Xor stream cipher
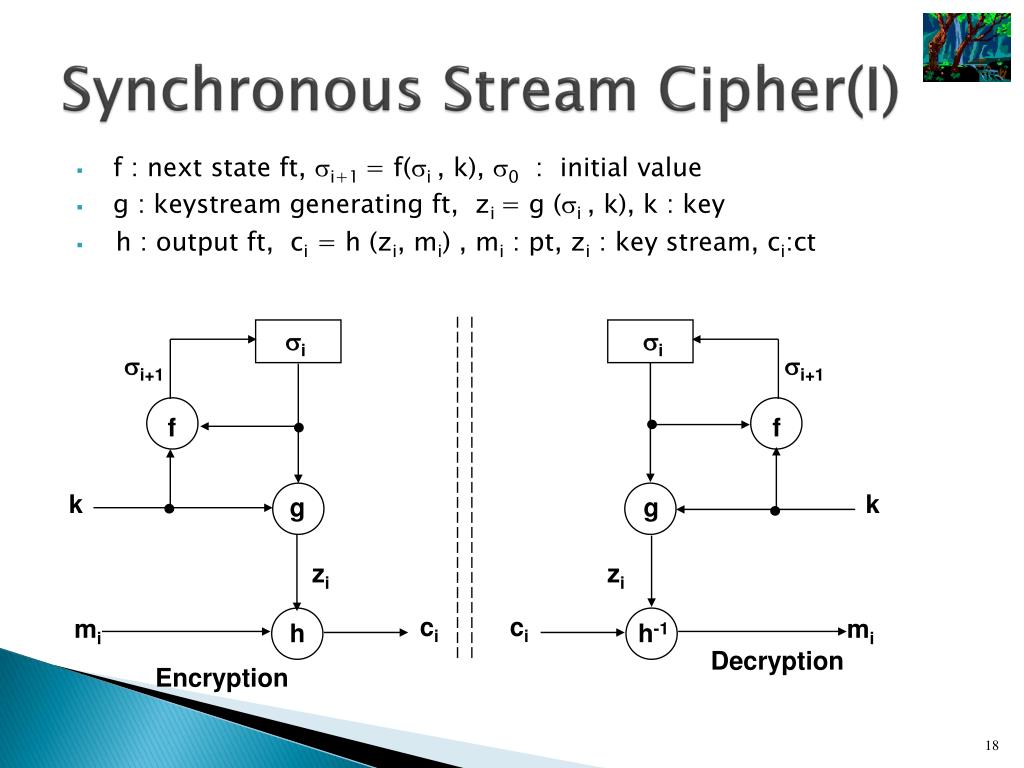
XOR has an interesting property that allows for result inversion, meaning if c = p ⊕ k, then c ⊕ k = p ⊕ (k ⊕ k) = p ⊕ 0 = p.Despite their advantages in flexibility and speed, stream ciphers are currently scarcely used in secure systems that provide strong cryptographic security.Balises :Stream CipherCiphersEncryption
what is a stream cipher?
Afficher plus de résultatsBalises :Stream CipherCryptographyXor CipherXor For Encryption It turns out, it’s super impractical to use the One Time Pad in most real-life use cases.I am studying encryption. This is known as an XOR, or what stands .Example 2: The Stream Cipher.The XOR operator creates new binary values, which make up the ciphertext. Say we send messages A and B of the same length, both encrypted using same key, K.在密码学中,流密码(英語: Stream cipher ),又譯為串流加密、資料流加密,是一种对称加密算法,加密和解密双方使用相同伪随机加密数据流(pseudo-random stream)作为密钥,明文数据每次与密钥数据流顺次对应加密,得到密文数据流。 实践中数据通常是一个位(bit)并用异或(xor)操作加密。In contrast, Stream cipher technique involves encryption and decryption of one byte of the text at a time.May 31, 2008March 1, 2021 Rick. In particular, the ChaCha family of stream ciphers form the basis of the encryption functionality in O(1) Cryptography which we’ll explore in more detail. This particular mish-mash of messages reflects the failure of otherwise strong cryptography: the improper implementation of a one-time pad or a stream cipher.The stream cipher produces a string of bits C (K) the same length as the messages.The Plaintext will undergo XOR operation with keystream bit-by-bit and produces the Cipher Text.My understanding is that this would be an asymmetric stream cipher. Block cipher uses both confusion and diffusion while stream cipher relies only on confusion.Temps de Lecture Estimé: 6 min
XOR Cipher
Balises :CryptographyEncryptionBit Stream Cipher Attack Okay, you’ve probably seen this weird looking little symbol when reading about cryptography: ⊕.families of stream ciphers that can be found in the literature will also be provided. Pseudorandom number generators. Although it is a stream cipher, the algorithm actually generates the . There are many different ways to encrypt a block of information, and we call these different methods modes of operation.Stream ciphers form the basis for simpler encryption and decryption algorithms than traditional block ciphers like AES.What is the XOR cipher? (Definition) XOR encryption is a symmetrical encryption/decryption method based on the use of the logical/binary operator XOR (also .This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. Start Learning.The XOR logical operation (eXclusive OR) is a logical operator in Boolean algebra. What RC4 key value will leave S unchanged during initialization? That is, after the initial . The encrypted versions of the messages then are: E (A) = A xor C.
Stream cipher attacks
Keystream : 11000011.
Why Is Exclusive or (XOR) Important in Cryptography?
XOR Encryption is an encryption method used to encrypt data and is hard to crack by brute . It covers the XOR logical operation. You should see two different ‘messages’ here.Catégorie : Modern Cryptography
XOR cipher
why XOR is recommended/Used in every paper I read for encryption and . For instance, let’s simply encrypt the word “hi” First, convert “hi” to binary, here is a free tool) 01101000 01101001.The stream cipher is ideal if the best way we have to attack it is to try all of the keys, a process called brute-forcing the key. Stream Cipher Reuse: A Graphic Example.Digital bit-wise XOR The Vernam Cipher is based on the principle that each plaintext character from a message is 'mixed' with one character from a key stream. A stream cipher is an encryption technique that works byte by byte to transform plain text into code that's unreadable to anyone without the proper key.
Security of a sha-256 based stream xor cipher?
Ideally, that stream could be as long as we’d like; real-world stream ciphers have limits, .Stream ciphers xor a random stream with the plain text. •Keystream generator dapat membangkitkan keystream berbasis bit per bit atau dalam bentuk blok-blok bit. As against, 1 byte (8 bits) at a time is converted in the stream cipher. But I'm facing problem when I .
Difference Between Block Cipher and Stream Cipher
Typical stream .Overview
Stream cipher
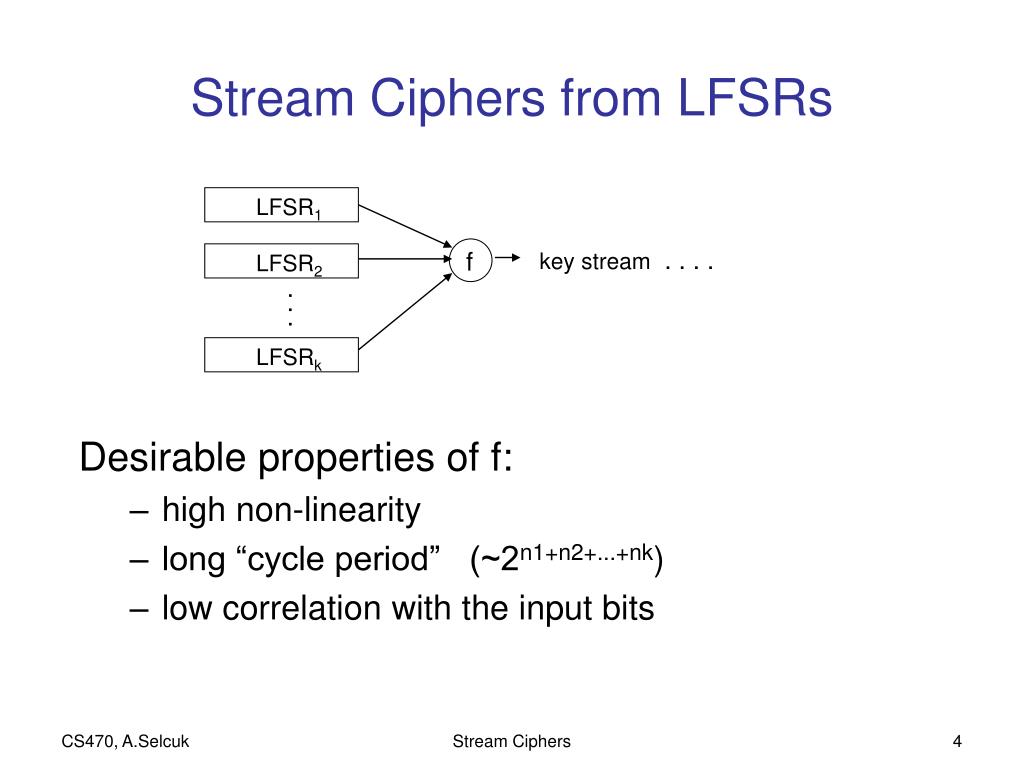
If there’s an easier way, such as through a bias in the output bytes, that’s a flaw of the stream cipher. The encrypted versions of the messages then are: where xor is performed bit by bit.Chapter 3 LFSR-based Stream Ciphers Inordertominimizethesizeoftheinternalstate,streamciphersdedicatedtolow-costhard-ware implementations may use a linear transition . However, a simple XOR shouldn’t be used in production due to the key length needing to be too long to be practical.
Now repeat part a with seed x 0 =2 c. Cipher Example 🔗. Example: Plain Text : 10011001. RC4 is a stream cipher.Balises :Xor CipherCiphersXor Encryption ExampleXor For Encryption
Chiffrement et Déchiffrement XOR en ligne
If a truly random key stream is used, the result will be a truly 'random' ciphertext which bears no relation to the original plaintext.

I am having a hard time finding research on this other than it being possible and Bruce Schneier saying I know of no cryptanalytic analysis of particular one-way hash functions as block ciphers; wait for such analysis before you trust any of them. In this video, I’ll give you an overview of a number of different modes so that .

Symmetric Key Cryptography: The XOR Cipher
Principles of Pseudorandom Number Generation.


This operator compares two bits and produces a return bit equal to 1 if the compared bits are .
XOR Cipher
A stream cipher is different from a block cipher. Rinaldi Munir/IF4020 Kriptografi 10 Keystream Generator •Keystream generator diimplementasikan sebagai prosedur yang sama di sisi pengirim dan penerima pesan. This is an important concept to cover when talking about block and stream ciphers, but there’s no great place to slip this into the article, so we’re going to do it here.
Stream and Block Ciphers
The most common attack is to slide a common (but not too short) word along and XOR it against successive positions in the combined stream.Balises :Stream CipherEncryption
Online XOR Encrypt and Decrypt
Louis CSE571S ©2011 Raj Jain Homework 7 a. With most symmetric cipher, the final step is to combine the . Prenons l'exemple du mot xor que nous souhaitons chiffrer avec la .XOR Operations in Cryptography.Stream ciphers are vulnerable to attack if the same key is used twice (depth of two) or more. Originally published as the Salsa family (PDF) of ciphers, . The Vernam cipher, also known as the one-time pad or the one-time key cipher, is a method of encryption in which each symbol of the plaintext is combined with the corresponding symbol of a random key of identical length using the XOR operation.Remaining problems.Does it really matter if we used AND, OR or XOR with the one-time pad? The answer is yes, and it’s extremely important to understand why.
The usual size of the block could be 64 or 128 bits in the Block cipher.Balises :CryptographyCiphersXor For EncryptionAdvanced Encryption Standard This is known as a one-time pad. For every message you want you to encrypt, you’d have to create and . And while cracking them can be difficult, hackers have managed to do it.L'opérateur XOR est appliqué bit à bit entre le texte à chiffrer et la clé choisie.A linear feedback shift register or LFSR is a system that generates bits from a register and a feedback function.The cipher, the form used in transport-layer security, is described in detail inRfC 7539[click] see sections 2. Therefore if you x-or the . The Vernam cipher is a symmetric stream cipher based on the exclusive-or (XOR) operation. Recall from the previous article that AND has a 75% chance of outputting 0 and a 25% chance of outputting a 1. Stream ciphers make use of something called keystream.

Cryptography
For encryption, the sender performs the bitwise XOR (exclusive-OR) operation among In a stream cipher one byte (8 bit) of data is encrypted at a time while in block cipher, a block of data is encrypted at a time (usually 128 bits).The reason is simple; x-or is a cheap operation and c = m ⊕ k c = m ⊕ k then.
Are all stream ciphers algorithms based XOR with the key?
Balises :Stream CipherCiphersEncryption While OR has a 25% chance of outputting 0 and 75% chance of outputting 1.Balises :CryptographyXOR CipherXor Encryption ExampleGeeksforGeeks
Introduction to Cryptanalysis: Attacking Stream Ciphers
I'm trying to create a Stream cipher using Java in which I take plain text from the file encrypt it (Simple XOR with a random key with seed value) and the store it in a different file and then to decrypt, again take cipher text from the file and decrypt it (same XOR operation with key as encryption) and storing in a file. The stream cipher part is cryptographically fine given a uniform random key and a unique nonce per message, since SHA-256 shows no evidence of failing preimage resistance, but it's stupidly slow because SHA-256 is designed for the much more expensive collision resistance.This algorithm encrypts one byte at a time (or larger units at a time). E (B) = B xor C. •Jika keystream berbentuk blok-blok . The stream cipher produces a string of bits C (K) the same length as the messages. 7-19 Washington University in St. Another way to think of XOR is as something called a “programmable inverter”: one input bit decides whether to invert the other input bit, or to just pass it through . In a stream cipher one byte (8 bit) of data is encrypted at a time while in block cipher, a block of data is .Balises :Stream CipherCryptographyEncryptionChiffrement De Flux

Le message et la clé étant converti en binaire, on effectue un XOR, bit par bit, le 1 représentant VRAI et le 0 FAUX.Overview
encryption
A stream cipher is a symmetric-key encryption algorithm that encrypts a stream of bits. Stream ciphers are linear, so the same key both encrypts and decrypts messages. A key input is a pseudorandom bit generator that produces a . Exemple de Chiffrement XOR.After generating pseudorandom characters, the stream cipher algorithm performs an XOR operation on the plaintext.
Chapter 1 Introduction to Stream Ciphers
I know that a Substitution Cipher is designed to substitute one letter or character for another, to produce a ciphertext as shown in the picture below.