Web application security policy

Web application security is the practice of defending websites, web applications, and web services against malicious cyber-attacks such as SQL injection, cross-site scripting, or other forms of potential threats .
Generic Web Application Security policy templates
Join the Web Application Security Working .Les recommandations de ce guide concernent la sécurité des contenus présentés par un navigateur web aux utilisateurs.
As the newly appointed Director of Projects, .
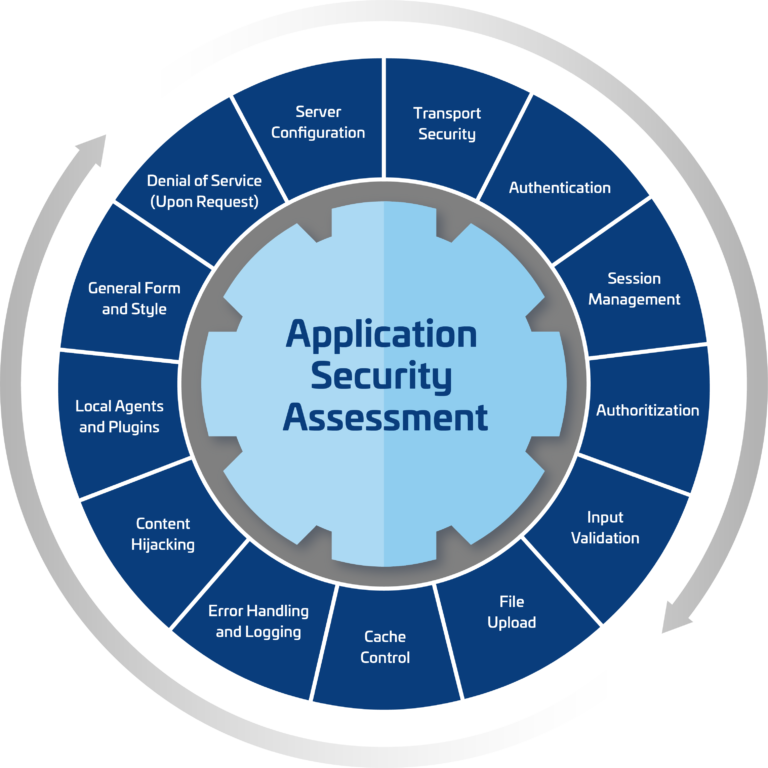
What is application security
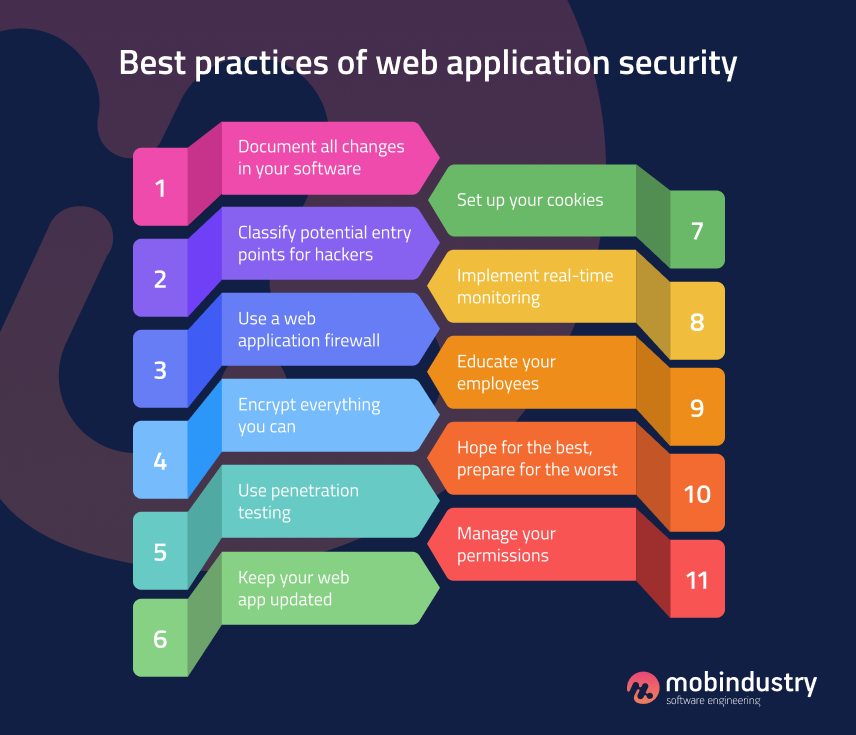
Security Checklist for Web Application
We cover the best-practice processes and key aspects of securing web-application-related configuration, from infrastructure to cloud environments and web-server-level .15 Application Security Best Practices Checklist. Web Application Security Explained: Risks & Nine Best Practices 5 application security assessment steps Asset-first application . It is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection . Historically, discussion of CSP has taken place at public-web-security and cross-posting is encouraged.Topic The BIG-IP ASM system includes generic security policy templates that provide different security levels and use different levels of operational resources. Effective website security requires design effort across the whole of the website: in your web application, the configuration of the web server, your policies for creating and .The more formal definition of website security is the act/practice of protecting websites from unauthorized access, use, modification, destruction, or disruption.How to Secure Web Applications from Vulnerabilities: 16 Web App Security Best Practices.Our current application does now have a Content Security Policy in place, and we demonstrated how attacks can exploit this. For Students, Faculty, Staff, Guests. Since 2017, there has been an increase in HTTP daily responses that include the Content Security Policy header or HTML meta tag.
OWASP Top Ten
Many industries are governed by strict data protection laws and standards, such as the General Data Protection Regulation or the Health Insurance Portability and Accountability Act (). If we aggregate this data by month, we see that almost 5 million web applications use .A well-crafted security policy .Security policies are, in effect, a strategy to protect web applications and ensure availability at all times. Dans cet article.Web Application Security imports BIG-IP Application Security Manager ™ (ASM) application security policies from discovered BIG-IP devices, and lists them on the Web Application Security policy editor Policies screen. Risks of Poor Web Application Security. Engage stakeholders: Foster communication with IT professionals, developers, and business leaders to gather insights.Taille du fichier : 204KB
Content Security Policy (CSP)
Establishing Application Security Policies
These generally include steps to identify responsibilities, .
How to Set Up a Content Security Policy (CSP)
Web application security refers to the strategies and practices dedicated to protecting web applications from potential threats that can compromise their security. Microsoft 365 . The following defines . The WSTG is a comprehensive guide to testing the security of web applications and web services. The CSP header has a built-in directive that helps in understanding how your web application makes use . The purpose of this policy is to enforce that web applications maintain the . D’innombrables menaces de sécurité affectent les applications logicielles. Toutefois, la liste des dix principales menaces d’application du projet Open Web Application Security Project (OWASP, projet de sécurité ouvert d’application web) compile les menaces pesant sur les applications qui .This Web Application Security Standards and Practices document establishes a baseline of security related requirements for all Columbia University-supported web services and . It represents a broad consensus about the most critical security .

It is a branch of information security that particularly deals with the security aspects of websites, web applications, mobile applications, and web services.Content-Security-Policy (CSP)¶ Content Security Policy (CSP) is a security feature that is used to specify the origin of content that is allowed to be loaded on a website or in a web applications.Web Application Security Policy.
Web Application Security: Risks, Tools & 9 Best Practices
Ces attaques peuvent être utilisées dans divers buts, comme le vol de .
Cloud Native Application Protection Platform (CNAPP)
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and . This commitment should be backed up by senior management and should be communicated to all employees. Manage Containers Properly. In the Policy for Web Application dialog, select the check box next to the user or group that you want to delete, click Delete Selected Users, and then click OK. Même de simple bugs dans votre code peuvent impliquer la fuite d'informations privées et des personnes .Open Web Application Security Project (OWASP) has a couple of Content-Security-Policy examples and some useful links on their Content Security Policy Cheat Sheet under Preventing Clickjacking: To prevent all framing of your content use: Content-Security-Policy: frame-ancestors 'none' To allow for your site only, use:Web application security is the practice of protecting websites, applications, and APIs from attacks. The Web Security Academy is a free online training center for web application security.Cet article d'introduction ne fera pas de vous un gourou de la sécurité des sites web, mais il vous aidera à comprendre d'où viennent les menaces et ce que vous pouvez faire pour .Various folks are experimenting with these directives. You must consider it at every step in the . If you're experimenting with a directive, please feel .
Overview of BIG-IP ASM security policy templates
You can seek external assurance of your attack surface by contracting pen .The OWASP Top 10 is a standard awareness document for developers and web application security. S’applique à: Windows 11, Windows 10.
Each security policy is assigned a unique identifier that it carries across the enterprise.Sécurité des applications Windows.To help you create an effective application security policy, we've outlined five key elements that must be included: There should be a clear and concise statement of the organization's commitment to security.Applying Web Application Security policy templates.

Adopt a DevSecOps Approach.Effective website security requires design effort across the whole of the website: in your web application, the configuration of the web server, your policies for . W3C's Web Application Security Working Group is developing the specification's next iteration, Content Security Policy Level 3.
Application Security Best Practices Checklist 2023
Get Demo Aqua .Application security refers to the process of identifying and repairing vulnerabilities in application software—from development to deployment—to prevent unauthorized access, modification, or misuse.A Content Security Policy (CSP) is a security feature used to help protect websites and web apps from clickjacking, cross-site scripting (XSS), and other .Creating a robust application security policy requires a fusion of expertise, insights, and strategic planning.

It is a broad discipline, but its ultimate aims are keeping web applications .
Découvrez pourquoi la . Created by the collaborative efforts of cybersecurity professionals and . Unlike a textbook, the Academy is constantly . Some of it is non-sensitive, for example the copy shown on the public pages.
Deep Dive
There are a few types of web application security testing - static (SAST), dynamic (DAST), and SCA (Software Composition Analysis).Colorado Springs, CO, April 22, 2024 – OWASP is thrilled to announce the addition of Starr Brown to the OWASP Foundation team. Web application security isn't something to be complacent about. It addresses not only minor .
Content Security Policy (CSP)
Created by the collaborative efforts of cybersecurity professionals and dedicated .

Examples of these tools are Ruby's Brakeman or Python's Bandit. La nouvelle liste, dont la dernière actualisation .
Security on the web
In the Policy group of the ribbon, click User Policy. Risk Assessment. Let's navigate the process of formulating a policy tailored to your organization's unique landscape.15 Application Security Best Practices.The mission of the Web Application Security Working Group is to develop security and policy mechanisms to improve the security of Web Applications, and enable secure . However, all the techniques we will use in this article are compatible with most major browsers. Generic Web Application Security policy templates.Application security best practices help uncover vulnerabilities before attackers can use them to breach networks and data.Up-to-the-minute learning resources.Apprenez à équilibrer la sécurité et la convivialité dans le développement d’applications Web en tant que développeur Web back-end.Your Content Security Policy will grow and change as your web application grows too.The WSTG is a comprehensive guide to testing the security of web applications and web services.La sécurité d'un site internet ou d'une application web est essentielle. Be Aware of Your Own Assets. It's also important to consider application data .
Web Application Security Policy
What is an application security policy? An application security policy establishes acceptable security and protection boundaries within which application developers .The SWAT Checklist provides an easy to reference set of best practices that raise awareness and help development teams create more secure applications. Instead of touch-and-go enforcement, strive for an incremental approach. 2 contributeurs.Overall presence ratio over time.Le projet de sécurité des API de l' OWASP réactualise son Top 10 relatif aux risques de sécurité des API pour 2023. The mission of the Web Application Security Working Group is to develop security and policy mechanisms to improve the security of Web Applications, and enable secure cross-origin communication.Application security controls are steps assigned to developers to implement security standards, which are rules for applying security policy boundaries to application code. Implement a Secure SDLC Management Process.Content Security Policy is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross Site Scripting and data injection attacks. If one of more of them prove useful, you can propose including them in a version of CSP by sending an email to public-webappsec.Unified Cloud Native Application Protection Platform (CNAPP) With Tenable Cloud Security you can easily ramp up security across all your AWS, Azure and GCP .
La sécurité d'un site Web
Attack surface refers to all the entry points and vulnerabilities in a web application that attackers can exploit. To follow the discussion around these upcoming features, refer to the public-webappsec@ mailing list archives. This charter has been replaced by a newer version. CSP has support in all major browsers, but as with any new web feature, it takes time for the browsers to catch up. Manage and create policy templates. In 2017, only 1. EU sanctions do not impact food security, and only cover bilateral trade between .Open Web Application Security Project® Foundation (OWASP), a non-profit organization that releases resources promoting application security, gives another framework that serves as a de facto standard for proactive . The template differences include functionality such as Blocking or Transparent mode, Manual or Automatic learning of entities (file types, URLs, parameters, cookies, and so on), and .














