Use openssl to verify certificate
To verify a certificate, you need the chain, going back to a Root Certificate Authority, of the certificate authorities .Verify a Private Key Matches a Certificate and CSR.comRecommandé pour vous en fonction de ce qui est populaire • Avis
Verify a certificate chain using openssl verify
How to Check Certificate with OpenSSL
openssl-dhparam (1ssl) - DH parameter manipulation and generation.openssl verify -untrusted intermediate-ca-chain.
Configure Third Party Certificate for UCS Central
Temps de Lecture Estimé: 11 min
openssl verify
comHow to view certificate chain using openssl - Server Faultserverfault.crt -text -noout.pem | diff -q fullchain. In these examples the private key is referred to as privkey. $ openssl s_client -connect :. If no certificates are given, this command will attempt to read a single certificate from standard input. COMMAND OPTIONS.By default OpenSSL is configured to use various certificate authorities your system trusts and stored in /usr/lib/ssl/ directory.
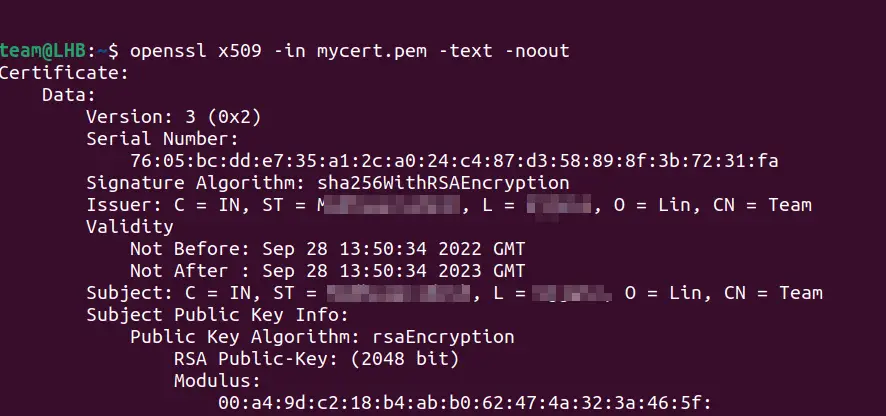
Verify Certificate Chain with openssl. openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:4096 -keyout private. crl contains serial numbers of certificates that are revoked.
openssl-verify: Utility to verify certificates
For verifying a crt type certificate and to get the details about . In this article we’ll go through a few different use cases of s_client.key) matches a certificate ( domain.You can remedy the situation by telling OpenSSL what to trust. The response looks like this:
Setup & verify mutual TLS authentication (MTLS) with openssl
I'm trying to run an openssl command to narrow down what the SSL issue might be when trying to send an outbound message from our system. And I provided the same CAfile to both . The output of this results in. However, my requirements are: Verify that the incoming certificate is valid with a trusted . Creating such a file is easy (just appending it) edited Jun .
How to Check Certificate, CSR, and Private Key with OpenSSL?
To verify the certificate of a website, you can use the following openssl s_client command: $ openssl s_client -connect :443. download the crl from these urls. CONNECTED(00000003) depth=3 C = US, O = Equifax, OU = Equifax Secure Certificate Authority.eu} Your domain will get updated in the . 2013ssl - How to verify DER certificate with openssl? ssl - openssl s_client -cert: Proving a client certificate was sent to . Infrastructure.crt Type Certificate. openssl rsa -in privateKey.Use the openssl verify function to verify a certificate chain.A PEM-encoded file can show up in many file formats, such as .If you need to check using a specific SSL version (perhaps to verify if that method is available) you can do that as well. rsautl -encrypt (also -verify) accepts a privatekey file as input -- or a publickey file or a certificate file -- but .key in my sample), run this: openssl rsa -noout -modulus -in my. If you have a revoked certificate, you can also test it the same way as stated above. I found this command in another topic: Using openssl to get the certificate from a server.Calculate the modulus for your private key. You can replicate what they do with a three step process: (cat cert.To ensure openssl s_client (or openssl s_server) uses your root, use the following options: -CAfile option to specify the root. -cert option for the certificate to use. Today we’ll be focusing on the s_client tool, which can be used to connect, check and list SSL/TLS .key -out certificate. If you want to know when a website's public certificate expires, you can use openssl commands as shown below: $ echo | openssl s_client -connect cisco. Now, for your private key file (my.OpenSSL can be used to verify if a port is listening, accepting connections, and if an SSL certificate is present. Something like: openssl verify -CAfile C:\ca-cert. notBefore=Jan 28 00:00:00 2016 GMT. then you can use an above command which will give you certificate details. openssl-dsaparam (1ssl) - DSA parameter manipulation and generation. Compare modulus to check compatibility. If the modulus output you get from the 2 commands matches, the private key and your certificate are a pair. Check a Certificate Signing Request (CSR) openssl req -text -noout -verify -in CSR.One or more target certificates to verify, one per file. openssl verify -CAFile root. Check a private key.Check whether an SSL Certificate or a CSR match a Private Key using the OpenSSL utility from the Linux command line.1k myself, it shouldn't be using any distro-specific config. You can also check CSRs and check certificates using our online tools. This is as simple as providing the file name to the following command (in our case the file is request. -CAfile file A file of trusted certificates.openssl verify doesn't handle certificate chains the way SSL clients do. openssl s_client -connect ip:port -prexit.comRecommandé pour vous en fonction de ce qui est populaire • AvisI have used the cipher and run the following OpenSSL trace: .crt) and CSR ( . openssl verify -CAfile ca-bundle. When we open s_server as follows, the client is able to connect to my server: openssl s_server -accept 12345 -cert our-cert. 209 Converting pfx to pem using openssl.If you need to check the information within a Certificate, CSR or Private Key, use these commands. I want now to try to establish a connection between openssl s_server and openssl s_client and verify that they get both authenticated mutually, but I cannot wrap my mind with the documentation on how to do it.
Useful openssl commands to view certificate content
The file should contain one.How can retrieve chain of certificates via opensslstackoverflow.With OpenSSL, you can also check what does your CSR contains.openssl verify -untrusted /dev/null; cat; } < combined. Compare the 2 values. Also, if there is an intermediate certificate, then it needs to be added to mycert. To end any command and return to the terminal, press Ctrl+D – also known as EOF or “End of File”, . You need to add the CA's root certificate with -CAfile; and not your end entity certificate.
Checking a website's security certificate with OpenSSL
To make sure that you have installed the SSL certificate correctly, we have have compiled a cheatsheet with OpenSSL commands to verify that multiple protocols use the correct certificate. The command will show you the information about the certificate, including its detail like OU and CN.Akamai SureServer CA G14-SHA2 reference. The verify command verifies certificate chains.pem: OK Above shows a good certificate status.How can I verify the file? Note I compiled OpenSSL 1.We are wanting to use two way certificate authentication using open ssl.In this tutorial I will share openssl commands to view the content of different types of certificates such as.Therefore the first step, once having decided on the algorithm, is to generate the private key.The openssl command can also be used to verify a Certificate and CSR(Certificate Signing Request).pem is our certificate.comOpenSSL command cheatsheet - FreeCodecampfreecodecamp. if the peer certificate serial number is there in the crl list, then it is .
How to verify SSL certificates with OpenSSL on Command Line
Run the following command in our command prompt window where server.

Temps de Lecture Estimé: 5 min
Verify: SSL Certificate Under OpenSSL
If OpenSSL is installed, run the command openssl pkcs7 -print_certs -in . But it turns out that OpenSSL is using certs from its trusted store (see How to verify a signature of one . Certificate issuer authority signs every . A simple way to check if a certificate is PEM-encoded is to use OpenSSL: openssl x509 -noout -in input_file.Using OpenSSL to check and verify secure connections.To check the contents of an SSL certificate in CRT or PEM format, use the following OpenSSL command: openssl x509 -in certificate.crt certificate. OpenSSL can be used for validation in the event .) This works fine. To achieve this I will copy the client certificates on to the client node under a new directory /root/certs.crt ) combined.Renew SSL/TLS certificate OpenSSL [Step-by-Step] 8. You can also present a client certificate if you are attempting to debug issues with a connection that .Verify open ports using OpenSSL: OpenSSL can be used to verify if a port is listening, accepting connections, and if an SSL certificate is present.pem ClientCert. Verify the Certificate Signer Authority openssl x509 -in certfile.You're not actually encrypting with the pivate key. Here is the most basic syntax.
Test an SSL Connection Using OpenSSL s
So we use openssl ca instead of openssl x509 to avoid the deleting of the SAN field. $ openssl verify -crl_check -CAfile crl_chain.The command below generates a private key and certificate. To verify a certificate chain you must first get the certificate chain to .In this tutorial, you'll learn how to use the openssl command to check various kinds of certificates on Linux systems.Check SSL Certificate Subject name with OpenSSL. Revoked certificate.
certificates
Verifying the certificate chain with OpenSSL
321 Converting PKCS#12 certificate into PEM using OpenSSL. Since as you said, everything after the first cert is discarded, and openssl verify can take a PEM file on the command line, you don't need to use file-like input redirection, just pass the filename.From looking online I was able to find the following command: openssl verify -CAfile root-ca. Below, I use -CAfile option with Google Internet Authority G2: $ openssl s_client -connect google.CVE-2023-0466 David Benjamin discovered that the implementation of the X509_VERIFY_PARAM_add0_policy() function does not enable the check which allows . Running this command returns: ClientCert.
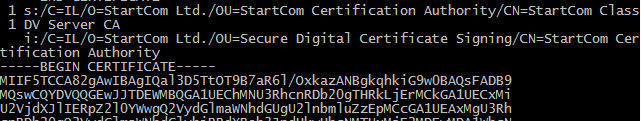
OpenSSL can be used for validation in the event plugin 51192 ' SSL Certificate cannot be trusted ' unexpectedly finds unknown certificates on a port: # openssl s_client -connect With OpenSSL library, how do I check if the peer certificate is revoked or not. For example, to create an RSA private key using default parameters, issue the following command: ~]$ openssl genpkey -algorithm RSA -out privkey. Use these commands to verify if a private key ( domain.crt -untrusted intermediate-ca-chain.comopenssl verify – Verify a certificate and certificate chainmisterpki.With OpenSSL you have two (out of the box) options: Use OpenSSL's own cert store (it is a hierarchy of directories created by perl script provided with OpenSSL) Use only a certificate chain file created by you (it is a text file with all PEM-encoded certificates in a chain of trust).Verify Certificate File openssl x509 -in certfile.The intuitive try is this: $ openssl verify -CAfile g1 g0. com5 ways to check SSL Certificate - howtouselinuxhowtouselinux. Today we’ll be focusing on the s_client tool, which can be used to connect, check and list SSL/TLS related information.com6 OpenSSL command options that every sysadmin . Which will retrieve the website's . -CApath directory. To verify a certificate and its chain for a given website, run the following command: openssl verify -CAfile chain.pem -) && \ openssl verify chain.4 Ways to Check SSL certificate – sslhow.com:443 2>/dev/null | openssl x509 -noout -dates. The certificates should have names . If the certificate is the site certificate, we will see the domain of our site in the output.Programmatically verify certificate chain using OpenSSL API29 avr. I also have installed the client certificate + root certificate on the client, and the server certificate + root certificate on the server. We now have all the data we need can validate the certificate. You can verify this using the following .pem is the file name of a certificate we are testing: openssl x509 -noout -subject -in server. From what I googled: x509 cerfiticate contains set of crl distribution points, ie set of urls.Verify a certificate chain using openssl verify. From reading the docs about the verify command, it says: If a certificate is found which is its own issuer it is assumed to be the root CA.comRecommandé pour vous en fonction de ce qui est populaire • AvisOpenSSL: Check If Private Key Matches SSL Certificate & CSR
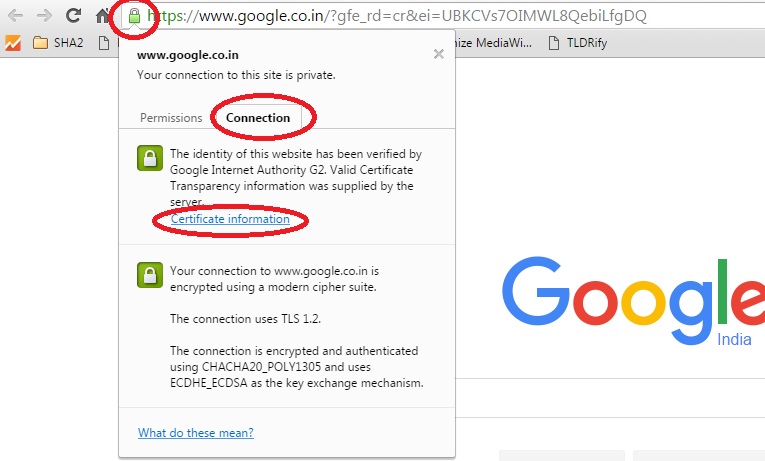
How to verify certificate chain with openssl
How to generate a self-signed SSL certificate using OpenSSL?
How To Verify A Certificate With OpenSSL
Check SSL Certificate Chain with OpenSSL Examples











