Splunk latest event

The simplest way to create a new event type is through Splunk Web. For example, the following is the Simple XML for the dashboard panel above. Example 3: Partition different searches to different indexes; in this example, you're searching three different indexes: main, _internal, and mail. How to write Splunk query to get first and last request time for each sources along with each source . I have my query ready which essentially extracts some fields and displays in a table. The aggregation is added to every event, even events that were not used to generate the aggregation.The problem is that 1/2 of the hosts are performing a vast majority of the cumulative task (millions) while other host can go days without performing even one task (hence no log event). An event is a set of values associated with a timestamp.When Splunk software indexes events, it does the following tasks: Task.March 18, 2024. Join us at an event near you to gain new skills, expand your network and connect with the .What your query is doing is for a particular sessionid getting the first and last time of the event and as the output naming the fields Earliest and Latest respectively.conf23 and we’re bringing . It is a single entry of data and can have one or multiple lines. Navigate to Settings > Event types. index=idx_noluck_prod source=*nifi-app.name: Name of the first, or only field, that displays the marker.The eventstats command is similar to the stats command. We make organizations more resilient. Log events are sent to your Splunk deployment for indexing.SAN FRANCISCO – June 07, 2022 – Splunk Inc. An event can be a
2022 Splunk Product Review
You can also run this search with type=hosts and type=sources.Event data can be assigned to the event key within the JSON object in the HTTP request, or it can be raw text. You can use both commands to generate aggregations like average, sum, and maximum. I'm just using the _time field to sort the date.
How to get the latest timestamp by host?
The results are: serviceName. I want to show range of the data searched for in a saved search/report. Upcoming Events. Cost: In-Person $425 / Free Virtual.
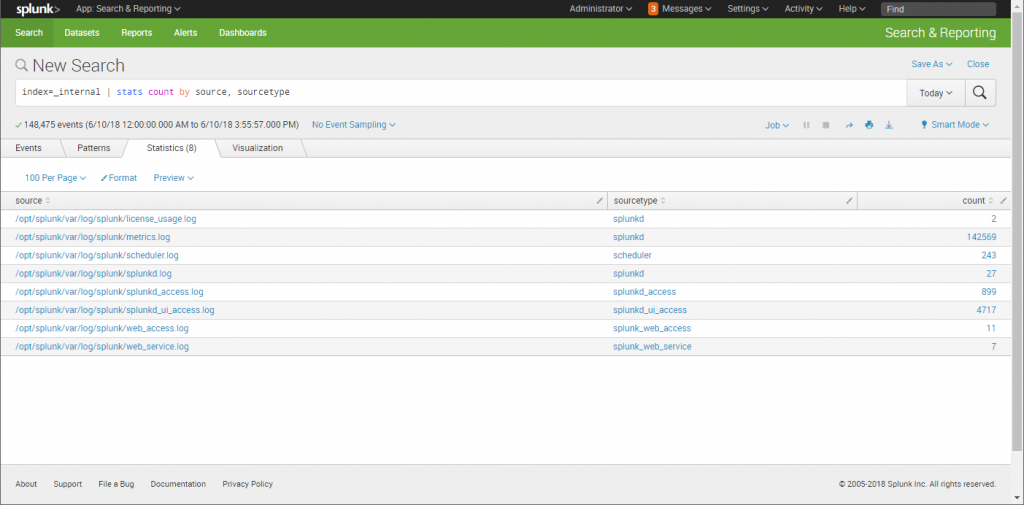
Example 1: Search across all public indexes. If the stats command is used without a BY clause, only one row is returned, which is the aggregation over the entire incoming result set. Below seems to be suffice , however I am unable to change the date & time format for required results : tstats latest(_time) where index=abc by host.
Log events
I need to list all the hosts with their latest Splunk event timestamps in YYYY-MMM-DD HH24:MI:SS format .Chronological and Timestamp Order Distinction
Time functions

Diminish downtime.This Splunk Quick Reference Guide describes key concepts and features, as well as commonly used commands and functions for Splunk Cloud and Splunk Enterprise.Generate an events list. - Splunk Community.These files are monitored by Splunk UF and forwarded to two heavy forwarders to be saved on the indexer. This is similar to SQL aggregation. There are no additional data format requirements.Wednesday, November 15, 2023 | 12:30–15:00 GMT.
Solved: How to pull latest event
Select the Add chart button ( ) in the editing toolbar and browse through the available charts.

This Splunk search utilizes the tstats command to show the last time that an event was indexed for each index, host and sourcetype. Use the events viewer visualization to capture logs and look at raw data for visibility into the specific attributes of each event.Calculates aggregate statistics, such as average, count, and sum, over the results set.07-26-2011 03:44 PM.Splunk Employee. Search Analysis.
Find earliest and latest event per day for a time range
News, Press Releases, Videos, Blogs, Events
Join us and be Ready for Anything! July saw our largest event of the year, . Review Configuration . Cisco Completes Acquisition of Splunk. Construct custom log events to index and search metadata. This opens the Save as Event Type dialog, where you can provide the event type name and optionally apply tags to it. When you're starting a hunt, it's important to have a clear objective in .So, you're looking for outcome events by user, so your by clause of your stats should reflect that. Id prefer it if it stopped searching against a host's log once the most recent event has been discovered. 06-06-2018 05:52 AM. to determine how long it took to index x data. We have now noticed that the number of events . How to get latest values for each group with an Elasticsearch query? 0. In this example, host is a default field, while eventtype and user are additional fields that .To add an event annotation to a chart, use the command search type= annotation followed by the query that searches the data for the events to annotate, and the time frame for the query. Simplest and most efficient is simply this: Run over all time and it will search till it finds the most recent event with the text statuskey, return that one event, and stop.If you have metrics data, you can use the latest_time funciton in conjunction with earliest, latest, and earliest_time functions to calculate the rate of increase for a counter. Set up a new data source by selecting + Create search and adding a search to the SPL query window. The results of the bucket _time span does not guarantee that data occurs.Solved: I simply looking for the fist event in an index and the last. The event key is at the same level within the JSON event packet as the metadata keys. Identify relationships based on the time proximity or geographic location of the events.
Splunk
index=server EventCode=5829.
How can I get the latest event by a specific field?
You can of course just limit the fields: You might do slightly better with: depending on your data and field extractions. February 27, 2024.We run a query that produces a count of each event type, but we also want to know when was the last time the event ran. I think you are looking for: The time the search was executed will be in the info_search_time field. They also have role-based permissions that can prevent you from seeing and/or . zacksoft. 2022 felt like it went by in a flash. any suggestions? i couldn't The command creates a new field in every event and places the aggregation in that field.It then reports the 20 most recent events.
Time since last event by index, host and sourcetype
Announces Fiscal Fourth Quarter and Full Year 2024 Financial Results. Here are the definitions of these settings. How to find the latest event (message) with a given key (field)? asingla. The Splunk platform indexes events, which are records of activity that reside in machine data.conf : time_field = . Using the log event alert action requires the edit_log_alert_event capability.
Splunk to Announce Fiscal 2023 Third Quarter Results on November 30, 2022.This function is used to retrieve the first seen value of a specified field. Technical Update Event. If a BY clause is used, one row is returned for each distinct value specified in the .How eventstats generates aggregations.
Use fields to retrieve events
Any help or insights is appreciated.
eventstats command usage
Splunk Web enables you to view and edit lists of event types. View Conference Catalog.Generate an events viewer. Location: Washington DC + Virtual. Configures line breaking for multi-line events. You could create a dashboard with 3 panels and have one search in each panel. Select the chart on your dashboard to highlight it with the blue editing outline. (NASDAQ: SPLK), the data platform leader for security and observability, today announced it will host its 13th annual user .

Tags:
Using dedup to keep the oldest events
Configure event line breaking. Identifies event timestamps and applies timestamps to events if they don't exist. This would get you the latest result: Configure character set encoding.How to find the latest event (message) with a give. serviceTimeStamp.I want to include the earliest and latest datetime criteria in the results. Concepts Events. Data Property Description click. You want to see events that match error in all three indexes . Events provide information about the systems that . The content in an events list depends on the search that you run. Configures character set encoding.Dates: January 29 - February 5, 2024. Splunk query: retrieve top 5 previous _raw events for each matching search event. After you run a search that would make a good event type, click Save As and select Event Type. Use this correlation in any security or operations investigation, where you might need to see all or any subset of events .You can use the cURL web data transfer application to manage tokens, events, and services for HTTP Event Collector (HEC) on your Splunk Enterprise instance using the Representational State Transfer (REST) API. Here is the query: index=lisa_vse| top limit=100 serviceName | fields serviceName count serviceTimeStamp. Events are transformed into a table of aggregated search results.
Format events for HTTP Event Collector
02-07-2013 03:02 PM. Using the REST API lets you seamlessly manage HEC objects without having to use Splunk Web or the CLI.

Hi all, I know that the dedup command returns the most recent values in time. Note: Keep in mind that event types are often associated with specific Splunk apps.
December 22, 2022.Rejoignez un évènement Splunk près de chez vous pour acquérir de nouvelles compétences, élargir votre réseau et vous connecter à la communauté.02-07-2013 03:23 PM.
Splunk Cheat Sheet: Query, SPL, RegEx, & Commands
Choose the events viewer chart.Splunk software supports event correlations using time and geographic location, transactions, sub-searches, field lookups, and joins.Temps de Lecture Estimé: 2 min
Event order functions
index=* OR index=_*.earliest/latest : Time range of the clicked event, which is: earliest: _time latest: (_time + 1 second) map (event tokens) The field for the tag in dynamic drilldown always corresponds to click.log* APILifeCycleEventLogger Event Durations (ms) API=/v*/payments/ach/*. How get max count of request in time in splunk. 11-11-2020 11:32 AM. In View mode, you can select an . trn_RiskReportsService. eventstats command. (no need for by _time as well). So far I have figured out how to find just the first and last event for a given time range but if the time range is 5 days I'll get the earliest event for the first day and the last event on the last day. index=info |table _time,_raw | stats first(_raw) Explanation: We have used “| . 2022 Splunk Product Review. Starting the hunt process.splunk latest event for each host.Las Vegas, June 11-14.I would like to find the first and last event per day over a given time range.To create a simple time-based lookup, add the following lines to your lookup stanza in transforms. Identifies the field in the lookup table that represents the timestamp. The recentTime in the result is the latest time that Splunk indexed data from that sourcetype (or host or source). You can also get the most recent value of a particular field using the first function in stats: 02-07-2013 02:43 PM. For anyone in cyber threat intelligence (CTI), from newbies to . Fix issues faster. | stats count, latest(_time) .value: Value of the first, or only field, that displays the . Within the event key-value curly brackets, the data can be in whatever format you want: a string, a number, another JSON object, and so on.







