall Evasion Lab .• DNS server setup • DNS rebinding attack • Attacks on IoT devices • Same Origin Policy. 首先在 user-10. Task 2: DNS Cache Poisoning Attack – Spoofing Answers. DNS Pharming attacks manipulate this resolution process in various ways, with an intent to . To reduce load on DNS servers and to speed up response time, Firefox browser caches DNS results. 很简单,就在权威字段里写入一个域对应的权威服务器,在附加字段写入它的IP,这样缓存的时候就会有一个域的记录. How to Spoof DN.Singularity of Origin is a tool to perform DNS rebinding attacks. Containers have significantly reduced the complexity of the lab . How to trigger the Same-Ori.SEED Labs – DNS Rebinding Attack Lab 4 Step 1.
DNS Rebinding 域名重新绑定攻击技术
This lab is not related to security, but it is the basis for the other DNS labs. 在互联网上,每个设备都有一个唯一的IP地址,用于在 .
DNS Rebinding Attack Lab
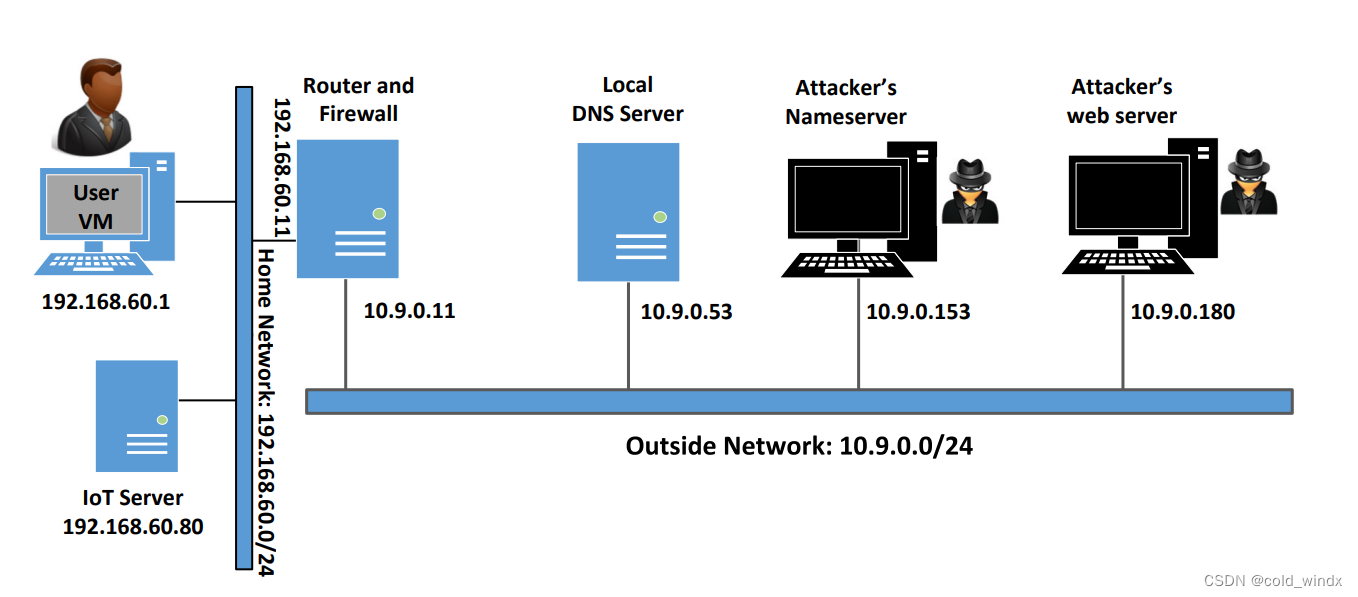
SEED Labs – DNS Rebinding Attack Lab 2 2 Background: IoT Our attack target is an IoT device behind the firewall.com),此时DNS服务器会向其权威服务器请求,此时攻击者发送大量伪造的DNS回应,并猜测transaction ID,在权威服务器回应之前到达,且某一个猜对了transaction ID的话,就能成功写入缓存了. Navigation Menu Toggle navigation. Without this step, DNS requests from others will not be able to reach our . Implement a small DNS infrastructure for a mini Internet created using .
Manquant :
Many IoT devices have a simple .الملفات موجودة في الرابط أدناه https://seedsecuritylabs. In the setup, we have a simulated IoT device, which can be controlled through a web interface (this is typical for many IoT devices).Palo Alto Networks has launched a detector to capture DNS rebinding attacks from our DNS Security and passive DNS data.

SEED Labs network security lab - Local DNS Attacks - Alina-sul/seedlabs-local-dns-attacks. 攻击者向目标DNS服务器发送一条DNS解析请求,请求解析一个不存在的域名,比如 www. 默认情况下,缓存的过期时间为60秒。. nslookup与dig两个工具功能类似,都可以查询指定域名所对应的ip地址,但不同的是 dig . It includes the necessary components to rebind the IP address of the attack server DNS name to .
Task 2: Construct DNS request.The DNS rebinding attack technique normally requires detailed knowledge of a target network, but a new tool by security researchers Tomer Zait and Nimrod Levy – dubbed ReDTunnel – means a hacker would need “zero knowledge about the target” in order to run an attack. And we could also flush the local dns server to make it takes effect faster. It also ships with sample payloads to exploit several vulnerable .This translation is through DNS resolution, which happens behind the scene. 该漏洞允许程序突破进程内、进程间的隔离,如此,恶意程序就能从它不能访问的区域读取数据. That means that our DNS rebinding attack needs to wait for at least 60 seconds. How to Construct DNS request with Python and Scapy?3. The attacks conducted in this lab assume that the attacker is on the same local network, and can thus sniff the DNS packets.我们的目标是让内部用户运行我们的JavaScript代码, 这样我们就可以使用DNS重新绑定攻击与物联网设备交互。 许多物联网设备都有一个简单的内置web服务器, 这样用户可以 . DNS服务器在本地 .












