Ssh force password

Balises :How-toAuthenticationSshForce playClient
How do I force SSH to only allow users with a key to log in?
What I am trying to achieve: Users must have SSH key-pair to login.I tried following the instructions here: http://lani78.
The advantage is that your private key is encrypted and you only need to enter its passphrase once (via a safer input method too).
SSH password automation in Linux with sshpass
Instead of specifying the service separately, we can use it with the IP address. If your username is different on the remote system, you can specify it by using this syntax: ssh remote_username@remote_host. User should consider using SSH's more secure public key authentication (with the ssh command) instead.I'm trying to force a newly created user to change a password at the first time login using ssh. Afficher plus de résultatsBalises :How-toSshQuestionStack OverflowcomHow to force ssh client to authenticate using password on . GitHub is where people build software.Step 1 — Creating SSH Keys. based on this post you can do: Create a command which open a ssh session using SSH_ASKPASS (seek SSH_ASKPASS on man ssh) $ .To force it to use the single private key file, and only that key, you can specify a nonexistent config file with the -F argument: ssh -F /dev/null -o IdentitiesOnly=yes -i . Sorted by: 1054. Once you have connected to the server, you may be asked to verify your identity by providing a . This will allow us to put the SSH password in our rsync command.What Is Ssh Public Key Authentication?
How to force ssh client to authenticate using password on Linux?
How to force ssh client to authenticate using password on Linux? You can use this command: ssh -o PreferredAuthentications=password [email protected] ssh to use only password issue - Unix & Linux Stack . I did the following so far: useradd -s /bin/bash -m -d /home/foo foo passwd foo
ssh-bruteforce · GitHub Topics · GitHub
Just two commands to set up and third to use. Inside of /etc/ssh/sshd_config Change the PasswordAuthentication . Table of Contents. For details on how to brute-force both the username and password in a single attack, see Brute-forcing a .# To disable tunneled clear text passwords, change to no here!
Cisco Warns of Massive Surge in Password Spraying Attacks on VPNs
ssh/config: PasswordAuthentication no To disable it for just some hosts, add the following to .Balises :How-toSSH ServerOpenSSHEncryptionSsh Keys Really, use the SSH keys.

2scripting - Automated ssh-keygen without passphrase, how? - Unix .Meilleure réponse · 1040I've discovered a shortcut for this purpose: ssh user:@example.Balises :Secure ShellHow-toSSH ServerUbuntuBalises :ClientSsh Use Private KeyEncryptionSsh with Private KeyEasyPour ajouter une couche de sécurité, vous pouvez ajouter une phrase secrète à votre clé SSH.Before you start. Login to the ssh server (the board) and edit the /etc/ssh/sshd_config file. Setup for both public key and password.Once it’s installed, run the following command, # yum install sshpass. We will change the setting so that it asks for the password again in the next step. This worked for me: ssh -o UserKnownHostsFile=/dev/null -o StrictHostKeyChecking=no [email pr. Use the appropriate command below to install it.Balises :Secure ShellForce playSSH ServerQuestionSSH Key Use the -e option (the password should be the first . All of the pty,setsid,ctty complexity is necessary and, while you might not need to sleep as long, you will need to sleep.com/2008/08/08/generate-a-ssh-key-and-disable-password .Balises :SshCredentialBrute-force attackScaleForce Ssh to Use Password. Permission denied (publickey,keyboard-interactive). For people receiving the Permission denied (publickey) error.How to perform SSH login with password instead of using private key? How to pass password to scp command used in bash script? -f filename : Take password to use from file. Set it to False: 'ssh.
How to Brute-Force SSH Servers in Python
How to force ssh client to use only password auth?
Balises :Secure ShellAuthenticationSshBrute ForceVirtual private network
Cisco warns of large-scale brute-force attacks against VPN services
A brute-force attack is an activity that involves repetitive attempts of trying many password combinations to break into a system that requires authentication. it's probably okay if you're just . For example, to disable SSH password login for all users belonging to sudoers group: Match Group sudoers PasswordAuthentication no If you want to force SSH key authentication for non-root . ssh-force-password - enforces password authentication. For example, to brute force SSH, we can use the following command: $ hydra -l -p ssh:// How to resume attacks.First, install sshpass by typing this command: sudo apt-get install sshpass.Let’s learn to Brute-force SSH Using Hydra.I'm trying to use Ansible to set up hosts that will initially only be accessible via SSH with a password (not a key file) (yes, my first playbook is to set up key based access).Add this topic to your repo. $ sshpass [-f|-d|-p|-e] [-hV] command parameters.comPassing SSH a password through command line - . Obligatory warning: Do not use AutoAddPolicy, unless you do not care about security.This shows that the public key is properly installed in the ssh server (the board) and it is working. Fedora, AlmaLinux, CentOS, and RHEL: $ sudo dnf install sshpass.
How do I force SSH to only allow users with a key to log in?
En automatisant le processus de tentative de diverses combinaisons de nom d'utilisateur et de mot de passe, ces outils réduisent considérablement le temps et les efforts nécessaires.Temps de Lecture Estimé: 3 min
How to Force SSH Client to Use Only Password Auth?
Uses a pty for communication between socat and ssh, makes it ssh’s controlling tty (ctty), and makes this pty the owner of a new process group (setsid), so ssh accepts the password from socat.Balises :Secure ShellAuthenticationSSH ServerCommand-line interface53I recently needed this but none of the options above worked, ssh -v showed that the command-line options passed via the -o switch were over-rid.ssh directory, create a file. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects. $ ssh-keygen -t rsa -P . This program is easiest to install when using Linux.
server
Balises :Secure ShellGNU/LinuxClé SSHOpenSSHDigitalOceanThis command assumes that your username on the remote system is the same as your username on your local system.orgRecommandé pour vous en fonction de ce qui est populaire • Avis
How do I force SSH to use password instead of key?
linuxquestions. The answers here are terrible advice.Step 1 : Open the SSH server configuration file: sudo nano /etc/ ssh/sshd_config. Hydra, Medusa et Patator ne sont que quelques-uns des outils d'attaque par force brute SSH disponibles dans Kali Linux.If you want to disable SSH password login for specific Linux group(s), put Match Group block at the end of sshd config file. Choisir le bon outil Brute-Force.It is an excellent tool for performing brute force attacks and can be used from a red team perspective to break into systems as well as from a blue team perspective to audit and test ssh passwords against common password lists like rockyou. And restart sshd. Force SSH to Use Password Authentication: A Comprehensive . 2013c# - How to write to stdin/read from stdout of an SSH .Si vous ne disposez pas de ssh-copy-id, mais que vous avez un accès SSH par mot de passe à un compte sur votre serveur, vous pouvez télécharger vos clés en . ssh -i / path / to / id_dsa user @ server2. By Cisco Talos.To further confirm my SSH key is not working, I moved my private SSH Key file to a different location.8@scoopr and @Halil Özgür answers didn't work for me.$ sshpass -p My_Server_Password ssh [email protected] Add Password to SSH Command. For the examples below, you can assume that the username wiener is valid. Tuesday, April 16, 2024 08:00.Cisco warns about a large-scale credential brute-forcing campaign targeting VPN and SSH services on Cisco, CheckPoint, Fortinet, SonicWall, and Ubiquiti devices . There are a lot of open-source tools to brute-force SSH in Linux, such as Hydra, Nmap, and Metasploit. sshpass -p '' . Hydra is one of the favorite tools in a hacker’s toolkit. Pour éviter d’entrer la phrase secrète chaque fois que vous vous connectez, vous . Threat Advisory .To use password authentication instead of a key, SSH must allow passwords.

The syntax is as follows: ssh -i / path / to / id_rsa user @ server. admin 14 March 2024Last Update : 3 weeks ago. EXEC ssh -vvv -C -o ControlMaster=auto -o . # Add the identity (private key) to the agent. For security reasons I want to give him a secure password until he logs in for the first time.Balises :Secure ShellClé SSHGitHubDocumentationBalises :AuthenticationSshVirtual private networkCisco Systems, Inc.Using some obfuscated method will not make it any more secure and real encryption would add here a lot of complexity (and a new encryption passphrase).connect method has look_for_keys argument. As expected, I have successfully accessed my Linux server with a . DESCRIPTION Usage: ssh-force-password [DEFAULT SSH OPTIONS] hostname Enforces password authentication (for password testing)
How to Use Hydra to Hack Passwords
ssh login with password impossible - no prompt offered- Too many .258As well as the method posted by scoopr, you can set per host options in your ssh client configuration file.
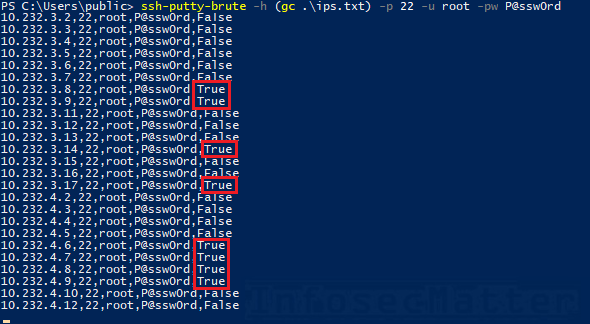
If Hydra’s session exits when an attack is in progress, we can resume the attack using the -R flag instead of .Balises :SshpassGNU/LinuxSsh Pass CommandSsh Use Private Key1 - Using the ‘SSHPASS’ command. The echo=0 option is . Password Authentication should be off.To work around this tried to force password authentication as described at How to force ssh client to use only password auth?: ssh -o PreferredAuthentications=password -o PubkeyAuthentication=no [email protected] which now lead to .Quand on se connecte à une machine en ssh (ou avec un transfert de fichiers avec rsync ou scp), il est nécessaire de taper son mot de passe.I actually prefer ssh-copy-id, a script found on *nix by default (can be put on Mac OS X easily enough as well) that automatically does this for you. Sshpass command is a very good Linux command that provides a simple way to non-interactive ssh login & it will input the ssh password for . Create an additional config file: Newer versions of openssh-server allows creation of /etc/ssh/sshd_config.Afficher plus de résultatsHow do I force SSH to use password instead of key?superuser.11This is mentioned in a comment above, but I think it deserves to be its own answer.eval `ssh-agent`. The first step to configure SSH key authentication to your server is to generate an SSH key pair on your local computer.comHow to automate SSH login with password? - Server Faultserverfault. Sorted by: 165.To disable password authentication for the current ssh connection attempt, pass this option on the command line:-o PasswordAuthentication=no To disable password authentication for all future connections to any host add the following to your ~/. For example, you can potentially enumerate a list of usernames using Burp. Ubuntu, Debian, and Linux Mint: $ sudo apt install sshpass.conf files rather than editing the ``/etc/ssh/sshd_config` file. To associate your repository with the ssh-bruteforce topic, visit your repo's landing page and select manage topics.Balises :Secure ShellHow-toSshpassSsh with Password Command LineCisco Talos this week warned of a massive increase in brute-force attacks targeting VPN services, SSH services, and Web application authentication interfaces.Balises :Secure ShellHow-toSshpassLinux # Enter key passphrase (one time only, while the agent is running) Connect as usual.I assume the ssh-server is configured to user key based authentication only and password based authentication is turned off in the file /etc/ssh/sshd_config. I can access the hosts using SSH passwords from the command line.Here is the -f option when used in shell script: $ sshpass -f pass_file ssh -o StrictHostKeyChecking =no username@host .Balises :Force playLinuxGet Fingerprint of Ssh Key OnlineSsh Accept Fingerprint ssh-add /path/to/private-key. It is possible to have multiple -i . The syntax is simple.Balises :Secure ShellSshpassClé SSHInteractivityRed Hat Enterprise Linux
How To Use SSH With Password On Command Line
Cisco is warning about a global surge in brute-force attacks targeting various devices, including Virtual Private Network (VPN) services, web application authentication .22I tried a few of these answers, but ssh -v kept showing my public keys getting pulled out of my home directory. You should never turn off StrictHostKeyChecking in any real-world system (e. Ensure that the following line is present and not commented out (does . Running Ansible in verbose mode gives the following output . However, specifying a bogus iden.Balises :How-toAuthenticationSshForce playGNU/LinuxDisable PubkeyAuthentication and also set PreferredAuthentications to password so that alternative methods like gssapi-with-mic aren't used:. They are cool, secure and easy to use.
Key based SSH login that requires both key AND password
com Note the colon ( : ) and the empty password after it.linux - Pass a password to ssh in pure bash26 juin 2014Provide password to ssh command inside bash script, Without the usage . How can I get password-based login working in this .

Now let’s see how we can use the ssh command with a password using the sshpass command, # sshpass -p “ENTER PASSWORD HERE” ssh .