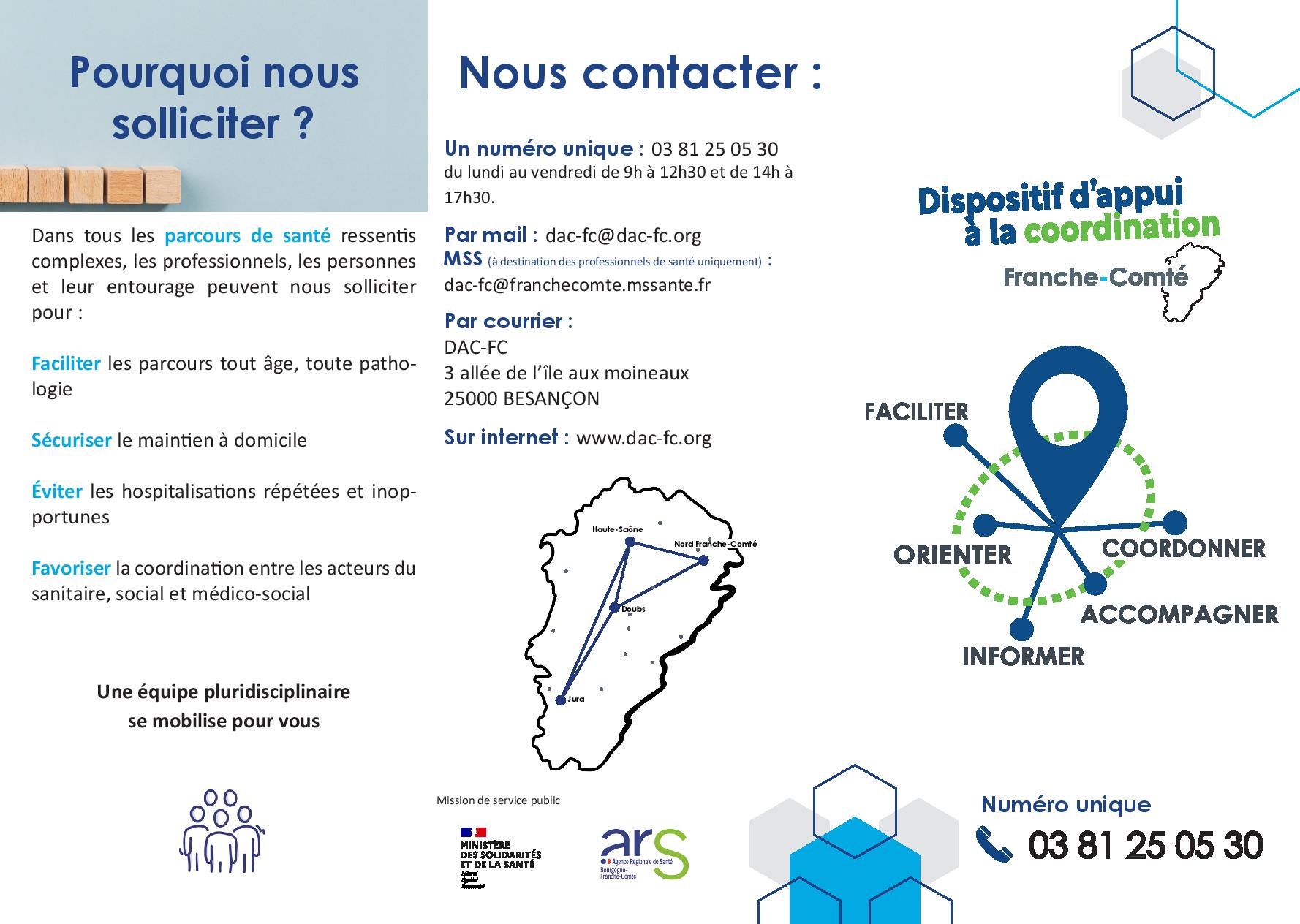
What is trojan horse

Trojan Horse Facts for Kids. Following the same analogy, a Trojan is a malicious program a hacker will use to break into a computer. The Trojan horse was a sly trick the ancient Greeks used to infiltrate their troops in Troy to ultimately conquer the city.A Trojan or Trojan horse is a variety of malware that disguises itself as something you want in order to trick you into letting it through your defenses.Un cheval de Troie ( Trojan horse en anglais) est un type de logiciel malveillant, qui ne doit pas être confondu avec les virus ou autres parasites. The horse was built by Epeius, a .com14 Different Types of Computer Viruses [As Of 2024] - .Trojan horse (or “Trojan”) is a broad term describing malicious software that uses a disguise to hide its true purpose. Learn how Trojans work, what types of Trojan .Trojan horse, huge hollow wooden horse constructed by the Greeks to gain entrance into Troy during the Trojan War. Once installed, Trojans can . The end of the war came with one final plan.In computing, a Trojan horse is a program downloaded and installed on a computer that appears harmless, but is, in fact, malicious. Un virus est un .orgWhat is the Difference Between Viruses, Worms and Trojan .A Trojan Horse is a malicious program that pretends to be harmless to trick users into installing it.
Qu’est-ce qu’un Trojan et comment s’en protéger ?
Les gens pensent parfois aux chevaux de Troie comme étant des virus ou des vers, mais ils ne sont ni l'un ni l'autre.There are many different types of harmful Trojan horses. ‘after Homer’), an epic poem by Quintus of Smyrna.
Overview
Cheval de Troie : de quoi s'agit-il ?
Just as the original Trojan horse deceived the people of Troy, so does the computer Trojan . Once inside, some trojans sit idly on your computer and wait for further instructions from its host hacker, but others begin their malicious .‘Most Dangerous Trojan Virus Ever’ Steals Over $1 Milliondigitaltrends.

Qu’appelle-t-on un Trojan et comment s’en protéger ? S’il existe plusieurs types de Trojans ou chevaux de Troie, tous .Today, the phrase “Trojan Horse” is defined as, “Someone or something that is used to hide what is true or real in order to trick or harm an enemy.A Trojan horse, Trojan malware, or simply a Trojan is a type of malware.comDifference between Virus and Trojan Horse - GeeksforGeeksgeeksforgeeks. Once installed, Trojans can perform various malicious activities such as stealing sensitive data, monitoring user activity, and providing unauthorised remote access for cybercriminals.
Manquant :
trojan horse The perpetrators then demand a ransom payment in exchange for restoring your computer’s performance or unlocking the blocked data. 27/10/2023.TROJAN HORSE definition and meaning

To infiltrate a victim’s device, this malware category relies on other means, such as drive-by-downloads, exploitation . The Trojan Horse was used in the Trojan War.
What is a Trojan Horse?
To infiltrate a victim’s device, this malware category relies on other means, such as drive-by-downloads, exploitation of .The company vowed Wednesday to take legal action against the legislation, suggesting it will file a lawsuit on the grounds that a potential ban could violate its users’ .When the horse's belly opened at night it was too late.Trojan horse: [noun] someone or something intended to defeat or subvert from within usually by deceptive means.The Trojan Horse & Victory.
The Greek Myth of Odysseus and the Trojan Horse
Trojan horse definition: 1. There are a wide variety of Trojan viruses on the Internet landscape that can perform an array of tasks.A Trojan horse is a malicious software that hides its true purpose and infiltrates a device using various techniques. Le cheval de Troie est un logiciel . Once installed, Trojans can perform various malicious activities such as stealing sensitive data, monitoring user activity, and providing unauthorized remote access for cybercriminals. The term was coined from the Greek myth of the wooden horse that was used to sneak into the city of Troy.A Trojan horse virus is a malware that disguises as a legitimate program and performs malicious actions on a computer. They hid soldiers inside the wooden horse.Free Trojan Scanner and Removal Tool | Trojan Remover .
What is a trojan horse virus and how does it work?
45 percent of all malware, 1 which comes as no surprise, given the unique traits of a Trojan.comRecommandé pour vous en fonction de ce qui est populaire • Avis
Détecter un cheval de Troie, comment l'éliminer ?
To infiltrate a device, a Trojan presents itself as legitimate software, but hidden beneath its seemingly harmless exterior are malicious codes that .Qu'est-ce qu'un Cheval de Troie ?
Trojan horse (computing)
A Trojan Horse, or simply Trojan, is a type of malware that disguises itself as legitimate software in order to gain access to a computer system.
How this tricky malware works
Trojan horse (or “Trojan”) is a broad term describing malicious software that uses a disguise to hide its true purpose. A Trojan horse is a malicious code that can steal, damage, or control your .Often disguised as legitimate software, a Trojan horse is a type of malicious software (malware) designed to provide unauthorized, remote access to a user’s computer.
What is a Trojan Horse?
Learn what a Trojan horse is, how it works, and what types of Trojan viruses exist. A Trojan horse, also known simply as a Trojan, is a type of malware that is often disguised as legitimate software.Un cheval de Troie (Trojan horse en anglais) est un type de logiciel malveillant, qui ne doit pas être confondu avec les virus ou autres parasites. However, a trojan .In technology, Trojan Horse is a type of malware that pretends to be legitimate software or code.com4 Ways to Remove Trojan Horse Malware From Windows . Odysseus devised a new ruse—a giant hollow wooden horse, an animal that was sacred to the Trojans.Like its namesake, Trojan horse attacks (or simply “Trojans”) in computing are defined as a type of malware that use deception and social engineering to trick unsuspecting users .
Trojan Horse Virus
At night, the Greek soldiers came out. This malware targets specific data, restricting your ability to access it. Trojans are hard to detect, even if you’re extra . Thousands of years later, the myth of the Trojan horse still lives on, albeit today in an unflattering connotation.
The Trojan Horse in Greek mytholgy
In the Posthomerica, Odysseus comes up with the idea of building a wooden horse .
Types and How to Remove it
comWhat is Trojan Horse malware and how can you avoid it? The fullest account of the Trojan Horse found in an ancient text is in a Greek epic poem.Trojan-Ransomware is a malicious software that infiltrates your computer, encrypting critical data.

It can also disguise itself as authentic files attached to emails.A trojan horse virus is a type of malware that sneaks into your computer through seemingly safe messages or software. The earliest known depiction of the Trojan Horse, from the Mykonos vase c. It’s a famous tale from ancient Greece.Trojan horse viruses are a very common hacker tactic in part because of how they work. Namun, tidak seperti virus, virus tidak dapat mereplikasi atau menginfeksi file sendiri.Myth of the Trojan Horse: plot summary.Trojan viruses are a type of malware that invade your computer disguised as real, operational programs. This malware works when a user downloads the executable file (. Thousands of years later, the myth of the Trojan . However, unlike a virus, it is neither able to replicate nor infect files on its own.Defining the Trojan Horse. Similarly, Trojans are designed to deceive users into loading and executing them on their systems.Prevention & Removal.Today, the main source for the Trojan War is the Iliad by the Greek poet Homer, but this epic poem ends prior to the events linked with the Trojan Horse, although Homer does make mention of the Wooden Horse in the .A Trojan is a sneaky type of malware that infiltrates devices by camouflaging as a harmless program. It can steal your passwords, lock files, . They brought the horse inside their city. Unexpected changes to computer settings .Trojan horses: https://www. Most Trojans are typically . It may appear to offer free games or music, or suggest you won something or can get a big discount. Le cheval de Troie est un logiciel en apparence légitime, mais qui contient une fonctionnalité malveillante.

Learn how to detect and remove Trojan horses from .comRecommandé pour vous en fonction de ce qui est populaire • Avis
Is it a virus or is it malware?
A Trojan is a malicious program that disguises itself as something harmless to trick you into installing it.Comment définir les chevaux de Troie. The war involved several more exciting episodes including Achilles' fight with and killing of the Ethiopian King Memnon and the Amazon Penthesilea who both came to the aid of the Trojans.” This meaning comes from the original story from Greek mythology. They'll build a wooden horse and leave it outside the gates of Troy as an offering to the goddess Athena, while the Greek army pretends to leave . Also called: the Wooden Horse Greek mythology. No, not Homer’s Iliad, nor yet the Odyssey, but instead the Posthomerica (i. Learn how Trojans work, what they do, and how to detect and remove them with AVG AntiVirus. Once a trojan is inside your system, it can perform destructive actions before you even know it’s there.The other loose horses from the Household Cavalry, the ceremonial guard of the monarch and a feature of state functions in London, are named Trojan and . It makes up approximately 51.What is a Trojan Horse? Borrowed from the story of the wooden horse used to trick the defenders of Troy into sneaking soldiers into their city, a Trojan Horse hides malware in what appears to be a normal file.A Trojan Horse is a delivery mechanism for viruses and other types of malware. a person or thing that joins and deceives a group or organization in order to attack it from the.