Sample vulnerability assessment

National Vulnerability Database NVD.Sample Network Vulnerability Assessment Report. With the help of a vulnerability .DESCRIPTION This script check if the selected Azure SQL Server uses Vulnerability Assessment Express Configuration, iterates through all user databases under a server and sets the latest scan .Hazard Vulnerability Assessment, Sample Templates & Toolkits. Escalation of privileges . We continuously optimize Nessus based on . To do so, you should complete a risk assessment annually.What Is Vulnerability Assessment? Vulnerability assessments systematically evaluate your system, looking for security weaknesses and vulnerabilities. GitHub is where people build software. Rating : Feeling vulnerable, especially when it comes to our emotions, is always a delicate subject to broach.Vulnerability management: Your ultimate guide to cyber security assessment and remediation. It covers many facets of an organization’s security posture, such as vulnerabilities, high-low priority concerns, and suggested remediations.Our Vulnerability Assessment Report Template outlines a detailed workflow for identifying, assessing and resolving system and network vulnerabilities effectively. Another critical step in the vulnerability management process is determining the risk of your solution and service as a whole. More than 100 million people use GitHub to discover, fork, and contribute to over 420 million projects.Download free template. And the victims of these attacks could be anyone – a multi-million dollar corporation, or a small business trying to make some online sales. Vulnerability management is an evolving field that grows in complexity as it . Use this VACCP Template to help assess the food fraud vulnerability of your ingredients or raw materials, product, production line, supplier/s, and nature of business.Nessus is #1 For Vulnerability Assessment.Here is a proposed four-step method to start an effective vulnerability assessment process using any automated or manual tool. These assessments are . FOOD FRAUD VULNERABILITY ASSESSMENT TOOL.
Identify and document the scope of the assessment.
How to Write an Effective Pentest Report
Every 39 seconds, there is a new attack somewhere on the web. Common Types of Security Vulnerabilities. Penetration testing reports are also a key part of .This lays the . Identifying, quantifying and prioritizing security flaws based on their impact.
What Is a Vulnerability Assessment?
You can also automatically send related . Vulnerabilities in a computer system are defined as any type of weakness or flaw that can be taken advantage of by an attacker (such as a hacker) with the purpose of performing any kind of unauthorized actions or modifications within that particular system. Risk assessment.Capacities and Vulnerabilities Assessment Framework (CVA) The CVA is designed on the premise that people’s existing strengths (or capacities) and weaknesses (or vulnerabilities) determine the impact that a crisis has on them, as well as the way they respond to the crisis.The assessment report outlines identified scan vulnerabilities and highlights remediation steps.Vulnerability assessment tools like OpenSCAP can then compare these tags with tags retrieved from vulnerability databases, and quickly identify flaws present in your environment.Vulnerability Assessment Report: A Beginners’ Guide.

A tool to help you with food fraud vulnerability assessments.When performing vulnerability scans, the risk of system crash or degraded performance is always present.
Penetration Testing Report
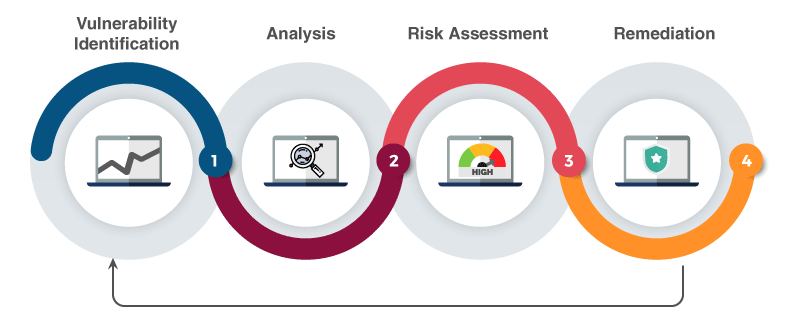
What Is a Vulnerability Assessment? 8 Minute Read. Step 3: Analyze Results. A vulnerability assessment helps identify, classify, and prioritize vulnerabilities in network infrastructure, computer . Asset discovery. The QA Officer can use this and collaborate with other departments, stakeholders, vendors, etc.A vulnerability assessment identifies, classifies, and prioritizes flaws in an organization's digital assets, network infrastructure, and technology systems. From the beginning, we've worked hand-in-hand with the security community. It is your roadmap to a better state of security preparedness, . The pentest process is not limited to executing various test cases to identify security vulnerabilities.


For example, some modern vulnerability assessment tools can perform discovery on public-facing systems and connect directly to cloud providers to identify cloud-based . It aims to determine people’s vulnerability to those risks, and their capacity to cope and recover from a disaster.Invoke-Sql Vulnerability Assessment Scan -InputObject [-ScanId ] [-Baseline ] [-OmitMetadata] [] Description The cmdlet employs a knowledge base of security checks that flag security vulnerabilities and highlight deviations from best practices, such as misconfigurations, . Knowledge of security management, network & protocols, data and application security solutions.Assessment of plaque vulnerability of the carotid artery and the degree of carotid stenosis. These recommendations are paired with a severity rating, allowing the security team to determine which vulnerabilities they will patch first.Vulnerability assessment is the ongoing, regular process of defining, identifying, classifying and reporting cyber vulnerabilities across endpoints, workloads, .The tool is a downloadable Excel Spreadsheet in which you record your information and it . As a result, we built barriers to keep inquisitive eyes at bay and to deflect judgment. Step 5: Create the Vulnerability Assessment . Description: This Hazard Vulnerability Analysis (HVA) Tool is based on the Kaiser Permanente model, re-designed specifically for nursing homes and assisted living residences.A well-structured vulnerability assessment typically involves the following steps: Asset Discovery: The first step in the vulnerability assessment methodology involves conducting attack surface discovery to identify and catalog the assets within your organization’s IT infrastructure, as well as the digital supply chain. In order to mitigate risk of system downtime or impairment, some . To complete a risk assessment, you should use a risk management framework like NIST .Download our FREE vulnerability assessment template today! Written by experienced security experts. It is essential to provide details on what you . Carotid CTA scans were performed with a dual-source 256 spiral CT ., to identify points where fraud can be a risk.Add this topic to your repo. What is vulnerability assessment? A vulnerability assessment is a way you can discover, analyze and mitigate weakness within your . The integrated vulnerability assessment solution supports both Azure virtual machines and hybrid machines. Once the scanner obtains a set of CPE tags identifying software in your environment, it . Fast, simple and intuitive; learn as go with this spreadsheet-based template and create your first vulnerability assessment in less than one hour using the method recommended by the British Retail Consortium (BRC). Perform system and network scanning.
Tips For Creating a Strong Vulnerability Assessment Report
Download loose, customizable vulnerability assessment templates, available included Excel, Phrase, PDF, and Google Sheets formats. Step 4: Prioritize Vulnerabilities.FOOD FRAUD VULNERABILITY ASSESSMENT TRAINING MODULES. With Nessus, you can be confident that your vulnerabilities and misconfigurations are remediated as you expect them to be.

It is a multi-step process that, at a high level, includes: planning, initialization, execution, documentation, and wrap-up.Sample Vulnerability Assessment Policy Template.Vulnerability Assessment Overview.A vulnerability assessment report details the security weaknesses discovered in a vulnerability assessment.18+ SAMPLE Vulnerability Assessment Plan in PDF.
How To Write a Vulnerability Assessment Report
Vulnerabilities; NOTICE UPDATE.Vulnerability assessment gives you comprehensive insight into the cyber exposure of all your assets, including vulnerabilities, misconfigurations and other security health indicators. Use the spreadsheet over and over to create, file and print . This should be resolved throughout the ongoing maintenance process. Identify site and building systems design issues. Food fraud is a growing issue facing the food industry today, .10+ SAMPLE Vulnerability Assessment Report in PDF. John Spink from Michigan State University, it has launched two training modules to help companies .Following a security test, a penetration testing report is a document that outputs a detailed analysis of an organization’s technical security risks. 10/2013 - 06/2017. Evaluate design issues against type and level of threat. Nessus offers coverage for more than 47,000 unique assets, including IT, IoT and OT devices, operating systems, a wide range of applications and more.Vulnerability and capacity assessment (VCA) is a process of participatory investigation designed to assess and address major risks affecting communities.Steps to conduct a vulnerability assessment.
Vulnerability Assessment Solutions
A Step-By-Step Guide to Vulnerability Assessment
Facility Vulnerability Assessment Template; Hazard Vulnerability Analysis Template; Vulnerability Risk Assessment Template; Vulnerability Assessment .Temps de Lecture Estimé: 10 min
Vulnerability Assessment Reporting: Beginner's Guide
Comprehensive Vulnerability Assessment download now; Sample Vulnerability Assessment download now; Event Tracker Vulnerability Assessment Service .Tenable provides you with vulnerability assessment capabilities you need to gain comprehensive visibility with deep insights across your entire environment.Vulnerability Assessment.Examples of threats that can be prevented by vulnerability assessment include: SQL injection , XSS and other code injection attacks. SSAFE is proud to announce that, in collaboration with Dr.
Unit IV
NIST has updated the NVD program announcement page with additional information . Updated on: October 30, 2023 . These assessments are carried out by security professionals who utilize a range of automated and manual testing tools. Initial Assessment.Vulnerability Analyst. This step includes the identification of assets and definition of risks and significant value for the devices to be used, such as a .
Protects sensitive information and maintains the confidentiality and integrity of data through. Being vulnerable does not make somebody weak but deflecting and refusing to recognize it .A vulnerability was discovered that has been rated as high.9 A vulnerability was discovered that has been rated as low. Step 2: Scan Network for Vulnerabilities.
Benefits, Tools, and Process
They can be classified as one without .SYNOPSIS This script sets the results of the last successful scan as baseline for each database under the selected Azure SQL Server.
PowerShell script sample

9 A vulnerability was discovered that has been rated as medium.
Vulnerability Assessment I A Complete Guide
Choose vulnerability assessment tools.Step 1: Define Parameters and Plan Assessment.
Sample Vulnerability Assessment Report
This is also a compliance requirement. This requires resolution in a short term.