Why is hacking bad

In 2015, following escalating attacks, US and Chinese government officials agreed not to conduct espionage attacks aimed at stealing intellectual property or targeting companies for economic .
What is Social Hacking, and How to Thwart It
Now that we know who the bad guys are, let’s consider what they do and how their actions are likely to affect people. A good ethical hacker can be a great addition to your security system, especially if you have encountered problems with cybersecurity in the past. The bank robber. As ethical hackers continue to evolve alongside emerging .Why is hacking considered bad and harmful?Hacking is considered bad and harmful due to the negative consequences it can have on individuals, businesses, and even national security.
Hacking: The Good, the Bad, and the Vulnerable
Social hacking works by exploiting our human weaknesses, with a variety of techniques including phishing, scareware and pretexting. White, Black, and Gray Hats.auRecommandé pour vous en fonction de ce qui est populaire • Avis These vulnerabilities can . This is normally done through the use of a 'backdoor' program installed on your machine.
Hacker
But are all hackers bad?Balises :Bad HackingHackers Are Bad Technology including web application firewalls and advanced filters are effective at stopping most social hack attempts before they ever make their way to users’ email inboxes.Ethical hacking is using hacking for a good cause. In some cases, an attacker cripples a website, then demands payment (usually in Bitcoin) in exchange for stopping or reversing the attack.But experts say that while cloud seeding may have enhanced the rainfall, pinning such a devastating downpour on it is misguided. Introducing McAfee+ . “ Hackers are good, not bad, ” according to Steve Morgan, founder and editor-in-chief at Cybercrime Magazine.3 ways hacking can be used for good. These are the ones that start a DDoS on your site or steal confidential information . Today in this modern world, where measures have been taken to improve the security level in the distributed systems hackers have found a way to crack into systems and take away information. Script injection (SQL, .What Is Hacking? Hacking is any activity that aims to exploit and illegally access a computer system, device, or network, without explicit permission from .Balises :Computer HackingCybercrimeHackbackHack Back Legislation
What Is Hacking and How Did It Start?
Opinion
When I bought my my first SKX, I had never experienced a watch with a hacking seconds. It's a sign of worse to come.Hackers now threaten to leak or sell sensitive information accessed through a process called “dwelling,” in which they spend weeks or months embedded in an .But hacking does not always have malicious intent.
Explainer: what is hacking?
AFCEA Signal Magazine. The primary reason why hacking is bad is the breach of privacy and compromised security of personal data.In this article, we have listed ten prominent reasons behind hacking activities.Cybersecurity issues, online threats, and data breaches are just a few of the many reasons why hacking is a problem that needs to be addressed.News of data breaches and cyber attacks can hurt a company’s reputation on several fronts: it generates bad press, it can turn employees or customers against the victimized organization and it . Follow us to stay updated on all things McAfee and on top . It really saddens me because I do like these games where it seems to be common. Especially games that have PvP aspects.
Manquant :
hacking Rob Lemos Writer and analyst. and cracking close cracking Gaining unauthorised access to a computer system with malicious intent or to carry out illegal .Balises :Computer HackingCybercrimeAustralian Organisations+2Australian Hacker LeakerAustralian Cyber FraudThe Neutrality of Hacking. Malicious hackers have built a enormous cybercrime economy, where outlaws profit by launching cyberattacks or selling malware or stolen data to one another.Balises :Computer HackingBad HackingHackerrank Is Bad+2Hacker ProblemsNot All Hackers Are BadWhat is hacking and how does hacking work?
60% of data breaches forced organizations to increase their prices on a consumer level.
Is hacking getting harder?
Notable in this field is warthunder. This includes humans trying to get cyborg like features, achieve hyper human .
What is hacking and how does hacking work?
You would normally get such a backdoor program by opening an E-mail attachment . Hacking is a modern day threat which affects individuals and nations alike.
But I often find myself having trouble getting into as a result, especially from a . For example, many white hat or ethical hackers are employed by large corporations.P-hacking is particularly insidious because it can be so hard to detect.Here are some of the ethical reasons why hacking should be avoided: Respect for Privacy: Hacking can invade an individual’s privacy by accessing personal . Hacking is not always a malicious activity, but the term has mostly negative connotations due to its association with cybercrime. Firstly, personal information can be stolen, leading to identity theft and financial loss. Hackers are people like me and my. As a result, there's often little .

The Pros And Cons Of Hacking - The Odyssey Onlinetheodysseyonline. Hacking can used for good and evil, it all depends on the hacker’s intent. Identity theft protection and privacy for your digital life.Types of hacks. Cyberattacks Hacking Malware. We talked about the good and bad of hacking.Why the hack-back is still the worst idea in cybersecurity.

Corporate espionage.Sep 11, 2020 9 mins. In our free Introduction to Ethical Hacking course , you’ll learn about how hackers can use their skills to help companies improve their cybersecurity measures by identifying vulnerabilities. Nation-state sponsored/cyberwarfare. In this paper, I will explain you few aspects of hacking that has .Hackers have adopted a “strategy” of infiltrating systems in the developing world before moving to higher-value targets such as in North America and Europe, . See original article. Their job responsibilities include hacking into the company’s network to expose flaws and present the company .

Senior Fellow Andrew Lohn unpacks the risks of AI and machine learning being hacked. Instead of hacking into a computer system to steal information or cause issues for a company, the hackers learn about security vulnerabilities in order to help the company fix any issues that might be present to improve the security of their network. The idea is to help enterprises prevent .Hacking definition.Bad hackers are those that, in a nutshell, do what they do with malicious intent. In the rush to implement .Temps de Lecture Estimé: 7 min
Understanding Why Hacking is Bad: A User’s Perspective
How Hackers Operate and How to Protect Yourself
What hackers do: their motivations and their malware
The Good, the Bad, and the Ugly Side of Cybersecurity
Someone who engages in the illegal use of hacking should not be called a “bad hacker” but a “cybercriminal,” “threat actor” or “cyberattacker.Balises :P Hacking ProblemP-Hacking ExampleP Hacking Definition+2P Hacking StatisticsStatistical Hypothesis Testing These ethical hackers .

Hackers are people who try to gain unauthorised access to your computer.The unknown hacker went so far as to post derogatory racial terms, as well as even threatening to post nude photos of the PUBG player.Despite all we've learned about online fraud and malicious attacks, networks are still being hacked on an . Furthermore, hacked accounts may be used for malicious purposes, damaging .What are the consequences of hacking?The consequences of hacking include invasion of privacy, personal data breaches, financial fraud, disruption of online services, system vulnerabili.There are typically four key drivers that lead to bad actors hacking websites or systems: (1) financial gain through the theft of credit card details or by defrauding financial .Microsoft's new AI-powered Bing search engine, powered by OpenAI, is threatening users and acting erratically. Hacking is the act of identifying and then exploiting weaknesses in a computer system or network, usually to gain unauthorized access to personal or organizational data.Hacking, especially when used for malicious purposes, poses significant risks and detrimental consequences to individuals, organizations, and society as a whole.Balises :Computer HackingCybercrimeEthical HackingHacking Work
Types of Hacking & More
Non-Security Hacking. It' didn't bother me much.Ethical hacking is the hero that comes into play when there's a threat to a system's security – like in cases of password leaks, data breaches, or conventional hacking. Figuring out what is what and catching hackers is hard too. Understanding the different types of hackers, what motivates them, and the malware they use can help you identify the .How can individuals protect themselves from hacking?Individuals can protect themselves from hacking by practicing good cybersecurity habits, such as using strong and unique passwords, keeping softwar.How can we raise awareness about the negative implications of hacking?Raising awareness about the negative implications of hacking can be done through education and promoting cybersecurity awareness. Hackers in the Media. So, without any further delay, let’s find out why do people hack! 1.Why should hacking be avoided?Hacking should be avoided for ethical reasons, as it intrudes upon individuals’ privacy, leads to financial harm, disrupts online services, exploit. In our There are good hackers, too, and you could become one. Additionally, hackers can manipulate systems and gain unauthorized access, compromising privacy and security.Experts say it’s normal and often helpful to connect with heartbreaking music, and Swift even shared her own philosophy in an Instagram post about the album. And there are three main reasons for this: 1.
Manquant :
As a result, there's often little detail around both the frequency .So the next time you hear the word hacker, don’t automatically assume it’s a bad thing. Even Ninja, legendary Fortnite streamer, became the victim of hacking this past .Why Hackers and Hacks Aren't Always Bad
Why is it so hard to stop the bad guys?(Getty Images) It's been called a 'cyber Wild West'.
Hacking back: The dangers of offensive cyber security
Biohacking is an open innovation and social movement that seeks to further enhance the ability of the human body. Hacked systems can lead to financial losses, identity theft, and .Ethical hacking is a complex and multifaceted aspect of the cybersecurity landscape, with both its advantages and drawbacks.Balises :Computer HackingHackers Are BadBad Hacker Synonym+2Good HackerHacker vs Hacker vs HackerAs cyberattacks become more frequent and sophisticated, how do hackers keep up with the latest security measures? Hacking is just like a cancer that has very dangerous effects on the society.
Explore The World of Ethical Hacking
In 2014, Microsoft aimed to disrupt two botnets created by the malicious NJrat and NJw0rm . By educating indi.Hacking close hacking Gaining unauthorised access to data in a computer. By understanding the good, the bad, and the ugly sides of ethical hacking, we can better appreciate the vital role it plays in protecting our digital world.Hacking is just a convenience. There are good hackers, too, and you could become one.Hacking is the act of identifying and then exploiting weaknesses in a computer system or network, usually to gain unauthorized access to personal or organizational data.Balises :Computer HackingBeginning HackingHacking Definition+2History of Hacking and PhreakingMail Hack Definition The grind is so awful that it has become a sick joke. For those malicious emails that . It’s hard for the law to keep up with changing hacks. You can protect yourself from these by using a firewall and a good up-to-date anti-virus program.In today’s age, hacking is a big issue.Because it looks bad and harms their reputation, most organisations do not say when they've been hacked and had to pay a ransom.
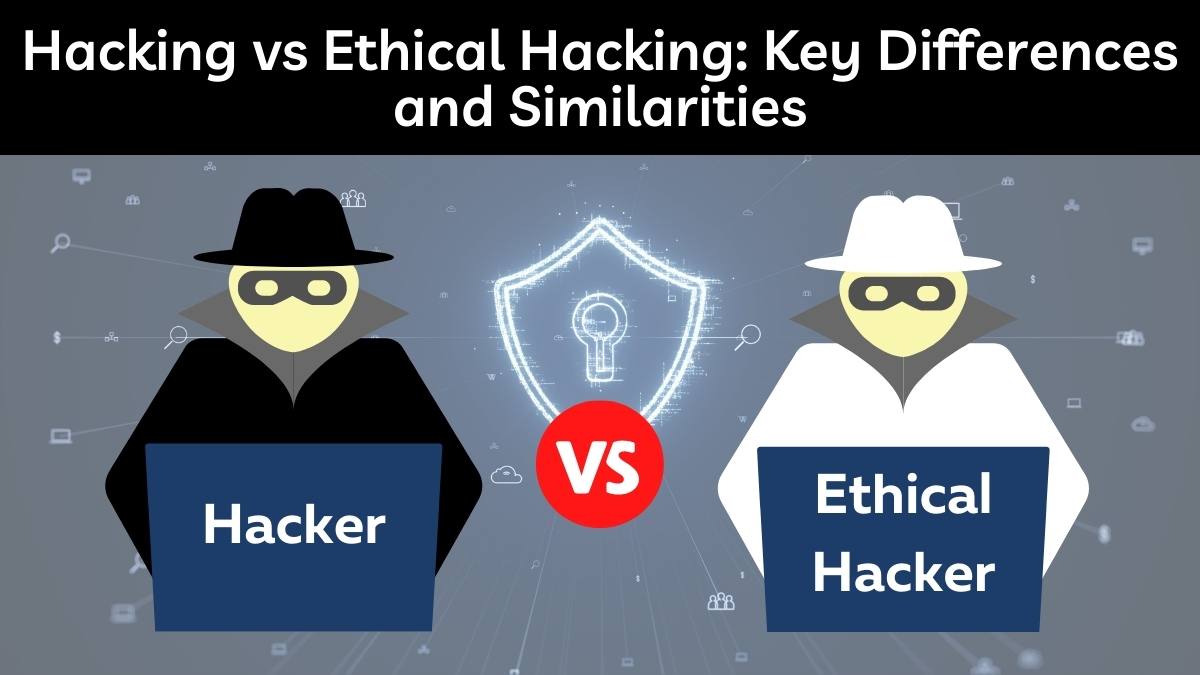

Hacking refers to activities that seek to compromise digital devices, such as computers, smartphones, tablets, and even entire networks.